
[16 Jan 2017] – [Quotation Malware] – SUBJECT : [Request For Quotation #20017]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Request FOr Quotation #20017.
ASSOCIATED FILES
ZIP archive of the malware: [15 Jan 2017] – [Quotation.rar] 337 KB (345,606 bytes)
- 16694-1484212597-190563.eml 233 KB (239,401 bytes)
- REQUEST FOR QUOTATION_PDF.exe 354 KB (362,496 bytes)
- quotation.pcapng 180 KB (184,944 bytes)
THE EMAIL
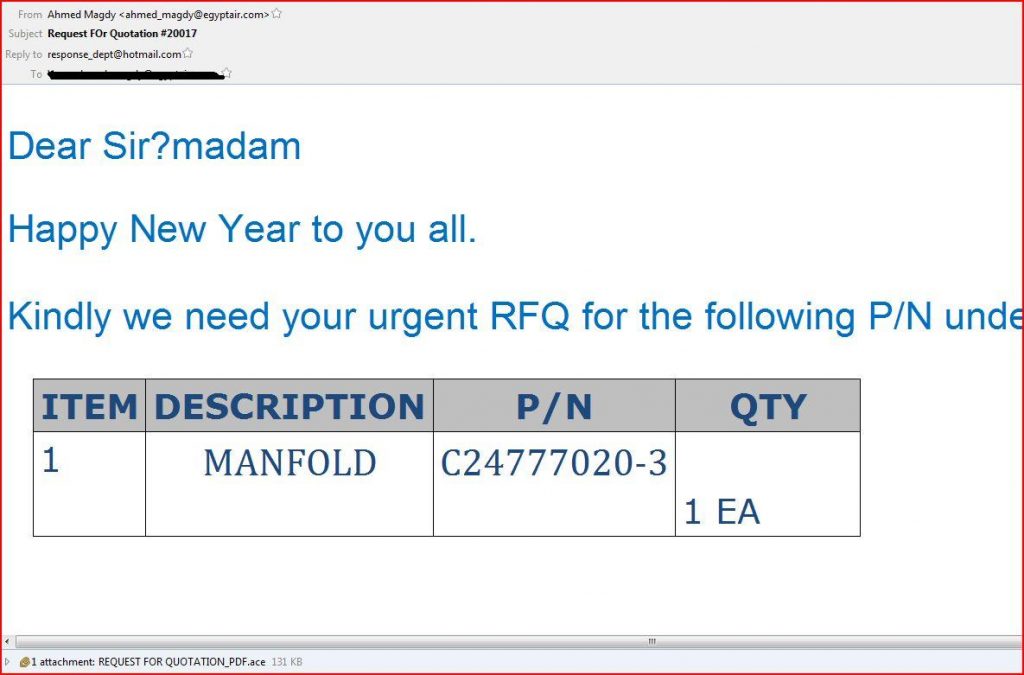
EMAIL DATA
From: Ahmed Magdy <ahmed_magdy@egyptair.com>
Date: Thu, 12 Jan 2017 07:50:41 +0200
Reply-To: response_dept@hotmail.com
Message-Id: <20170112055107.071FC15892A0@ms1.asiansourcing.com.tw>
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.5
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: attachment REQUEST FOR QUOTATION_PDF.ace blocked because
of filter rule: .ace$ action: REJECT
Content-Type: multipart/mixed;
Content-Transfer-Encoding: quoted-printable
Content-Description: Mail message body
THE ATTACHMENT
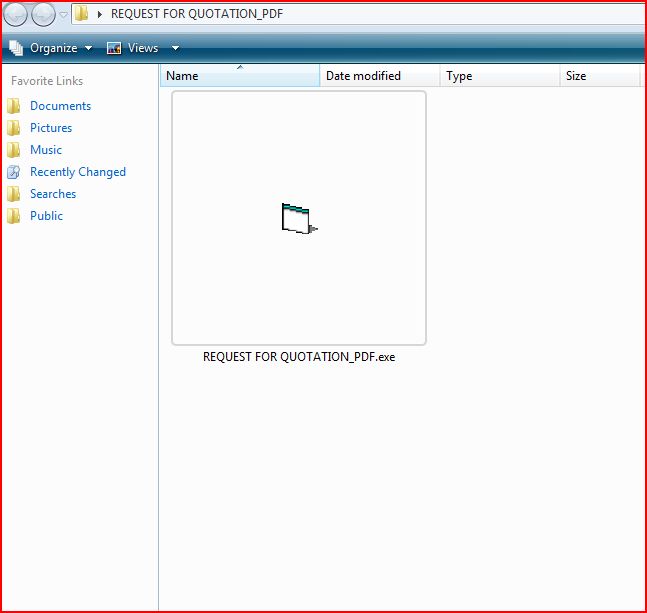
ATTACHMENT AND EXTRACTED FILE
MD5 hash : 5C75A5248AF4365899091F5AF9D30E2D
SHA1 hash : 325768488998484925338A1936324270BE5B51C9
SHA256 hash : AC2D3BC76A7FE51C36C15C4E4FE885D5F4085E8931D414F7A37D1360A81B9EEC
File Name : REQUEST FOR QUOTATION_PDF.exe
TRAFFIC
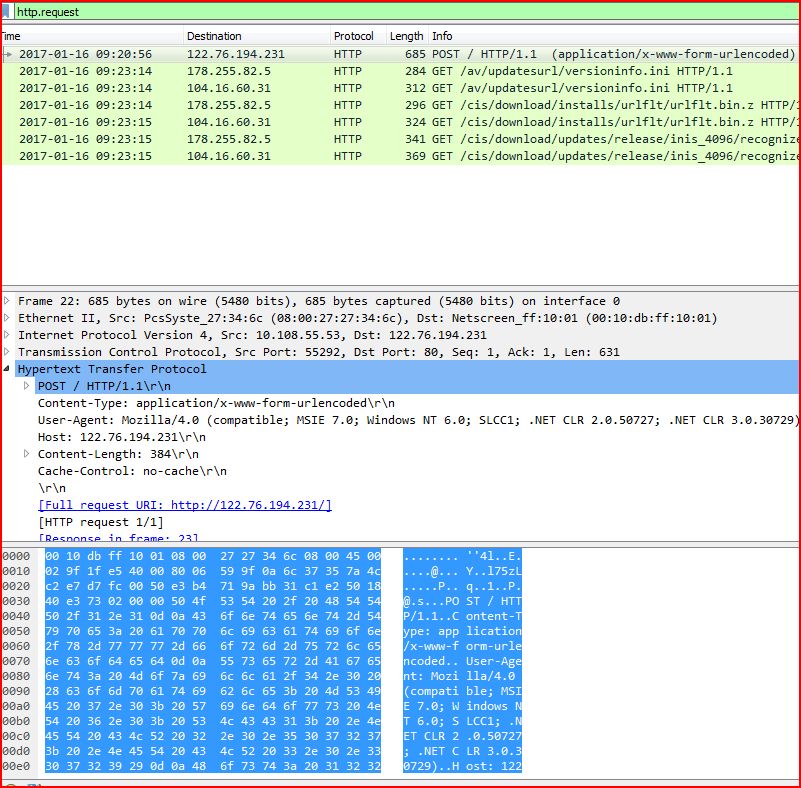
ASSOCIATED URLS
2017-01-16 09:20:56 122.76.194.231 HTTP 685 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-16 09:23:14 178.255.82.5 HTTP 284 GET /av/updatesurl/versioninfo.ini HTTP/1.1
2017-01-16 09:23:14 104.16.60.31 HTTP 312 GET /av/updatesurl/versioninfo.ini HTTP/1.1
2017-01-16 09:23:14 178.255.82.5 HTTP 296 GET /cis/download/installs/urlflt/urlflt.bin.z HTTP/1.1
2017-01-16 09:23:15 104.16.60.31 HTTP 324 GET /cis/download/installs/urlflt/urlflt.bin.z HTTP/1.1
2017-01-16 09:23:15 178.255.82.5 HTTP 341 GET /cis/download/updates/release/inis_4096/recognizers/proto_v6/cmdscope_update_x32.xml.7z HTTP/1.1
2017-01-16 09:23:15 104.16.60.31 HTTP 369 GET /cis/download/updates/release/inis_4096/recognizers/proto_v6/cmdscope_update_x32.xml.7z HTTP/1.1
VALKYRIE LINK FOR REFERENCE
https://valkyrie.comodo.com/get_info?sha1=325768488998484925338a1936324270be5b51c9
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES
ZIP archive of the malware: [15 Jan 2017] – [Quotation.rar] 337 KB (345,606 bytes)
- 16694-1484212597-190563.eml 233 KB (239,401 bytes)
- REQUEST FOR QUOTATION_PDF.exe 354 KB (362,496 bytes)
- quotation.pcapng 180 KB (184,944 bytes)
