
[10 July 2017] – [ EMPTY SUBJECT MALWARE]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware link, and spread to email user with Empty subject.
ASSOCIATED FILES:
RAR archive of the malware: [10 July 2017] – [Empty Subject Malware] – 352 KB (360,448 bytes)
-
Email : 37524-1499638651-514808 8.00KB(8,192 bytes)
-
Malware Link Dropped File : 1.dat 336 KB (344,064 bytes)
-
Dropped file : 27814.zip 8.00 KB (8,192 bytes)
THE EMAIL:
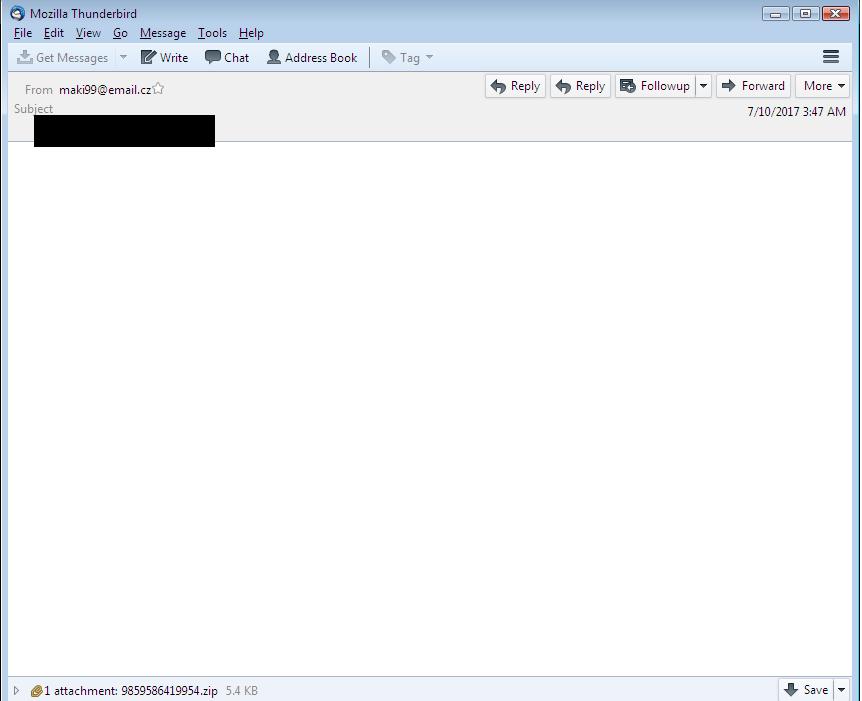
EMAIL DATA:
-
Received: from unknown (HELO asianet.co.th) (61.91.34.106) -
by 0 with SMTP; 9 Jul 2017 22:17:33 -0000 -
Received-SPF: unknown (0: domain at spf-trusted-fwd1.surgate.net does not designate permitted sender hosts) -
Content-Transfer-Encoding: base64 -
Subject: -
From: <maki99@email.cz> -
Date: Sun, 09 Jul 2017 22:17:22 -0000 -
Message-ID: <149963864264.23066.10648597957372805455@asianet.co.th> -
MIME-Version: 1.0 -
Importance: High -
Content-Type: application/zip; name="9859586419954.zip" -
Content-Disposition: attachment
PHISHING LINK – DROPPED FILE:
DROPPED FILE:
EXTRACTED FILE DETAILS FOR 27814.js:
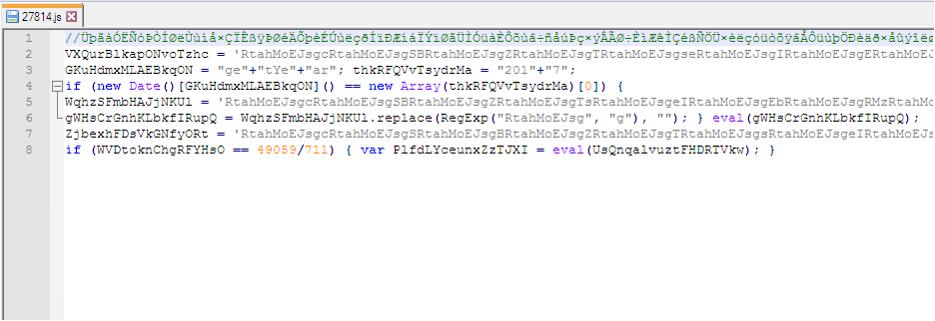
EXTRACTED FILE DETAILS FOR 1.dat:

File Name : 27814.zip 8.00 KB (8,192 bytes)
MD5 hash : 0b9ef52d46a221e2a8e36adc7f448934
SHA1 hash : d9e242ac94ab165d0aa96a9550136ebce4498aa8
SHA256 hash : 0ab80778fd504f4459e9fc6581e42f00cb05bc22774c5f731beeeb262b35346c
File Name : 1.dat 336 KB (344,064 bytes)
MD5 hash : 239b3cd3c466aab2202facf85058e9eb
SHA1 hash : 7b493707a6b3c4c1ba373578042854e417ea3799
SHA256 hash : 2243adb37abe7d7fe4a05cbc774383090551378f67cc3d5be5635c52758170e3
TRAFFIC:
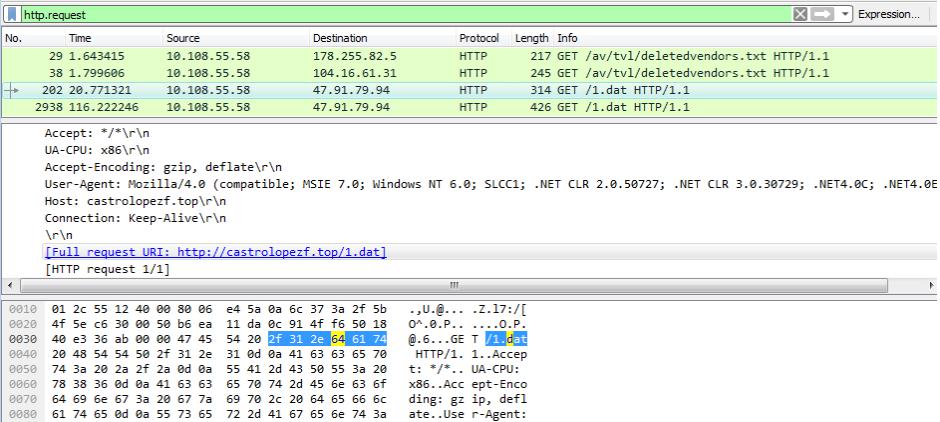
ASSOCIATED URLS:
-
29 1.643415 10.108.55.58 178.255.82.5 HTTP 217 GET /av/tvl/deletedvendors.txt HTTP/1.1
-
38 1.799606 10.108.55.58 104.16.61.31 HTTP 245 GET /av/tvl/deletedvendors.txt HTTP/1.1
-
202 20.771321 10.108.55.58 47.91.79.94 HTTP 314 GET /1.dat HTTP/1.1
-
2938 116.222246 10.108.55.58 47.91.79.94 HTTP 426 GET /1.dat HTTP/1.1
VALKYRIE FOR REFERENCE:
File name : 1.dat
https://valkyrie.comodo.com/get_info?sha1=7b493707a6b3c4c1ba373578042854e417ea3799
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
RAR archive of the malware: [10 July 2017] – [Empty Subject Malware] – 352 KB (360,448 bytes)
-
Email : 37524-1499638651-514808 8.00KB(8,192 bytes)
-
Malware Link Dropped File : 1.dat 336 KB (344,064 bytes)
-
Dropped file : 27814.zip 8.00 KB (8,192 bytes)
