
[03 Jan 2017] – [Purchase Order Malware] – SUBJECT : [Purchase Order]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Purchase Order”.
ASSOCIATED FILES
ZIP archive of the malware: [03 Jan 2017] – [Purchase Order Malware] 176 KB (180,224 bytes)
- 47159-1483088846-391441.eml 240 KB (245,760 bytes)
- Purchase-Order.exe 216 KB (221,184 bytes)
THE EMAIL
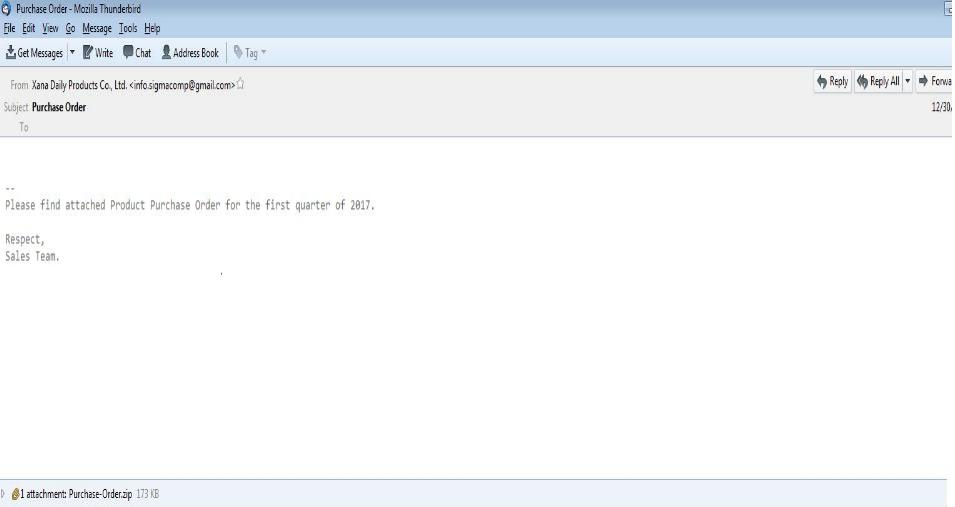
EMAIL DATA
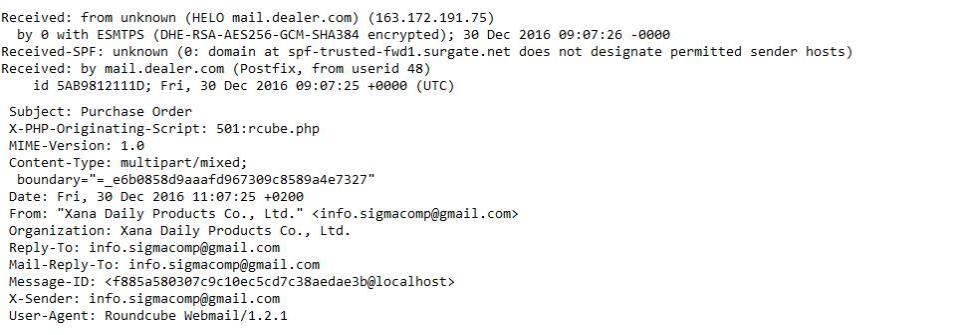
THE ATTACHMENT
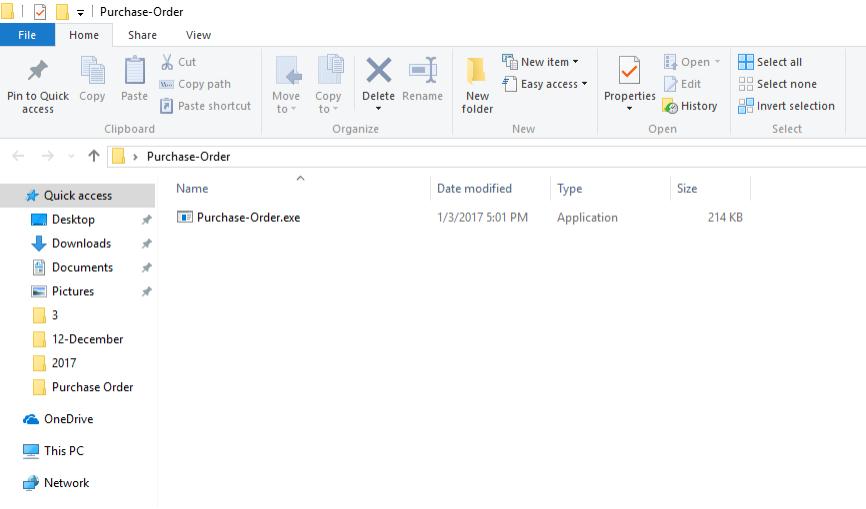
ATTACHMENT AND EXTRACTED .Exe FILE
File Name : Purchase-Order.zip 216 KB (221,184 bytes)
MD5 hash : bfd4a64b448b44e860fafb30cfdf6cc9
SHA1 hash : 371be557985e0b520d89f91ec46ea6034a0d31fa
SHA256 hash : 3602458df7ceeab03a2922b19953367e115ad53912764fc05dd53e208c39939e
File Name : Purchase-Order.exe 216 KB (221,184 bytes)
MD5 hash : 22fd9178159e556d3f9a75988673dcc6
SHA1 hash : b52b6f9644e2c47e7026f6e42e47bbcdf5e65936
SHA256 hash : b300d03dac0258133ff2d7ee794a95aaa9360ab1af3c20e9dab9b834dbfeebd0
TRAFFIC
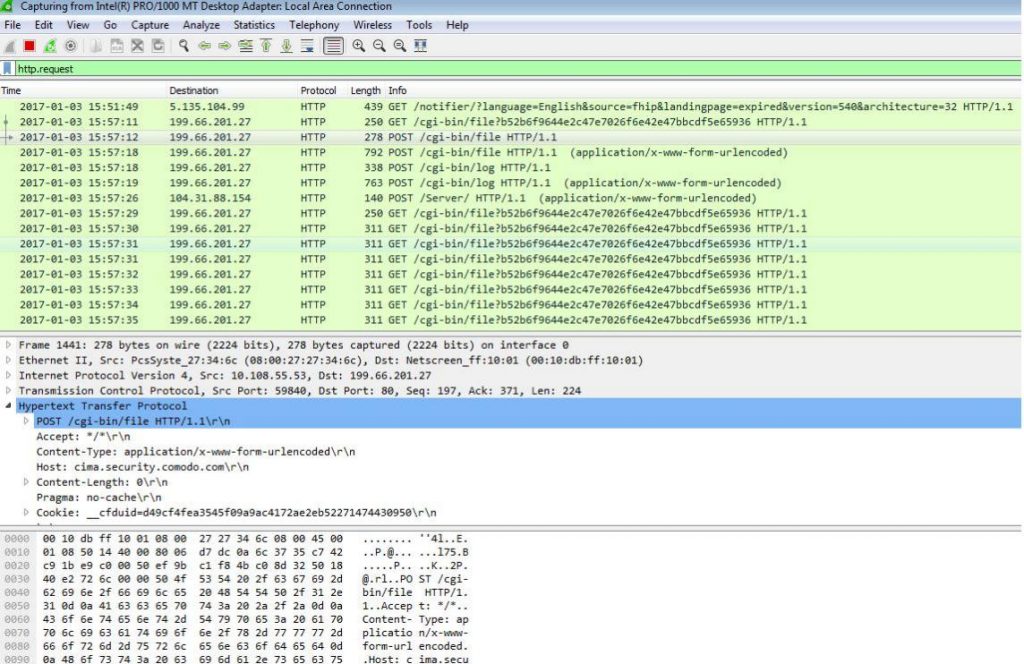
ASSOCIATED URLS:
2017-01-03 15:57:11 199.66.201.27 HTTP 250 GET /cgi-bin/file?b52b6f9644e2c47e7026f6e42e47bbcdf5e65936 HTTP/1.1
2017-01-03 15:57:12 199.66.201.27 HTTP 278 POST /cgi-bin/file HTTP/1.1
2017-01-03 15:57:18 199.66.201.27 HTTP 792 POST /cgi-bin/file HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-03 15:57:18 199.66.201.27 HTTP 338 POST /cgi-bin/log HTTP/1.1
2017-01-03 15:57:19 199.66.201.27 HTTP 763 POST /cgi-bin/log HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-03 15:57:26 104.31.88.154 HTTP 140 POST /Server/ HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-03 15:57:29 199.66.201.27 HTTP 250 GET /cgi-bin/file?b52b6f9644e2c47e7026f6e42e47bbcdf5e65936 HTTP/1.1
2017-01-03 15:57:30 199.66.201.27 HTTP 311 GET /cgi-bin/file?b52b6f9644e2c47e7026f6e42e47bbcdf5e65936 HTTP/1.1
2017-01-03 15:57:31 199.66.201.27 HTTP 311 GET /cgi-bin/file?b52b6f9644e2c47e7026f6e42e47bbcdf5e65936 HTTP/1.1
2017-01-03 15:57:31 199.66.201.27 HTTP 311 GET /cgi-bin/file?b52b6f9644e2c47e7026f6e42e47bbcdf5e65936 HTTP/1.1
2017-01-03 15:57:32 199.66.201.27 HTTP 311 GET /cgi-bin/file?b52b6f9644e2c47e7026f6e42e47bbcdf5e65936 HTTP/1.1
2017-01-03 15:57:33 199.66.201.27 HTTP 311 GET /cgi-bin/file?b52b6f9644e2c47e7026f6e42e47bbcdf5e65936 HTTP/1.1
2017-01-03 15:57:34 199.66.201.27 HTTP 311 GET /cgi-bin/file?b52b6f9644e2c47e7026f6e42e47bbcdf5e65936 HTTP/1.1
2017-01-03 15:57:34 199.66.201.27 HTTP 311 GET /cgi-bin/file?b52b6f9644e2c47e7026f6e42e47bbcdf5e65936 HTTP/1.1
IMAGES:
VALKYRIE LINK FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=b52b6f9644e2c47e7026f6e42e47bbcdf5e65936
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES
ZIP archive of the malware: [03 Jan 2017] – [Purchase Order Malware] 176 KB (180,224 bytes)
- 47159-1483088846-391441.eml 240 KB (245,760 bytes)
- Purchase-Order.exe 216 KB (221,184 bytes)
