
[09 Mar 2017] – [Product Sample Malware] – SUBJECT : [PRODUCT SAMPLE]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “PRODUCT SAMPLE”.
ASSOCIATED FILES:
ZIP archive of the malware: [09 Mar 2017] – [Product.rar] 230 KB (236,506 bytes)
- mail for blog5619-1488769290- 908440.eml 129 KB (133,066 bytes)
- Product Sample-4526857678926345_pdf.zip 94.0 KB (96,323 bytes)
- Product sample1.pcapng 138 KB (141,380 bytes)
THE EMAIL:
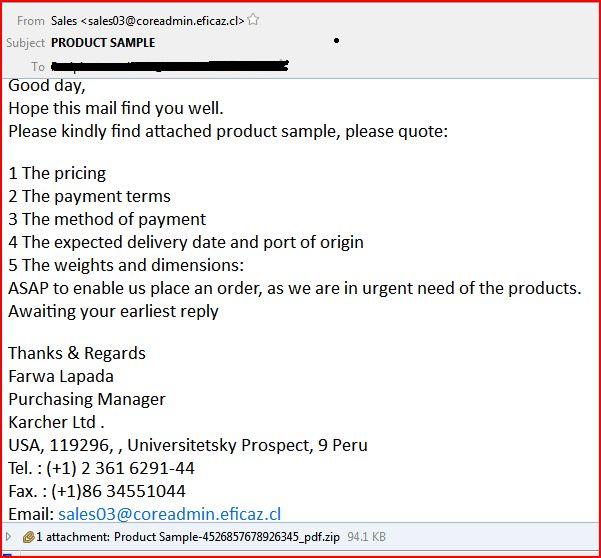
EMAIL DATA:
MIME-Version: 1.0
Subject: PRODUCT SAMPLE
From: Sales <sales03@coreadmin.eficaz.cl>
Date: Mon, 06 Mar 2017 03:09:37 +0100
Reply-To: sales03@coreadmin.eficaz.cl
Message-Id: <20170306021459.6A1C03D5CB4@mail.eficaz.cl>
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.6
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: Foxhole.Zip_pdf.UNOFFICIAL
X-KORUMAIL-QueueId: 5619-1488769290-908440
Content-Type: multipart/mixed;
THE ATTACHMENT:

EXTRACTED FILE DETAILS:

File Name : Product Sample-4526857678926345_pdf.zip 94.0 KB (96,323 bytes)
MD5 hash : B3B395BDFB6B117EA33793F09240566D
SHA1 hash : F2F5D34308397E02019899E5DC481A701068EFD6
SHA256 hash : 7FCF65264D0DA011C1D78F6C7EF52158EDCD5A6CD2280784CB37E106C637A198
File Name : Product Sample-4526857678926345_pdf.exe
MD5 hash : C6FF60616D4EBAEBBCA2393AA3B0407D
SHA1 hash : 35EAFFFB0F1BA8947B2395010A3E5569EE4BAC1D
SHA256 hash : A1BF9A7A40D2D1711604542BB47F51C583421A8F7CC6C6B1ABB7D40CBB533A42
TRAFFIC:
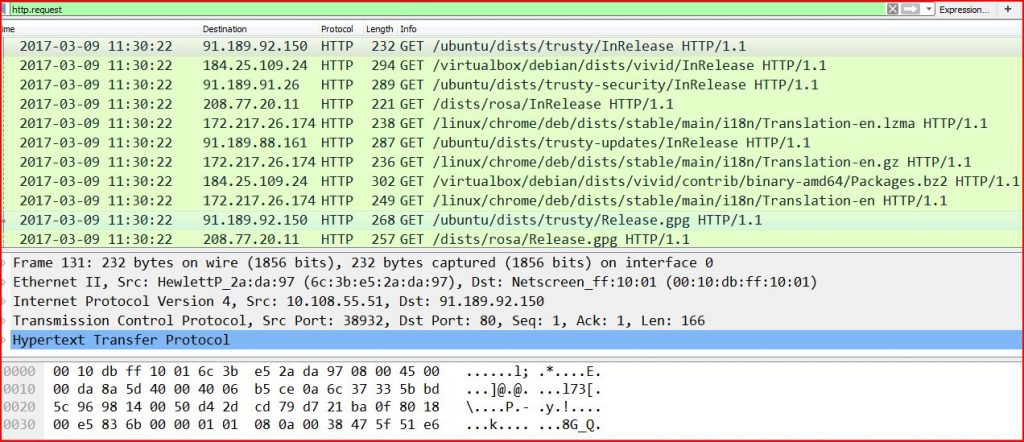
ASSOCIATED URLS:
2017-03-09 11:30:22 91.189.92.150 HTTP 232 GET /ubuntu/dists/trusty/InRelease HTTP/1.1
2017-03-09 11:30:22 184.25.109.24 HTTP 294 GET /virtualbox/debian/dists/vivid/InRelease HTTP/1.1
2017-03-09 11:30:22 91.189.91.26 HTTP 289 GET /ubuntu/dists/trusty-security/InRelease HTTP/1.1
2017-03-09 11:30:22 208.77.20.11 HTTP 221 GET /dists/rosa/InRelease HTTP/1.1
2017-03-09 11:30:22 172.217.26.174 HTTP 238 GET /linux/chrome/deb/dists/stable/main/i18n/Translation-en.lzma HTTP/1.1
2017-03-09 11:30:22 91.189.88.161 HTTP 287 GET /ubuntu/dists/trusty-updates/InRelease HTTP/1.1
2017-03-09 11:30:22 172.217.26.174 HTTP 236 GET /linux/chrome/deb/dists/stable/main/i18n/Translation-en.gz HTTP/1.1
2017-03-09 11:30:22 184.25.109.24 HTTP 302 GET /virtualbox/debian/dists/vivid/contrib/binary-amd64/Packages.bz2 HTTP/1.1
2017-03-09 11:30:22 172.217.26.174 HTTP 249 GET /linux/chrome/deb/dists/stable/main/i18n/Translation-en HTTP/1.1
2017-03-09 11:30:22 91.189.92.150 HTTP 268 GET /ubuntu/dists/trusty/Release.gpg HTTP/1.1
2017-03-09 11:30:22 208.77.20.11 HTTP 257 GET /dists/rosa/Release.gpg HTTP/1.1
VALKYRIE FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=35eafffb0f1ba8947b2395010a3e5569ee4bac1d
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [09 Mar 2017] – [Product.rar] 230 KB (236,506 bytes)
- mail for blog5619-1488769290- 908440.eml 129 KB (133,066 bytes)
- Product Sample-4526857678926345_pdf.zip 94.0 KB (96,323 bytes)
- Product sample1.pcapng 138 KB (141,380 bytes)
