
[22 Jan 2017] – [Shipping Details Confirmation Malware] – SUBJECT: [Shipping Documents]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Shipping Documents”.
ASSOCIATED FILES
ZIP archive of the malware: [22 Jan 2017] – [shipment.rar] 337 KB (315,392 bytes)
- 24990-1485081533-752471.eml 305 KB (315,392 bytes)
- Shipping Documents.exe 272 KB (278,528 bytes)
- ship.pcapng 316 KB (323,584 bytes)
THE EMAIL
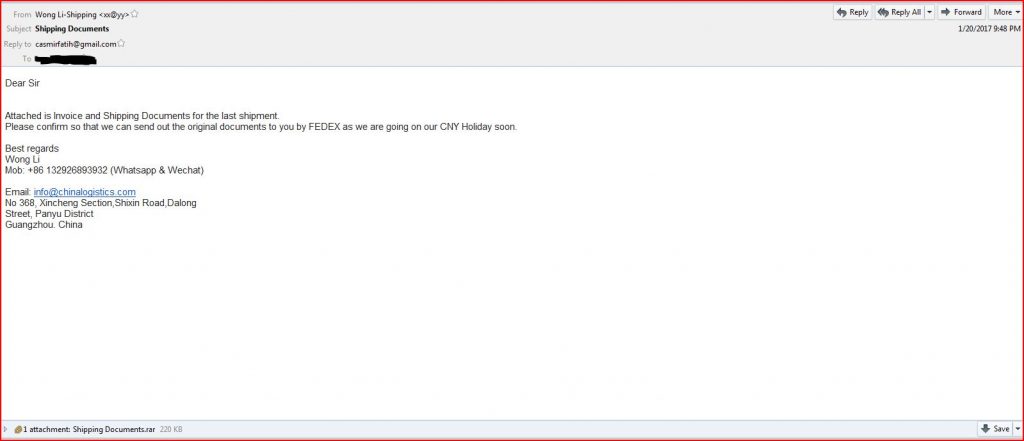
EMAIL DATA
Received: from unknown (HELO mail.pomicro.com) (72.249.151.160) by 0
with SMTP; 22 Jan 2017 10:38:56 -0000
Received-SPF: unknown (0: domain at spf-trusted-fwd1.surgate.net does not
designate permitted sender hosts)
Received: from LTSERVER.CT.local (rrcs-71-43-104-10.se.biz.rr.com [71.43.104.10])
by mail.pomicro.com (Postfix) with ESMTPA id 84F845150300;
Fri, 20 Jan 2017 21:21:18 +0500 (PKT)
MIME-Version: 1.0
Subject: Shipping Documents
From: Wong Li-Shipping <xx@yy>
Date: Fri, 20 Jan 2017 11:18:43 -0500
Reply-To: casmirfatih@gmail.com
THE ATTACHMENT
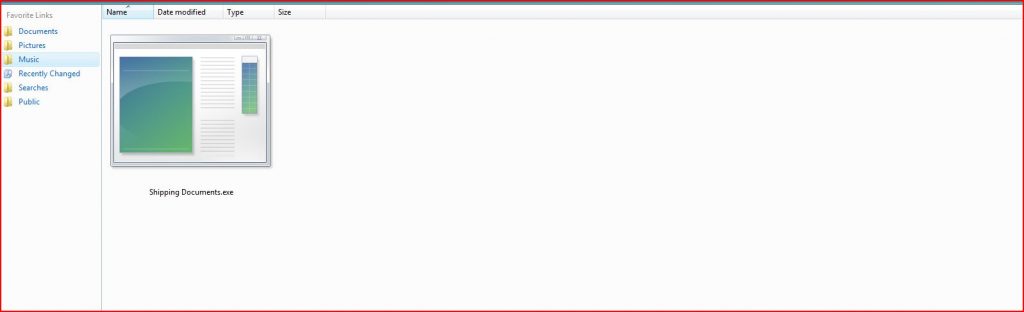
EXTRACTED FILE:
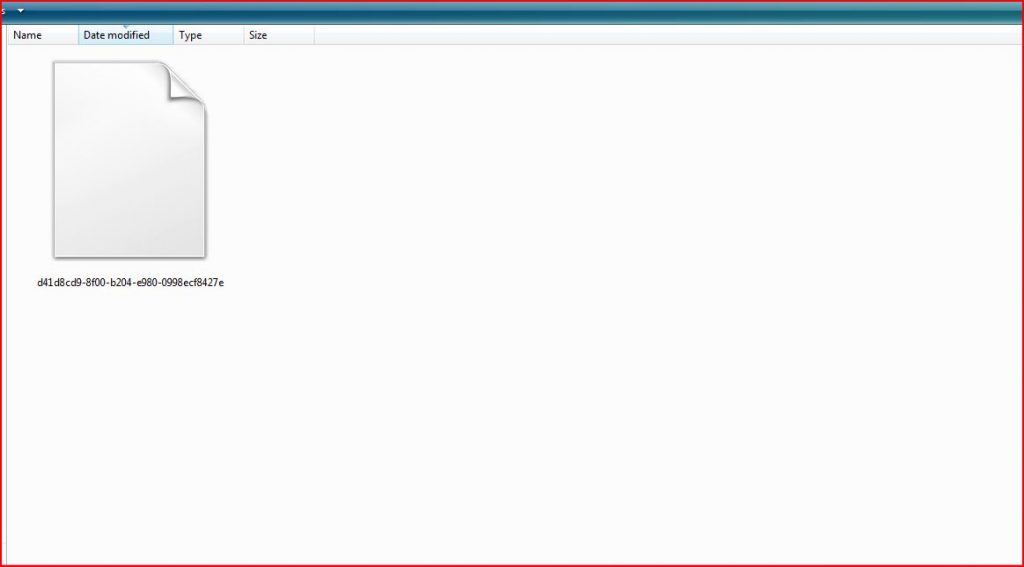
ATTACHMENT AND EXTRACTED FILE
MD5 hash : 5F2F5A7E5EAB6163FA6E285FE64535AC
SHA1 hash : 0D1A5A1FEC9EF9866858B12FCC5D9DB55176D96C
SHA256 hash : F839D6DEE3E64F5ED03C84538AF1032983D19E0897F3266D9B12E28BD3786857
File Name : Shipping Documents.exe
MD5 hash : 5F3F50407A1ED5A76CCB194A38D61135
SHA1 hash : 057018125E7B1F5A5A1D382D9B1562FD13073B2D
SHA256 hash : 4B991AF0E33E97781C72833C0351EA11A803FB68AE3E7BF8A2B3B2281DCC6883
File Name : d41d8cd9-8f00-b204-e980-0998ecf8427e
TRAFFIC
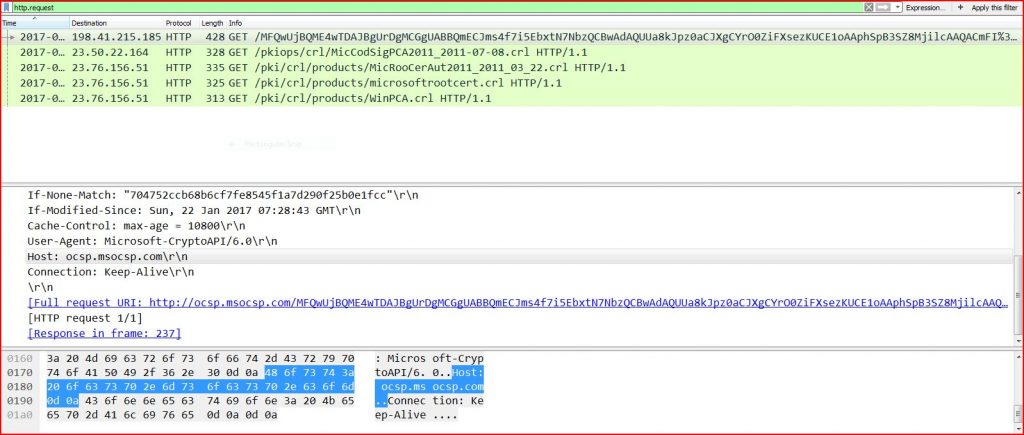
ASSOCIATED URLS
- 2017-01-22 19:03:06 198.41.215.185 HTTP 428 GET /MFQwUjBQME4wTDAJBgUrDgMCGgUABBQmECJms4f7i5EbxtN7NbzQCBwAdAQUUa8kJpz 0aCJXgCYrO0ZiFXsezKUCE1oAAphSpB3SZ8MjilcAAQACmFI%3D HTTP/1.1
- 2017-01-22 19:03:07 23.50.22.164 HTTP 328 GET /pkiops/crl/MicCodSigPCA2011_2011-07-08.crl HTTP/1.1
- 2017-01-22 19:03:07 23.76.156.51 HTTP 335 GET /pki/crl/products/MicRooCerAut2011_2011_03_22.crl HTTP/1.1
- 2017-01-22 19:03:08 23.76.156.51 HTTP 325 GET /pki/crl/products/microsoftrootcert.crl HTTP/1.1
- 2017-01-22 19:03:08 23.76.156.51 HTTP 313 GET /pki/crl/products/WinPCA.crl HTTP/1.1
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES
ZIP archive of the malware: [22 Jan 2017] – [shipment.rar] 337 KB (315,392 bytes)
- 24990-1485081533-752471.eml 305 KB (315,392 bytes)
- Shipping Documents.exe 272 KB (278,528 bytes)
- ship.pcapng 316 KB (323,584 bytes)
