
[07 September 2017] – [Locky Ransomware Spreading via True Telecom] – SUBJECT : [64809565 – True Telecom Invoice for August 2017]
Comodo Threat Research Labs (CTRL) identified a new MalSpam email, that contains a Compressed Malware file which is used by the Attacker to Download Locky Ransomware from Command & Control Server and Compromise the Victims Machine, and spread to email user with subject “64809565 – True Telecom Invoice for August 2017”.
ASSOCIATED FILES:
ZIP archive of the malware: [07 September 2017] – [Locky Ransomware Spreading via True Telecom] – 338 KB (3,46,470 bytes)
- 19200-1504542929-855360.eml 405 KB (4,15,215 bytes)
- SCNMSG00002188.vbs 10.6 KB (10,871 bytes)
- wireshark for new locky.pcapng 370 KB (3,79,624 bytes)
THE EMAIL:
Initially, Victims Received an Email from True Telecom with attached rar File that contain Executable VB Script.
Email Contact Says , “To be able to read your invoice file you will require the Adobe Acrobat PDF viewer”.
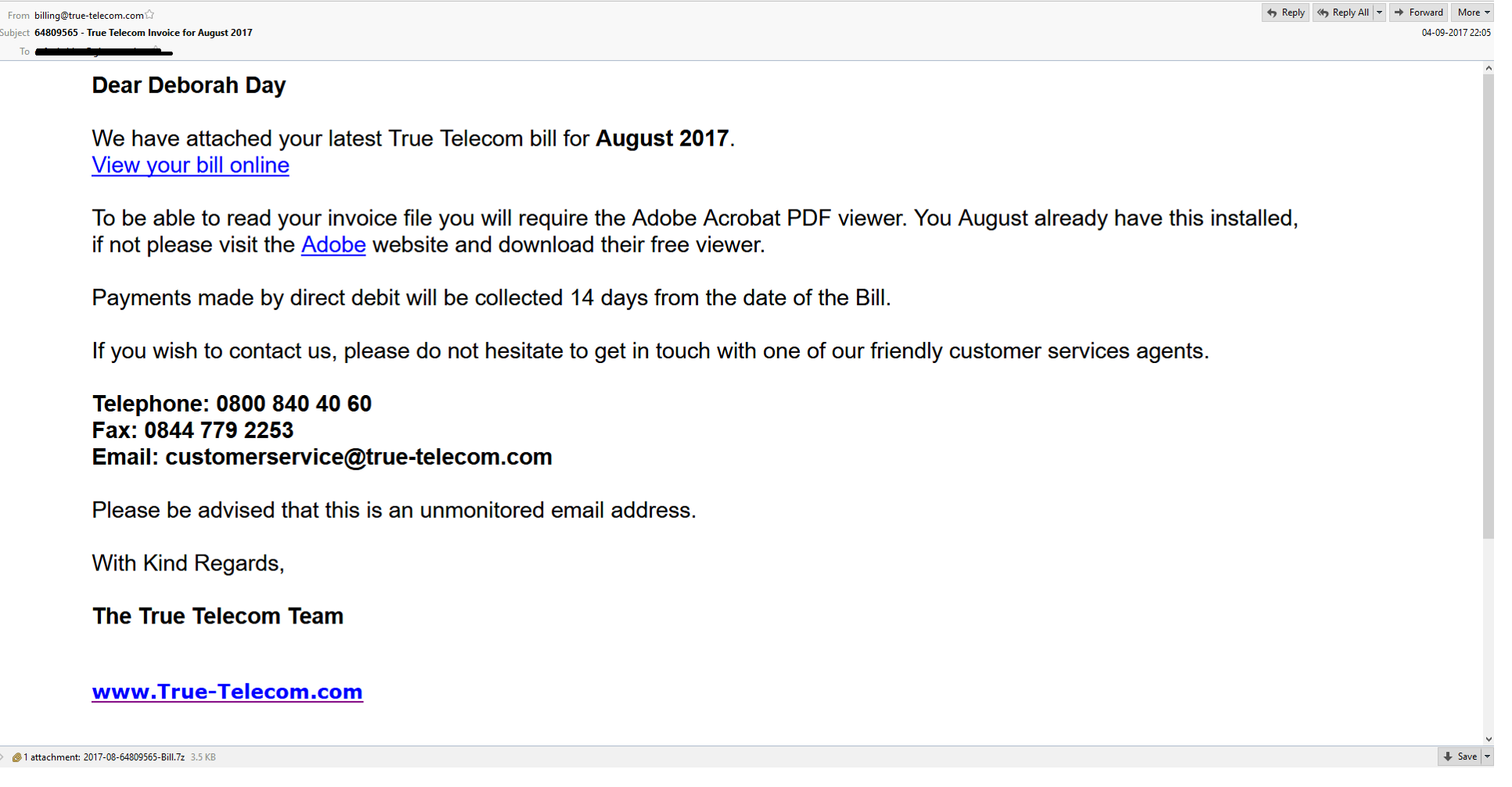
EMAIL DATA:
- From: billing@true-telecom.com
- Subject: 64809565 – True Telecom Invoice for August 2017
- Content-Type: multipart/mixed; boundary=”=_NextPart_2rcPRHxWxvPdBJXpRxgABJc”;
- MIME-Version: 1.0
- Date: Mon, 04 Sep 2017 23:35:25 +0700
- Message-ID: <AFF-MAI-SVC02IZfSp34127639b@giresun.edu.tr>
THE ATTACHMENT:
Email Attachment Contain Executable VB Script that is used to communicate with Command & Control server to Download Original Ransomware File into Victims computer.
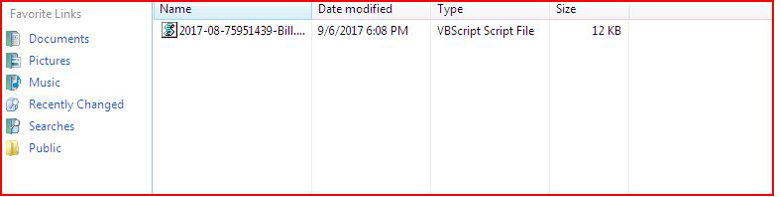
DROPPED FILE:
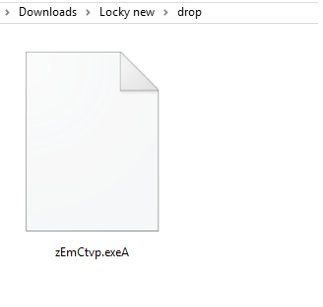
EXTRACTED FILE DETAILS FOR MALWARE :
C&C Server Link From Code
![]()
File Name :2017-08-50050811-Bill.7z 3.45 KB (3,537 bytes)
MD5 :5D6A7B93309B599237DBED9471372F55
SHA1 :E2F2A89239CC2D8056D9F64578B4D80FD6403EBE
SHA256 :6ECAC39D4F522F00AAB757B734D1E8F08F10538671788603FE58196BF2B99D59
File Name :zEmCtvp.exeA 603 KB (6,17,472 bytes)
MD5 :869DEBB0E6580AC74DD321FBEFB6A2ED
SHA1 :0CA83440024A645351818A6A2F13D7D323B555D0
SHA256 :4CDC0E6CD4C8D020B1D90C49352C9F4E7B279248B6A851CAD6DD6F600B55920F
TRAFFIC:
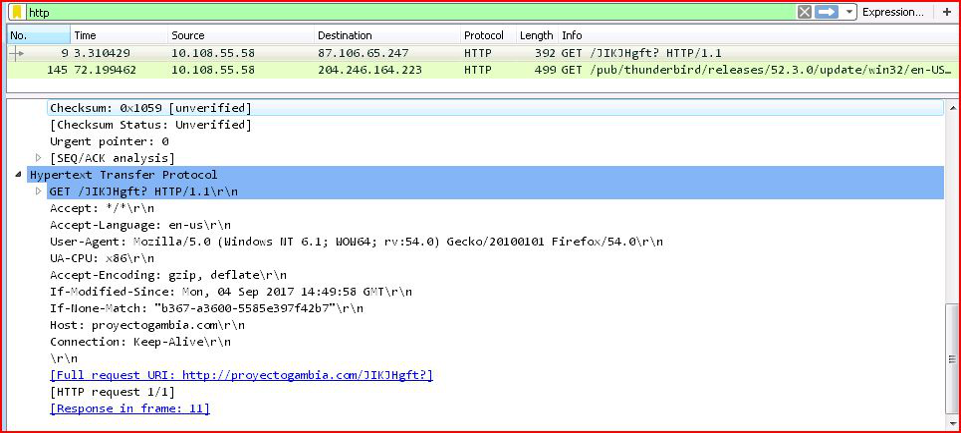
ASSOCIATED URLS:
- proyectogambia.com/JIKJHgft?#naturofind.org/p66/JIKJHgft#geolearner.com/JIKJHgft?”, “
- Source – 10.108.55.58 Destination – 87.186.65.247
- 9 3.310429 10.108.55.58 87.106.65.247 HTTP 392 GET /JIKJHgft? HTTP/1.1
- 493 72.449080 204.246.164.223 10.108.55.58 HTTP 378 HTTP/1.1 206 Partial Content (application/octet-stream)
FINAL NOTES:
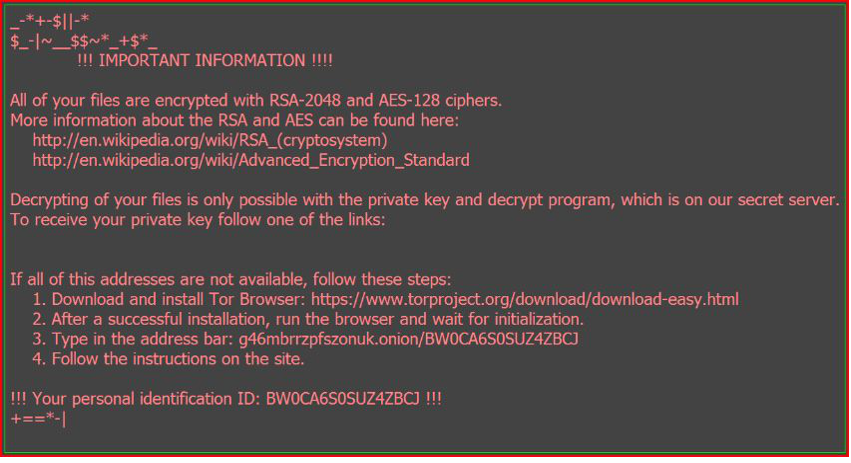
ASSOCIATED FILES:
ZIP archive of the malware: [07 September 2017] – [Locky Ransomware Spreading via True Telecom] – 338 KB (3,46,470 bytes)
- 19200-1504542929-855360.eml 405 KB (4,15,215 bytes))
- SCNMSG00002188.vbs 10.6 KB (10,871 bytes)
- wireshark for new locky. pcapng 370 KB (3,79,624 bytes)
related source by – Uber Clone
