
[24 Dec 2016] – [ SQL SOLUTIONS MALWARE ]– SUBJECT : [Urgent]
Comodo Threat Research Labs (CTRL) identified a new phishing email attack with a malware file attachment. It is a “Sql solutions malware” with subject titled: “Urgent” and is targeted at email users.
A new type of JavaScript file malware – “Sql solutions malware” has been created by malware authors.
ASSOCIATED FILES:
ZIP archive of the malware: [24 Dec 2016] – [Sql solutions malware] 145 KB (149,458 bytes)
- 799-1480560394-341386.eml (5,674 bytes)
- -8118op2k7x16.js (18,521 bytes)
- 7dixJ5SG.zk (282,830 bytes)
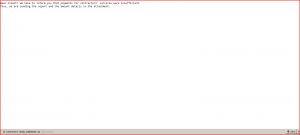
Below is an image of the “Urgent” email. The targeted victim receives an email with the following message:
Dear Client! We have to inform you that payments for contractors’ services were insufficient.
Thus, we are sending the report and the amount details in the attachment.
However, there is an encrypted script running behind the scenes which stays invisible when the infected user opens the mail and the attachment. The malware is designed to download a malicious file on to the infected user’s device which remains unremovable. This c help the cyber criminal track and access data relating to the victim’s identity and credentials.
THE EMAIL
EMAIL DATA:
From: Cornelius Byers <Byers.Cornelius@sql-solutions.ca>
Date: Thu, 01 Dec 2016 09:46:23 +0700
MIME-Version: 1.0
Message-Id: <6950101178.762726.23975.SMail@giresun.edu.tr>
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.4
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: Foxhole.JS_Zip_1.UNOFFICIAL
Content-Type: multipart/related; boundary=7b5539f5cc83213a5071b8ac464b1ab0
Content-Type: application/zip; name=”details_halklailiskiler.zip”
Content-Transfer-Encoding: base64
Content-Disposition: attachment; filename=”details_halklailiskiler.zip”
THE ATTACHMENT
The attachment is a “.zip file” named “details_halklailiskiler.zip”, which is actually a “.js” JavaScript file.
[SCREENSHOT of the java script file]
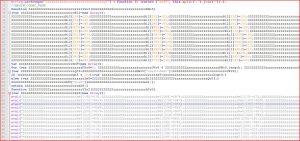
ATTACHMENT AND EXTRACTED .JS FILE:
SHA1 hash : 7510B4C0DC951A2E049D597A9A2735BCDEA4F99D
SHA256 hash : A36A399DFD68EE58DA8322418115F97ACEDDB8637AF4D9949E249886CDBAFDB0
File Name : details_halklailiskiler.zip (3,173 bytes)
SHA1 hash : 5984E6CC7972BE37977AB462E21ADCA5678F2E79
SHA256 hash : 329CAE456B2A1F8C882614B98B764C7E0A9F94B0A987F5745ADB707E290638EF
File Name : -8118op2k7x16.js (18,521 bytes)
TRAFFIC
When the email attachment is opened and executed, the file captures the HTTP Request traffic and finds the host of the malicious file URL.
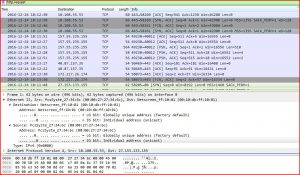
ASSOCIATED URLS:
2016-12-24 18:11:48 10.108.55.53 58205 80 58205→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 SACK_PERM=1 1
2016-12-24 18:11:49 10.108.55.53 58206 80 58206→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 SACK_PERM=1 3
2016-12-24 18:11:48 10.108.55.53 58205 80 58205→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 SACK_PERM=1 1
2016-12-24 18:11:49 10.108.55.53 58212 80 58212→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1 4
2016-12-24 18:11:51 10.108.55.53 58213 80 58213→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1 8
2016-12-24 18:11:51 10.108.55.53 58214 80 58214→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1 10
2016-12-24 18:11:51 10.108.55.53 58217 80 58217→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1 11
2016-12-24 18:11:52 10.108.55.53 58218 80 58218→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1 18
2016-12-24 18:11:53 10.108.55.53 58210 80 58210→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 SACK_PERM=1 22
2016-12-24 18:11:54 10.108.55.53 58220 80 58220→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1 25
IMAGES
FILES DOWNLOADED BY THE INFECTED HOST:
SHA1 hash : 56ADC0A51577065F96563E2AE19B35AE3E407748
SHA256 hash : AE0773460EBD0F25FC454D09E8D7937267DF390D71614B71BAB52BC250306456
File name : 7dixJ5SG.zk (282,830 bytes)
VALKYRIE LINK FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=56adc0a51577065f96563e2ae19b35ae3e407748
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [24 Dec 2016] – [Sql solutions malware] 145 KB (149,458 bytes)
- 799-1480560394-341386.eml (5,674 bytes)
- -8118op2k7x16.js ((18,521 bytes)
- 7dixJ5SG.zk (282,830 bytes)
ZIP files are password-protected with the standard password.
