
[07 Apr 2017] – [Proforma Invoice Malware] – SUBJECT : [Payment for proforma invoice order NH-43017]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Payment for proforma invoice order NH-43017”.
ASSOCIATED FILES:
ZIP archive of the malware: [07 Apr 2017] – [Proforma malware.rar] 1.74 MB (1700,000 bytes)
- 8910-1491450291-395585.eml 366 KB (374,980 bytes)
- proforma.pcapng 1.57 MB (1,646,972 bytes)
- 052017.scr 491 KB (503,512 bytes)
THE EMAIL:
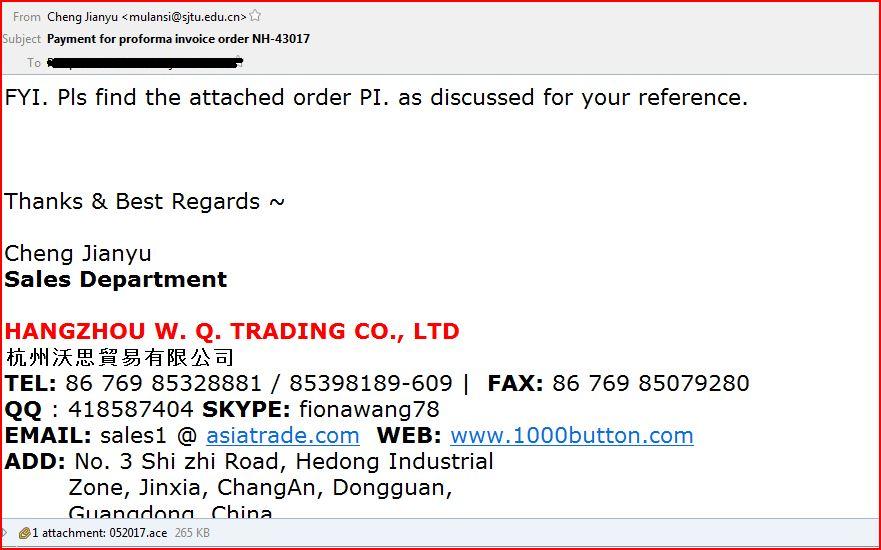
EMAIL DATA:
Subject: Payment for proforma invoice order NH-43017
From: Cheng Jianyu <mulansi@sjtu.edu.cn>
Date: Thu, 06 Apr 2017 03:09:12 -0700
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.6
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: attachment 052017.ace blocked because of filter rule:
.ace$ action: REJECT
X-KORUMAIL-QueueId: 8910-1491450291-395585
Content-Type: multipart/mixed; boundary=”===============1201130129==”
THE ATTACHMENT:
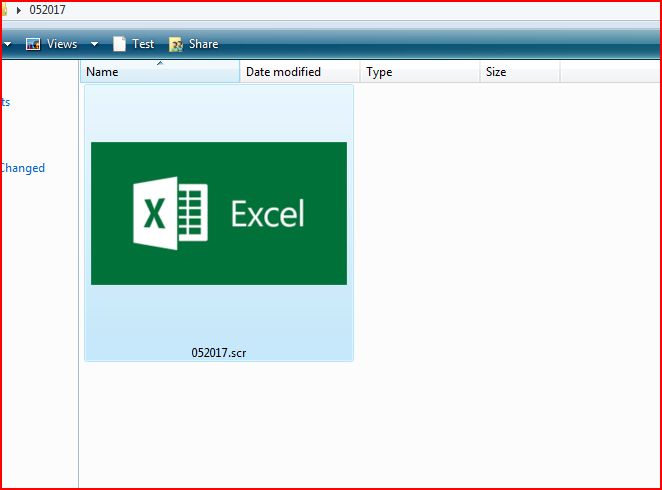
DROPPED FILE:
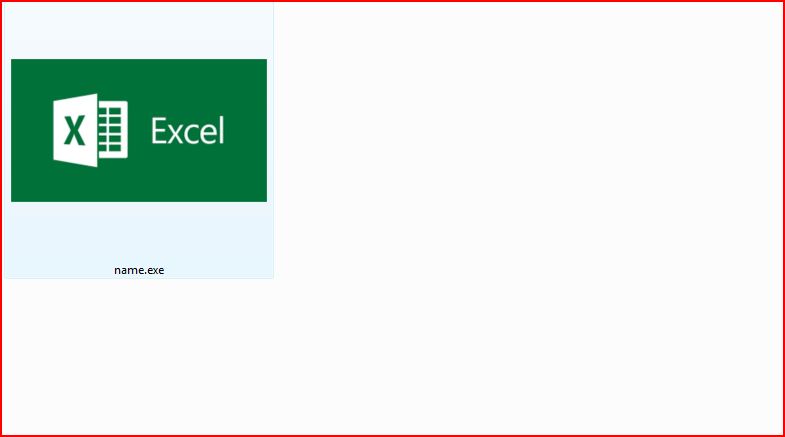
EXTRACTED FILE DETAILS:

File Name : 052017.scr 491 KB (503,512 bytes)
MD5 hash : 2963897646F6008E4D4222D57E4F38A4
SHA1 hash : 32A60427D3847F46BF4BA46D5236B8E9E17EE6B2
SHA256 hash : 134BA184D0391BD83440928CE8FFDF85EEDA30ED4E251DCD6925A97931C638A0
File Name : name.exe 491 KB (503,512 bytes)
MD5 hash : 134BA184D0391BD83440928CE8FFDF85EEDA30ED4E251DCD6925A97931C638A0
SHA1 hash : 134BA184D0391BD83440928CE8FFDF85EEDA30ED4E251DCD6925A97931C638A0
SHA256 hash : 134BA184D0391BD83440928CE8FFDF85EEDA30ED4E251DCD6925A97931C638A0
TRAFFIC:
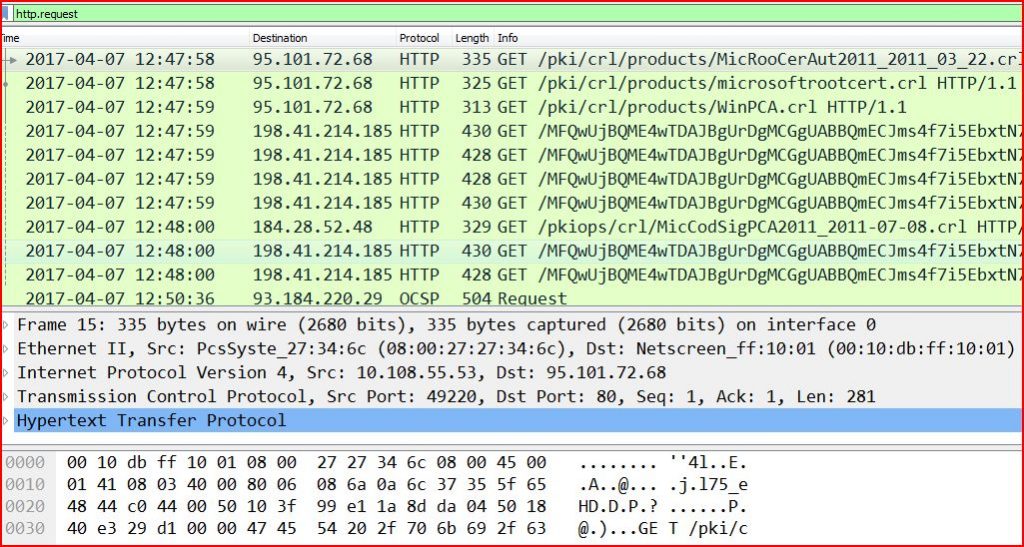
ASSOCIATED URLS:
2017-04-07 12:47:58 95.101.72.68 HTTP 335 GET /pki/crl/products/MicRooCerAut2011_2011_03_22.crl HTTP/1.1
2017-04-07 12:47:58 95.101.72.68 HTTP 325 GET /pki/crl/products/microsoftrootcert.crl HTTP/1.1
2017-04-07 12:47:59 95.101.72.68 HTTP 313 GET /pki/crl/products/WinPCA.crl HTTP/1.1
2017-04-07 12:47:59 198.41.214.185 HTTP 430 GET /MFQwUjBQME4wTDAJBgUrDgMCGgU ABBQmECJms4f7i5EbxtN7NbzQCBwAdAQUUa8kJpz0aCJXgCYrO0ZiFXsezK UCE1oAAy8FcNl%2Bq8UBrk0AAQADLwU%3D HTTP/1.1
2017-04-07 12:47:59 198.41.214.185 HTTP 428 GET /MFQwUjBQME4wTDAJBgUrDgMCGgUA BBQmECJms4f7i5EbxtN7NbzQCBwAdAQUUa8kJpz0aCJXgCYrO0ZiFXsezK UCE1oABgGTsEFEd9yef5cAAQAGAZM%3D HTTP/1.1
2017-04-07 12:47:59 198.41.214.185 HTTP 428 GET /MFQwUjBQME4wTDAJBgUrDgMCGgUAB BQmECJms4f7i5EbxtN7NbzQCBwAdAQUUa8kJpz0aCJXgCYrO0ZiFXsezK UCE1oABXWPhcP9WMn4FIcAAQAFdY8%3D HTTP/1.1
2017-04-07 12:47:59 198.41.214.185 HTTP 430 GET /MFQwUjBQME4wTDAJBgUrDgMCGgUAB BQmECJms4f7i5EbxtN7NbzQCBwAdAQUUa8kJpz0aCJXgCYrO0ZiFXsez KUCE1oABhD7yG%2BbjZf34tQAAQAGEPs%3D HTTP/1.1
2017-04-07 12:48:00 184.28.52.48 HTTP 329 GET /pkiops/crl/MicCodSigPCA2011_2011-07-08.crl HTTP/1.1
2017-04-07 12:48:00 198.41.214.185 HTTP 430 GET /MFQwUjBQME4wTDAJBgUrDgMCGgUAB BQmECJms4f7i5EbxtN7NbzQCBwAdAQUUa8kJpz0aCJXgCYrO0ZiFXsez KUCE1oABasbVc1%2F30qkcksAAQAFqxs%3D HTTP/1.1
2017-04-07 12:48:00 198.41.214.185 HTTP 428 GET /MFQwUjBQME4wTDAJBgUrDgMCGgUAB BQmECJms4f7i5EbxtN7NbzQCBwAdAQUUa8kJpz0aCJXgCYrO0ZiFXsez KUCE1oAB069RlCCbUknMzMAAAAHTr0%3D HTTP/1.1
2017-04-07 12:50:36 93.184.220.29 OCSP 504 Request
VALKYRIE FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=32a60427d3847f46bf4ba46d5236b8e9e17ee6b2
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [07 Apr 2017] – [Proforma malware.rar] 1.74 MB (1700,000 bytes)
- 8910-1491450291-395585.eml 366 KB (374,980 bytes)
- proforma.pcapng 1.57 MB (1,646,972 bytes)
- 052017.scr 491 KB (503,512 bytes)
