
[16 Jan 2017] – [Pending Payment Malware] – SUBJECT: [Re:Pending payment]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Re:Pending payment”.
ASSOCIATED FILES
ZIP archive of the malware: [16 Jan 2017] – [Pending payment.rar] 629 KB (644,461 bytes)
- 27351-1484220970-379799.eml 674 KB (691,064 bytes)
- MANIFEST.MF 212 bytes (212 bytes)
- Pending payment.pcapng 332 KB (340,264 bytes)
THE EMAIL
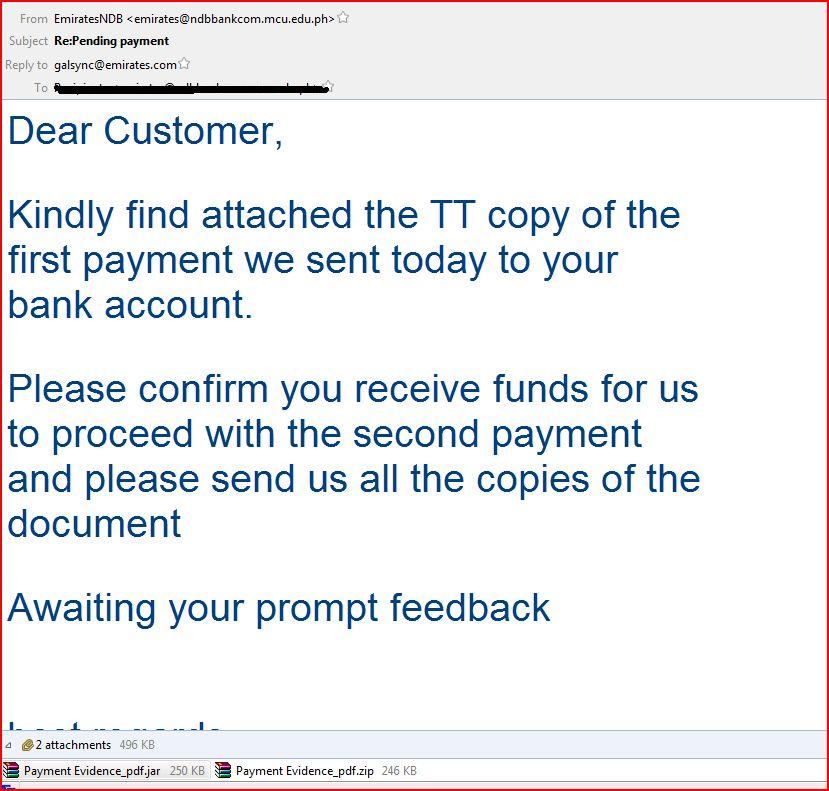
EMAIL DATA
From: EmiratesNDB <emirates@ndbbankcom.mcu.edu.ph>
Date: Thu, 12 Jan 2017 03:34:29 -0800
Reply-To: galsync@emirates.com
Message-Id: <20170112121157.9D7084CC1D1@troy.mcu.edu.ph>
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.5
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: attachment Payment Evidence_pdf.jar blocked because of
filter rule: .jar$ action: REJECT
Content-Transfer-Encoding: quoted-printable
Content-Description: Mail message body
THE ATTACHMENT
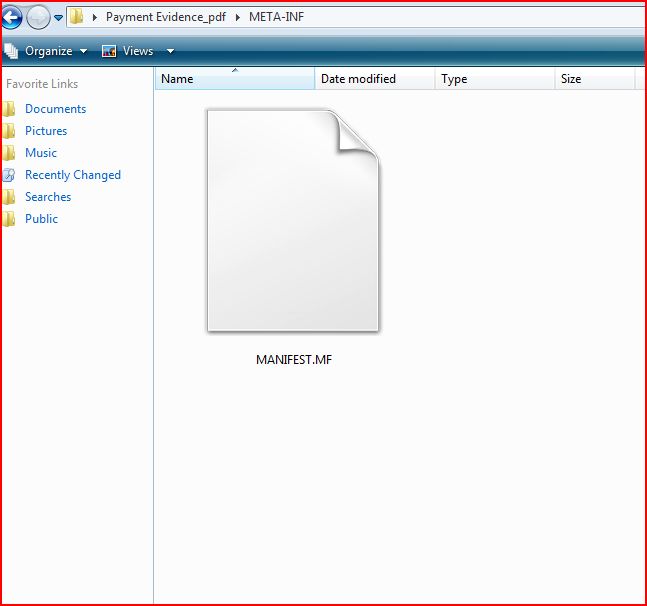
ATTACHMENT AND EXTRACTED FILE
MD5 hash : 3173715D5B52BEE523ADECA13F30C4ED
SHA1 hash : A6776AABAE95B1305C3B0C83EF82D507FEB56CDE
SHA256 hash : D53C08C9FE6C5D63AC86972406CF67D8C4DB25269B46705EEA433F481B7F27D9
File Name : Payment Evidence_pdf 251 KB (257,914 bytes)
TRAFFIC
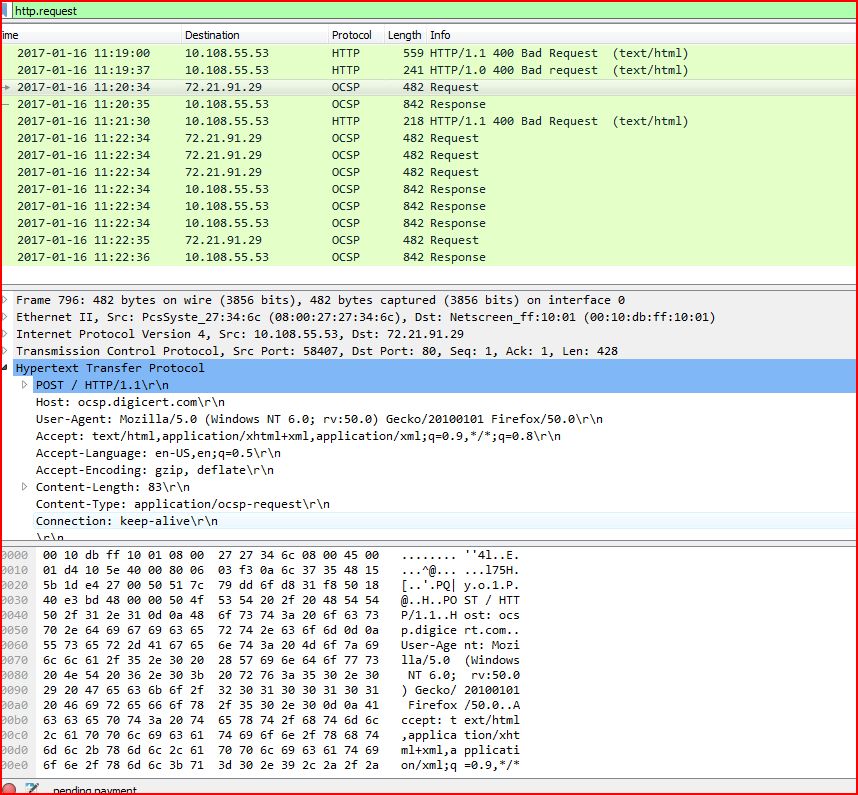
ASSOCIATED URLS
2017-01-16 11:19:00 10.108.55.53 HTTP 559 HTTP/1.1 400 Bad Request (text/html)
2017-01-16 11:19:37 10.108.55.53 HTTP 241 HTTP/1.0 400 Bad request (text/html)
2017-01-16 11:20:34 72.21.91.29 OCSP 482 Request
2017-01-16 11:20:35 10.108.55.53 OCSP 842 Response
2017-01-16 11:20:35 10.108.55.53 OCSP 842 Response
2017-01-16 11:21:30 10.108.55.53 HTTP 218 HTTP/1.1 400 Bad Request (text/html)
2017-01-16 11:22:34 72.21.91.29 OCSP 482 Request
2017-01-16 11:22:34 72.21.91.29 OCSP 482 Request
2017-01-16 11:22:34 72.21.91.29 OCSP 482 Request
2017-01-16 11:22:34 10.108.55.53 OCSP 842 Response
2017-01-16 11:22:34 10.108.55.53 OCSP 842 Response
2017-01-16 11:22:34 10.108.55.53 OCSP 842 Response
2017-01-16 11:22:35 72.21.91.29 OCSP 482 Request
2017-01-16 11:22:36 10.108.55.53 OCSP 842 Response
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES
ZIP archive of the malware: [16 Jan 2017] – [Pending payment.rar] 629 KB (644,461 bytes)
- 27351-1484220970-379799.eml 674 KB (691,064 bytes)
- MANIFEST.MF 212 bytes (212 bytes)
- Pending payment.pcapng 332 KB (340,264 bytes)
