
[01 June 2018] – [ HSBC PAYMENT DELIVERY MALWARE] – SUBJECT : [Fwd: Payment Copy? Payment 05/29/2018 – Tips Ref: [MT103] / Payment Priority / Customer Ref: [37035930FS37289
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware link, and spread to email user with subject “Fwd: Payment Copy? Payment 05/29/2018 – Tips Ref: [MT103] / Payment Priority / Customer Ref: [37035930FS37289]”.
ASSOCIATED FILES:
RAR archive of the malware: [01 June 2018] – [HSBC PAYMENT.RAR] – 28.7 MB (30,127,294 bytes)
- Email : 26349-1527568980-384339.eml 683 KB (699,528 bytes)
- Malware Link Dropped File : Swift Transfer Copy103_doc.r00 248 KB (254,502 bytes)
Payment Advice MT103001_doc.ace 248 KB 254,503 bytes) - Dropped file : tmp.exe 311 KB (318,478 bytes)
THE EMAIL:
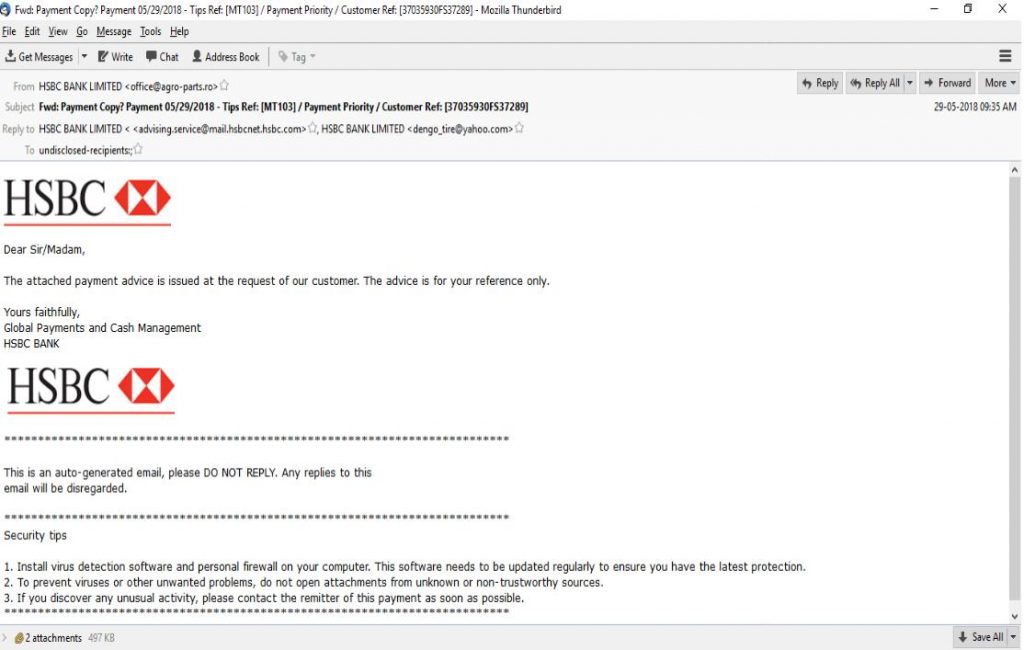
EMAIL DATA:
Received: from unknown (HELO res2whm73.claus.ro) (185.146.84.1) by 0 with SMTP; 29 May 2018 04:43:05 -0000
Received: from [127.0.0.1] (port=36473 helo=server73.romania-webhosting.com)by server73.romania-webhosting.com with esmtpa (Exim 4.91)envelope-from <office@agro-parts.ro>)
From: HSBC BANK LIMITED <office@agro-parts.ro>
Subject: Fwd: Payment Copy? Payment 05/29/2018 – Tips Ref: [MT103] / PaymentPriority / Customer Ref: [37035930FS37289]
Reply-To: “HSBC BANK LIMITED <” <advising.service@mail.hsbcnet.hsbc.com>,
HSBC BANK LIMITED <dengo_tire@yahoo.com>
Mail-Reply-To: “HSBC BANK LIMITED <“<advising.service@mail.hsbcnet.hsbc.com>, HSBC BANK LIMITED <dengo_tire@yahoo.com>
Message-ID: <615f488697688724de3dea1467c720f8@agro-parts.ro>
PHISHING LINK – DROPPED FILE:
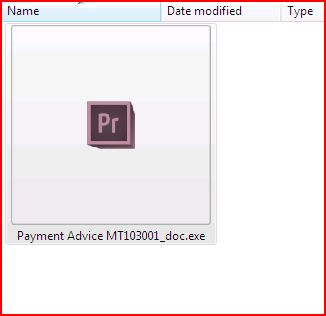
DROPPED FILE:
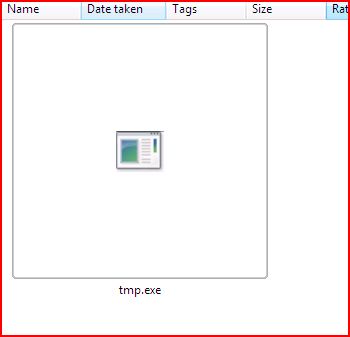
EXTRACTED FILE DETAILS FOR Payment Advice MT103001_doc.exe

EXTRACTED FILE DETAILS FOR tmp.exe
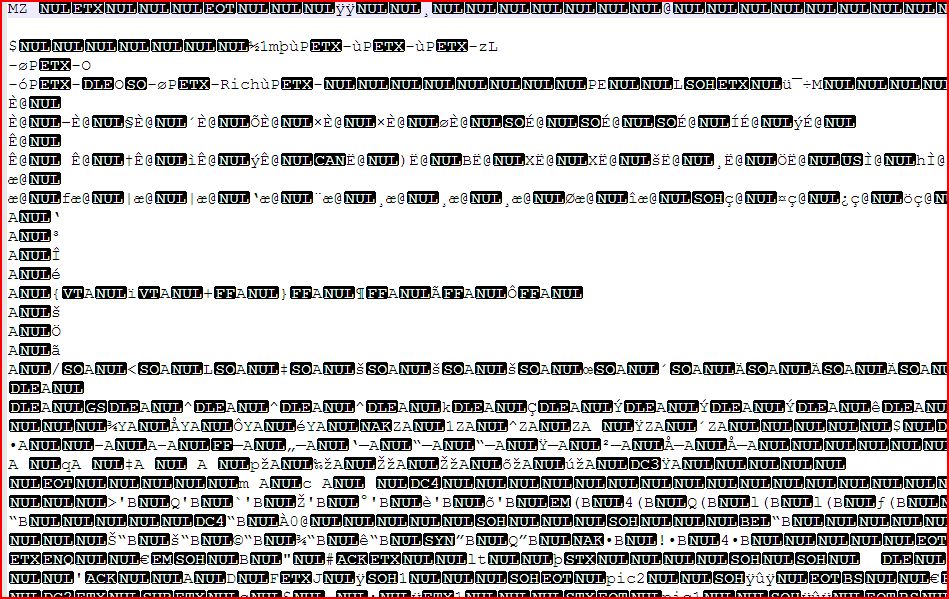
File Name : Payment Advice MT103001_doc.exe 993 KB (1,017,816 bytes)
MD5 hash : 13ED147460A573B5C15B31F76F81EC0E
SHA1 hash : 00DA452383D738C393334792CC3BA5E82D06BD72
SHA256 hash : 353C9336BB4D377B14056A6BDBF8695F2DED45AA991B149135B519DA6B6AA638
File Name : tmp.exe (318,478 bytes)
MD5 hash : BCE1094E83674AE3842FA1FB4C3BA371
SHA1 hash : B62FA5DC19501C16E54FF69FBE5AF1A269B47669
SHA256 hash : 6BA636F3A03F508967C11D0643BF9ACAF94C9E41E7210F0F9451A6B9FA98C1D6
TRAFFIC:
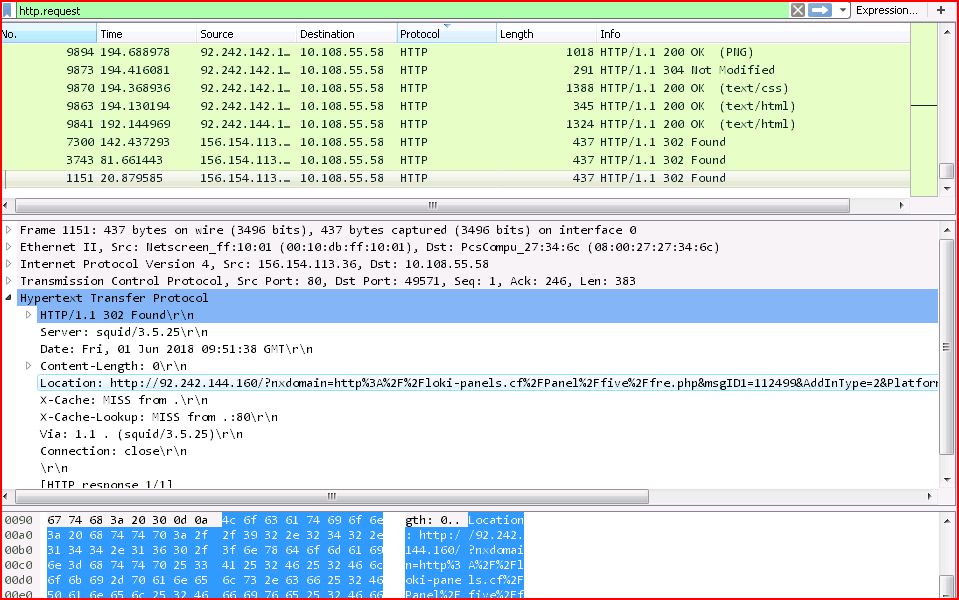
ASSOCIATED URLS:
- 9894 194.688978 92.242.142.137 10.108.55.58 HTTP 1018 HTTP/1.1 200 OK (PNG)
- 9873 194.416081 92.242.142.137 10.108.55.58 HTTP 291 HTTP/1.1 304 Not Modified
- 9863 194.130194 92.242.142.137 10.108.55.58 HTTP 345 HTTP/1.1 200 OK (text/html)
- 7300 142.437293 156.154.113.36 10.108.55.58 HTTP 437 HTTP/1.1 302 Found
VALKYRIE FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=b62fa5dc19501c16e54ff69fbe5af1a269b47669
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
RAR archive of the malware: [01 June 2018] – [HSBC PAYMENT.RAR] – 28.7 MB (30,127,294 bytes)
- Email : 26349-1527568980-384339.eml 683 KB (699,528 bytes)
- Malware Link Dropped File : Swift Transfer Copy103_doc.r00 248 KB (254,502 bytes)
Payment Advice MT103001_doc.ace 248 KB 254,503 bytes) - Dropped file : tmp.exe 311 KB (318,478 bytes)
Resources
related source by – Uber Clone
