
[26-12-2016] – [SCAN WITH DATE MALWARE] – SUBJECT : [Scan 2016-1130 09:22:27]
“Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Scan 2016-1130 09:22:27”.
With new version of malware getting on to the virtual space called the Scan Malware.
ASSOCIATED FILES:
ZIP archive of the pcap: SCAN WITH DATE MALWARE.rar 4.00 MB (4,204,693 bytes)
ZIP archive of the malware: scan date malware.rar 111 KB (114,427 bytes)
– 8670-1480477948-779417.eml 3.74 KB (3,834 bytes)
– 2016-1126 00-55-59.vbs 5.69 KB (5,829 bytes)
– lVeckQArv.342 200 KB (204,800 bytes)
Below is the sample email. The intended victim user receives the infectious mail with a mail subject as “[Scan] 2016-1130 09:22:27” (scan with the date). However there is an encrypted script running behind which stays invisible, when the infected user opens the mail and hence the attachment. The malware is designed to download a malicious icon on the infected user’s device which remains unremovable. This might help the cyber criminal to track and access the data relating to identity theft and data loss.
THE EMAIL:
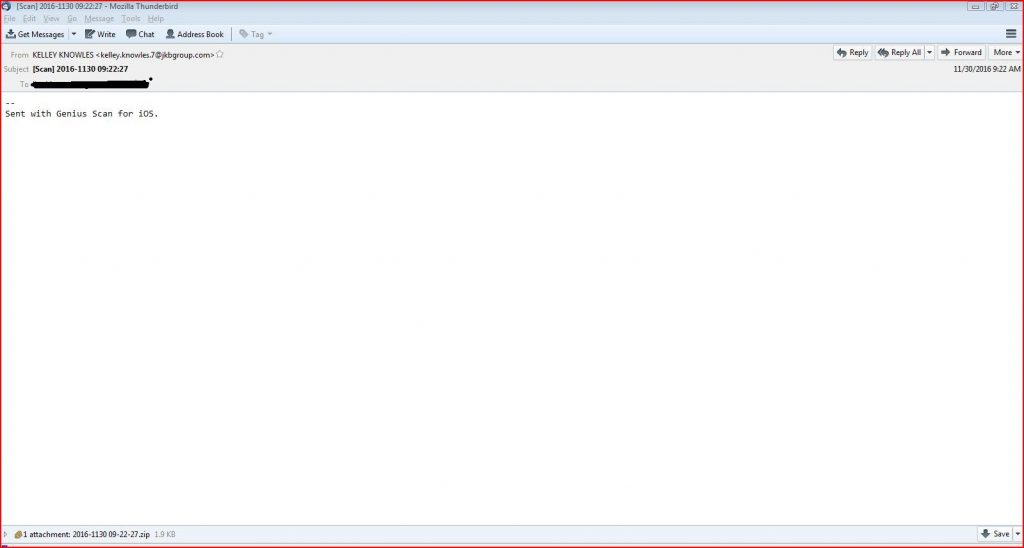
EMAIL DATA:
From: KELLEY KNOWLES <kelley.knowles.7@jkbgroup.com>
Subject: [Scan] 2016-1130 09:22:27
Date: Wed, 30 Nov 2016 09:22:27 +0530
Message-ID: <1d60c925f6e7a9d3cf25329251677e8@jkbgroup.com>
MIME-Version: 1.0
X-Mailer: Microsoft Outlook 14.0
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.4
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: Foxhole.JS_Zip_1v.UNOFFICIAL
Content-Type: multipart/mixed;
boundary=”—-=_NextPart_000_000D_D48B5E19.9BA7902C”
Content-Language: en-gb
Content-Type: application/zip;
name=”2016-1130 09-22-27.zip”
Content-Transfer-Encoding: base64
Content-Disposition: attachment;
filename=”2016-1130 09-22-27.zip
THE ATTACHMENT:
Email Attached “VBScript Script” file:
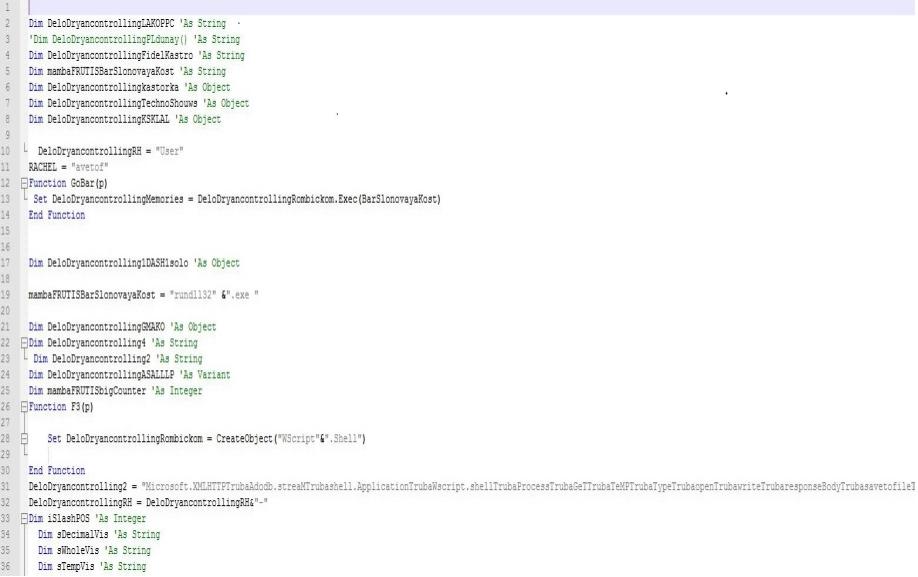
[SCREENSHOTS OF THE ATTACHMENTS]
SHA-1 hash : 7315AA20C8680B2B0F3484DCE5939EAA713F3F51
SHA-256 hash:1A59EAA9860B7A25D6423DE463855A14ED3D84FE0C87C94DEC705071F889A9C64
File Name: 2016-1130 09-22-27.zip 1.89 KB (1,939 bytes)
SHA-1 hash : 6EB348D22F3DB0676FE386B11110743A30230D7D
SHA-256 hash: 5DC752E9292D318AEB36E5E1B52133402D93457D666E194B038E6A671DA6EB65
File Name: 2016-1126 00-55-59.vbs 5.69 KB (5,829 bytes)
TRAFFIC:
When the email attachment opened and executed, the file performs to capture the HTTP Request traffic and finds the host of the malicious file URL
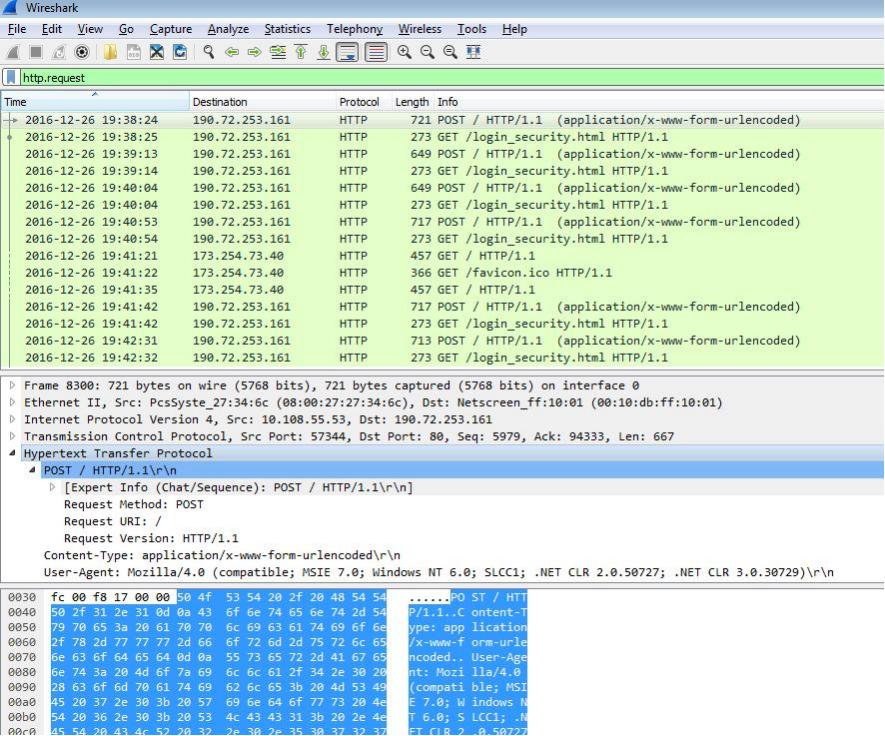
ASSOCIATED URLS:
2016-12-26 19:32:39 190.72.253.161 HTTP 681 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:32:40 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
2016-12-26 19:33:28 190.72.253.161 HTTP 697 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:33:28 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
2016-12-26 19:34:17 190.72.253.161 HTTP 721 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:34:17 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
2016-12-26 19:35:07 190.72.253.161 HTTP 721 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:35:08 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
2016-12-26 19:35:56 190.72.253.161 HTTP 645 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:35:57 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
2016-12-26 19:36:10 65.112.85.57 HTTP 444 GET /MFUwUzBRME8wTTAJBgUrDgMCGgUABBTkLVLomfJQOu5CFIgPOR73ljBRHAQU% 2BL36r3N3xscb%2BUtNEafRM6%2BvchECFFH4KTplun7Y4FbrBRhiskF98uZz HTTP/1.1
2016-12-26 19:36:10 65.112.85.57 HTTP 444 GET /MFUwUzBRME8wTTAJBgUrDgMCGgUABBTkLVLomfJQOu5CFIgPOR73ljBRHAQU% 2BL36r3N3xscb%2BUtNEafRM6%2BvchECFFH4KTplun7Y4FbrBRhiskF98uZz HTTP/1.1
2016-12-26 19:36:39 198.41.214.186 HTTP 430 GET /MFQwUjBQME4wTDAJBgUrDgMCGgUABBQmECJms4f7i5EbxtN7NbzQCBwAdAQ UUa8kJpz0aCJXgCYrO0ZiFXsezKUCE1oABasbVc1%2F30qkcksAAQAFqxs%3D HTTP/1.1
2016-12-26 19:36:45 190.72.253.161 HTTP 681 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:36:46 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
2016-12-26 19:37:35 190.72.253.161 HTTP 677 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:37:35 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
2016-12-26 19:38:11 72.21.91.29 OCSP 482 Request
2016-12-26 19:38:11 72.21.91.29 OCSP 482 Request
2016-12-26 19:38:24 190.72.253.161 HTTP 721 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:38:25 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
2016-12-26 19:39:13 190.72.253.161 HTTP 649 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:39:14 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
2016-12-26 19:40:04 190.72.253.161 HTTP 649 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:40:04 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
2016-12-26 19:40:53 190.72.253.161 HTTP 717 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:40:54 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
2016-12-26 19:41:21 173.254.73.40 HTTP 457 GET / HTTP/1.1
2016-12-26 19:41:22 173.254.73.40 HTTP 366 GET /favicon.ico HTTP/1.1
2016-12-26 19:41:35 173.254.73.40 HTTP 457 GET / HTTP/1.1
2016-12-26 19:41:42 190.72.253.161 HTTP 717 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:41:42 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
2016-12-26 19:42:31 190.72.253.161 HTTP 713 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2016-12-26 19:42:32 190.72.253.161 HTTP 273 GET /login_security.html HTTP/1.1
IMAGES:
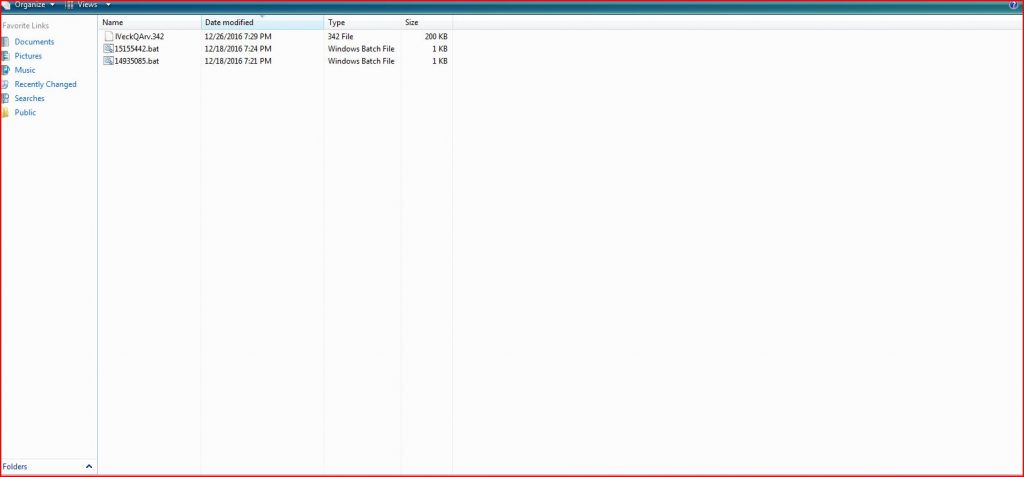
This section contains the list of files related to payload
SHA-1 hash: 4A573351CF0DFE6F27EF3F2AD46547907974596F
SHA256 hash: 4580A67B6EEDCF233F9C74723635D89F29CCF1CC58FE0C12EF0B8AA80E38AA73
File Name : lVeckQArv.342 200 KB (204,800 bytes)
VALKYRIE LINK FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=4a573351cf0dfe6f27ef3f2ad46547907974596f
FINAL NOTES:
Once again, here are the associated files:
ZIP archive of the pcap: SCAN WITH DATE MALWARE.rar 4.00 MB (4,204,693 bytes)
ZIP archive of the malware: scan date malware.rar 111 KB (114,427 bytes)
