
[11 January 2018] – [ ORIGINAL INVOICE MALWARE] – SUBJECT : [Invoice_0413103]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware link, and spread to email user with subject “Invoice_0413103”.
ASSOCIATED FILES:
RAR archive of the malware: [11 January 2018] – [Invoice] – 208 KB (212,992 bytes)
- Email : 1466-1514376931-528485.eml 6.30 KB (6,454 bytes)
- Malware Link Dropped File : Invoice_4202469.js 152 KB (155,648 bytes)
- Dropped file : OLKQFTD2.exe 13.7 KB (14,034 bytes)
THE EMAIL:
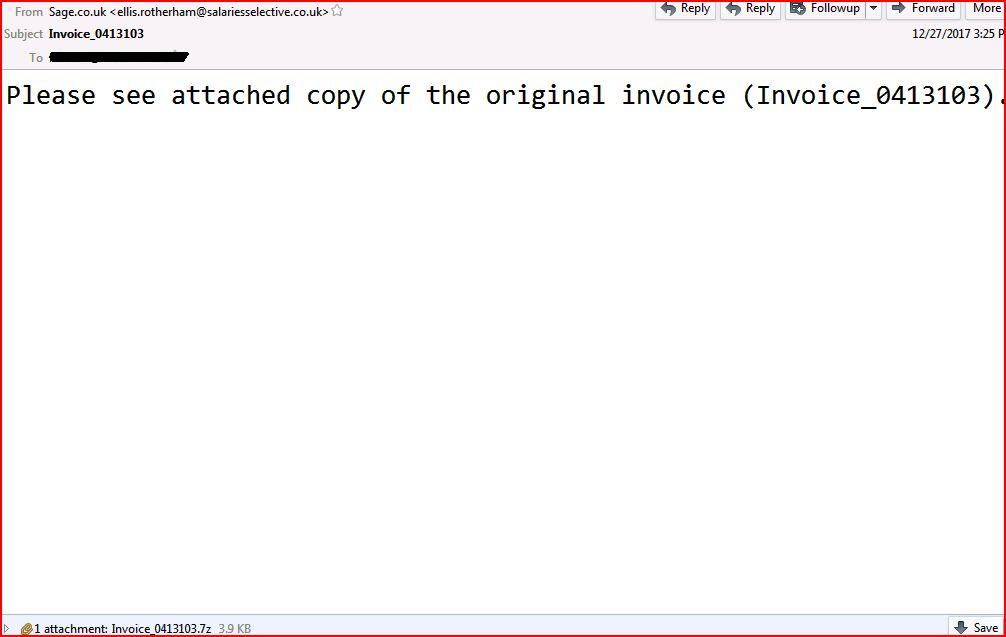
EMAIL DATA:Invoice_4202469.js
Received: from unknown (HELO ?203.135.26.134?) (203.135.26.134)
by 0 with SMTP; 27 Dec 2017 09:55:02 -0000
Received-SPF: unknown (0: domain at spf-trusted-fwd1.surgate.net does not designate permitted sender hosts).
Message-ID: <BE27D13D.3232578@salariesselective.co.uk>
Date: Wed, 27 Dec 2017 14:55:00 +0500
From: “Sage.co.uk” <ellis.rotherham@salariesselective.co.uk>
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:24.0) Gecko/20100101 Thunderbird/24.2.0
MIME-Version: 1.0
Subject: Invoice_0413103
PHISHING LINK – DROPPED FILE:
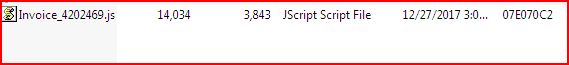
DROPPED FILE:
EXTRACTED FILE DETAILS FOR Invoice_4202469.js:
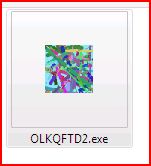
EXTRACTED FILE DETAILS FOR OLKQFTD2.exe:
File Name : OLKQFTD2.exe 13.7 KB (14,034 bytes)
MD5 hash : 71241C4F24281591D09DFB9BE763A256
SHA1 hash : 7615BDD3F422AF6C9CE408ABC15E9CB75E21D368
SHA256 hash : D2E6FC54B6DE406E71C48F61B040B904C866959415B4E90EE6088380AFE4C895
File Name : Invoice_4202469.js
MD5 hash : 9244C3E24AB4B3AB0D77342F964CD5D5
SHA1 hash : 519E0E365882EA1FF2E7EB55B8FE9779D720FF91
SHA256 hash : 3AC341B6E44DCE130A3CAEFBA097E1FFAE4D3DE7014FF5A3AD46F2F58AFF0054
TRAFFIC:
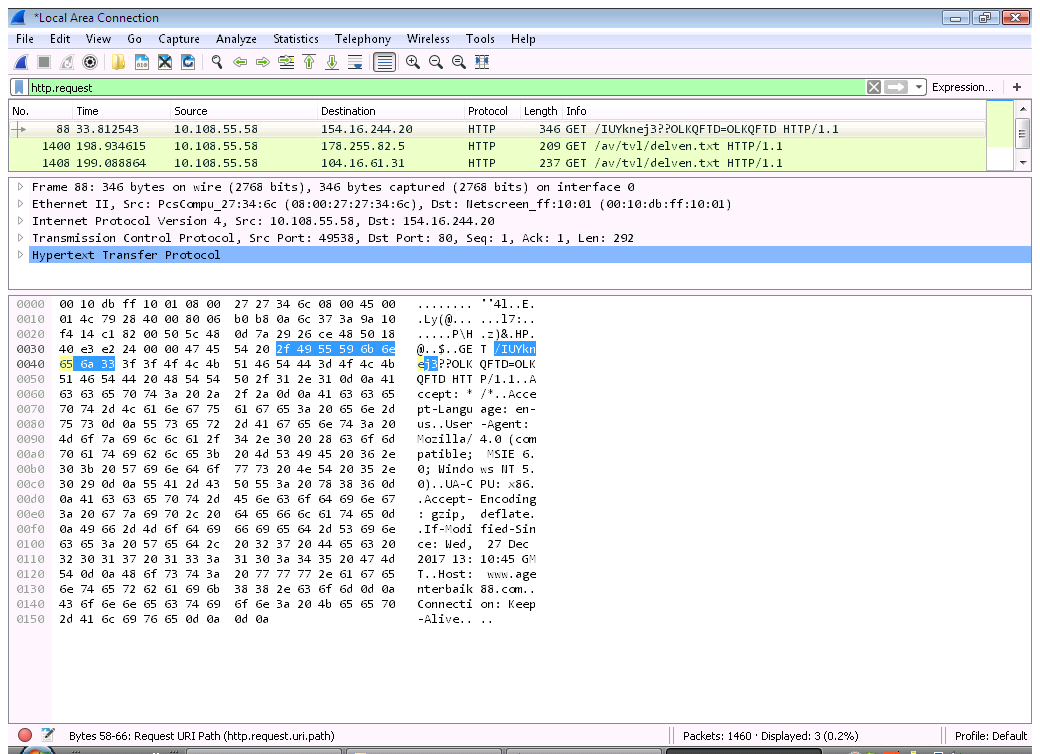
ASSOCIATED URLS:
- 88 33.812543 10.108.55.58 154.16.244.20 HTTP 346 GET /IUYknej3??OLKQFTD=OLKQFTD HTTP/1.1
- 1400 198.934615 10.108.55.58 178.255.82.5 HTTP 209 GET /av/tvl/delven.txt HTTP/1.1
- 1408 199.088864 10.108.55.58 104.16.61.31 HTTP 237 GET /av/tvl/delven.txt HTTP/1.1
VALKYRIE FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=7615bdd3f422af6c9ce408abc15e9cb75e21d368
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
RAR archive of the malware: [11 January 2018] – [Invoice] – 208 KB (212,992 bytes)
- Email : 1466-1514376931-528485.eml 6.30 KB (6,454 bytes)
- Malware Link Dropped File : Invoice_4202469.js 152 KB (155,648 bytes)
- Dropped file : OLKQFTD2.exe 13.7 KB (14,034 bytes)
related source by – Uber Clone
