
[08 August 2017] – [Simple Image Malware] – SUBJECT : [IMG_9103.JPEG]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “IMG_9103.JPEG”.
ASSOCIATED FILES:
- ZIP archive of the malware: [08 August 2017] – [SIMPLE IMAGE MALWARE] – 3.03 MB (3,178,496 bytes)
- 3466-1501897610-669268.eml 8.00 KB (8,192 bytes)
- IMG_3419.js 16.0 KB (16,384 bytes)
- rrGXvNC3.exe 320 KB (327,680 bytes)
- __t35DD.tmp.bat 4.00 KB (4,096 bytes)
THE EMAIL:
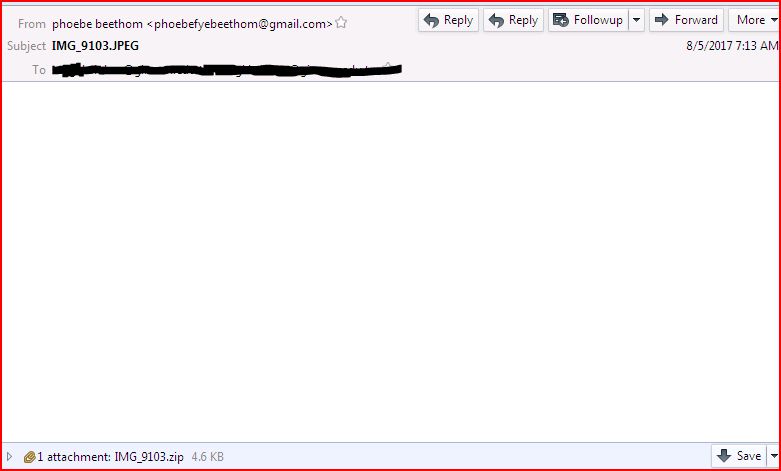
EMAIL DATA:
- Received: from unknown (HELO ?2.182.239.8?) (2.182.239.8)
- by 0 with SMTP; 5 Aug 2017 01:46:50 -0000
- Received-SPF: unknown (0: domain at spf-trusted-fwd1.surgate.net does not designate permitted sender hosts)
- Content-Type: multipart/mixed; boundary=Apple-Mail-46025C43-7319-7F88-0439-8471A9914434
- Content-Transfer-Encoding: 7bit
- From: phoebe beethom <phoebefyebeethom@gmail.com>
- Mime-Version: 1.0 (1.0)
- Date: Sat, 05 Aug 2017 06:13:59 +0430
- Subject: IMG_9103.JPEG
- Message-Id: <A9ADDD7D-D43D-A2B2-F16A-8B7E6B8EFF60@gmail.com>
- Content-Type: application/octet-stream;name=IMG_9103.zip; x-apple-part-url=3683F442-A037-4705-723A-2E1535C4EF7B
- Content-Disposition: inline; filename=IMG_9103.zip
- Content-Transfer-Encoding: base64
THE ATTACHMENT:
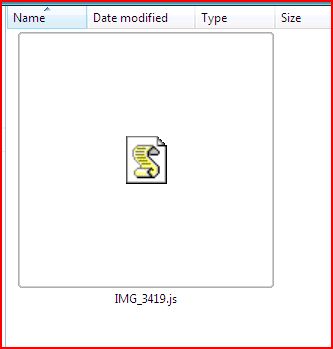
DROPPED FILE:
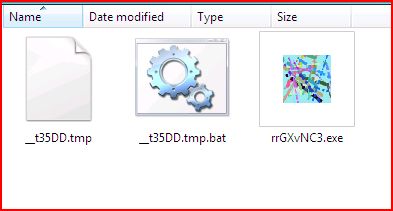
EXTRACTED FILE DETAILS FOR :

File Name : IMG_3419.js 16.0 KB (16,384 bytes)
MD5 :4e9c0d7d05134d579d036dca3fd082fd
SHA-1 :6ab9bbfdae83c2b945aed3acc17b037cf98417dc
File Name : rrGXvNC3.exe 320 KB (327,680 bytes)
MD5 :25e8bf41343bda75a9170aad44094647
SHA-1 :0976b97981640eab4b8c66dc48ed4547d4cb26e6
File Name : __t35DD.tmp.bat 4.00 KB (4,096 bytes)
MD5 :32d8f7a3d0c796cee45f64b63c1cca38
SHA-1 :d58466430a2bba8641bd92c880557379e25b140c
TRAFFIC:
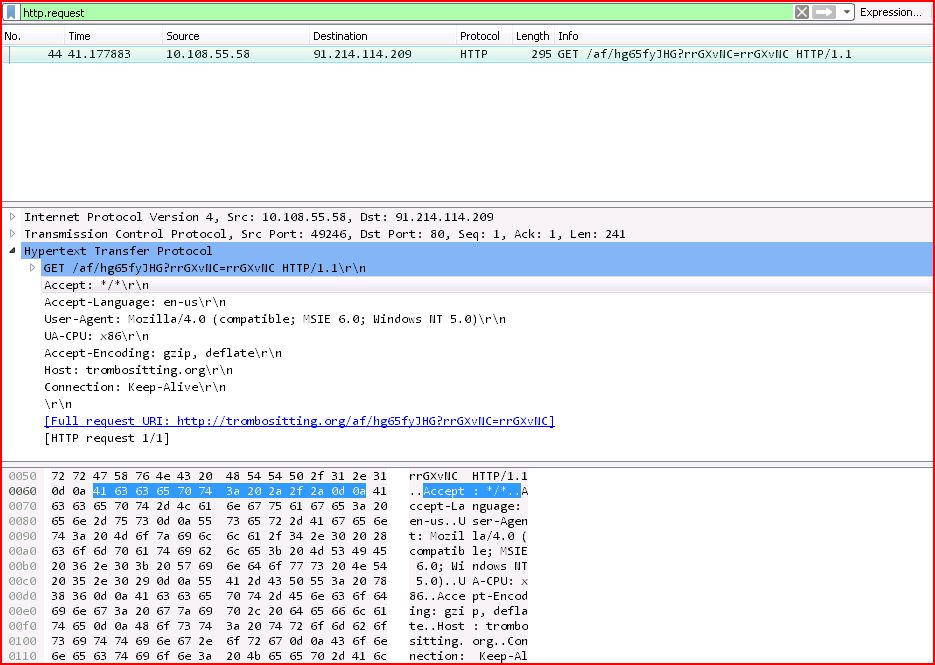
ASSOCIATED URLS:
- 44 41.177883 10.108.55.58 91.214.114.209 HTTP 295 GET /af/hg65fyJHG
rrGXvNC=rrGXvNC HTTP/1.1
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [08 August 2017] – [SIMPLE IMAGE MALWARE] – 516 KB (528,384 bytes)
- 3466-1501897610-669268.eml 8.00 KB (8,192 bytes)
- IMG_3419.js 16.0 KB (16,384 bytes)
- rrGXvNC3.exe 320 KB (327,680 bytes)
- __t35DD.tmp.bat 4.00 KB (4,096 bytes)
related source by – Uber Clone
