
[02 Jan 2017] – [Payment Slip Malware] – SUBJECT : [Payment Slip]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Payment slip”.
ASSOCIATED FILES
ZIP archive of the malware: [02 Jan 2017] – [Payment slip Malware] 656 KB (672,101 bytes)
- 10617-1482957018-106878.eml 477 KB (488,951 bytes)
- META-INF 212 bytes (212 bytes)
- o 60.2 KB (61,696 bytes)
- VORmaSQ 230 KB (236,064 bytes)
THE EMAIL
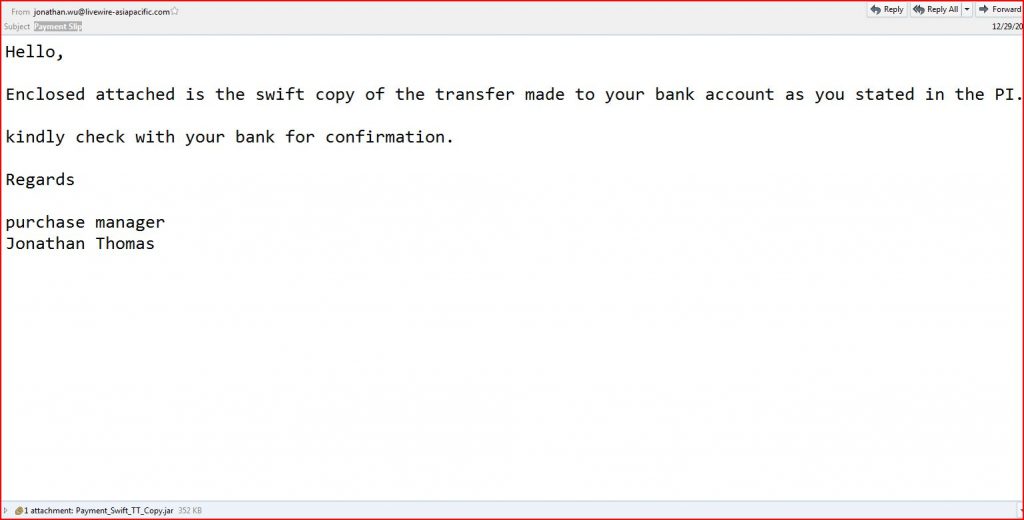
EMAIL DATA
From: jonathan.wu@livewire-asiapacific.com
Subject: Payment Slip
User-Agent: Horde Application Framework 5
MIME-Version: 1.0
X-PPP-Message-ID: <20161228203013.14260.35454@so199-35.asiawhere.com>
X-PPP-Vhost: livewire-asiapacific.com
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.5
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: attachment Payment_Swift_TT_Copy.jar blocked because of
filter rule: .jar$ action: REJECT
Content-Type: multipart/mixed; boundary=”=_oemNhRqqS84aejn1Nl62KCQ”
Content-Type: text/plain; charset=utf-8; format=flowed; DelSp=Yes
Content-Disposition: inline
THE ATTACHMENT
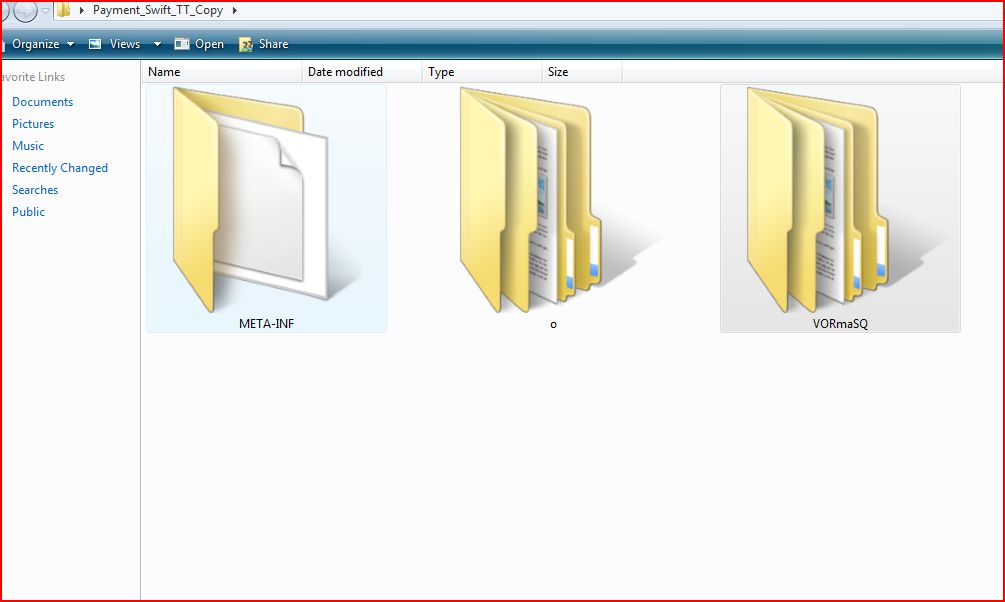


ATTACHMENT AND EXTRACTED FILE
SHA1 hash : 377353E15447D5052FF313305F55B3306507C565
SHA256 hash : 9FFB67625B3529C0D25DB0FD7B0E978064C41F3227C320CA3456773F42AD1821
File Name : Payment_Swift_TT_Copy.jar 352 KB (360,567 bytes)
SHA1 hash : E83EE9AB5E25957D26DF27990F3835729DBC4BD1
SHA256 hash : 8122CEEC347B126E28468F30CDE5CCC0F28A2F9229EEE8F5C8438E6C9A40F102
File Name : MANIFEST.MF 212 bytes (212 bytes)
SHA1 hash : 54D487E5B75BFC49D4ACD63D954766FBD51A9CF2
SHA256 hash : F2EBA4681973C898F6047256E5C09C51B35DD3C2D7469E731C9E1C02986C9747
File Name : a.s 60.2 KB (61,696 bytes)
SHA1 hash : 52BDE1F3B9C8E6A458ED17FFD08AA1D640343F71
SHA256 hash : C11C59815BE5D6533366A45E556803954F2EBD8C5B0CD25BF372DA95016511FC
File Name : elyBQO.zDf 230 KB (236,064 bytes)
TRAFFIC
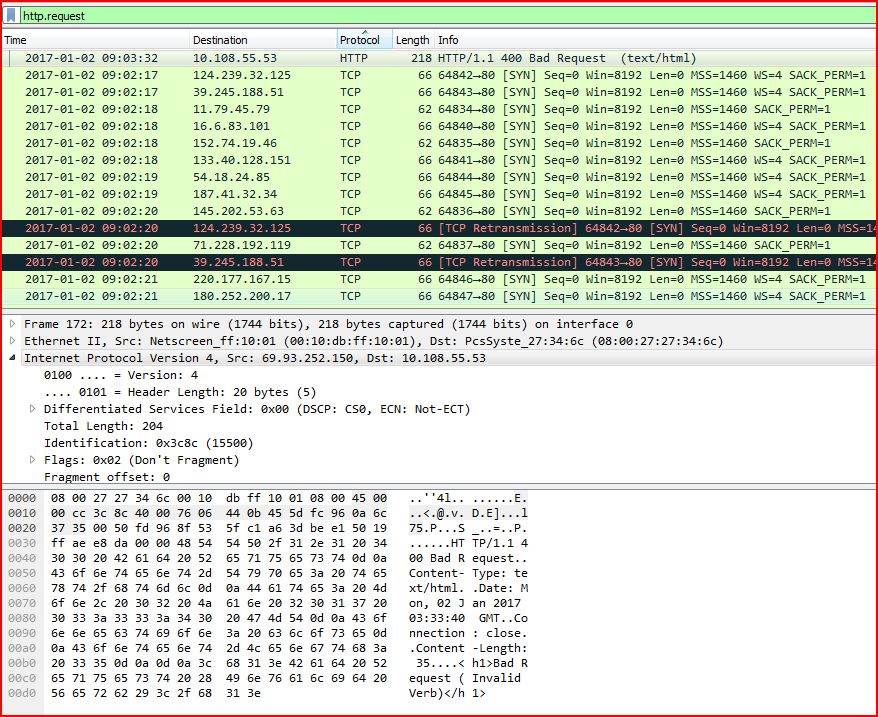
ASSOCIATED URLS
2017-01-02 09:03:32 10.108.55.53 HTTP 218 HTTP/1.1 400 Bad Request (text/html)
2017-01-02 09:02:17 124.239.32.125 TCP 66 64842→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-02 09:02:17 39.245.188.51 TCP 66 64843→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-02 09:02:18 11.79.45.79 TCP 62 64834→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 SACK_PERM=1
2017-01-02 09:02:18 16.6.83.101 TCP 66 64840→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-02 09:02:18 152.74.19.46 TCP 62 64835→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 SACK_PERM=1
2017-01-02 09:02:18 133.40.128.151 TCP 66 64841→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-02 09:02:19 54.18.24.85 TCP 66 64844→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-02 09:02:19 187.41.32.34 TCP 66 64845→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-02 09:02:20 145.202.53.63 TCP 62 64836→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 SACK_PERM=1
2017-01-02 09:02:20 124.239.32.125 TCP 66 [TCP Retransmission] 64842→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-02 09:02:20 71.228.192.119 TCP 62 64837→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 SACK_PERM=1
2017-01-02 09:02:20 39.245.188.51 TCP 66 [TCP Retransmission] 64843→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-02 09:02:21 220.177.167.15 TCP 66 64846→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-02 09:02:21 180.252.200.17 TCP 66 64847→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
IMAGES
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES
ZIP archive of the malware: [02 Jan 2017] – [Payment slip Malware] 656 KB (672,101 bytes)
- 10617-1482957018-106878.eml 477 KB (488,951 bytes)
- META-INF 212 bytes (212 bytes)
- o 60.2 KB (61,696 bytes)
- VORmaSQ 230 KB (236,064 bytes)
