
[26-12-2016] – [PAYMENT MALWARE] – SUBJECT: [Urgent]
Comodo Threat Research Labs (CTRL) identified a new phishing email attack with a malware file attachment. It is a “Payment Malware” with subject titled: “Urgent” and it is targeted at email users.
Malware authors have created a new type of JavaScript file malware named as “Urgent” malware.
ASSOCIATED FILES:
- ZIP archive of the pcap: payment.rar 628 KB (642,680 bytes)
- ZIP archive of the malware: urjent.rar 10.0 KB (10,320 bytes)
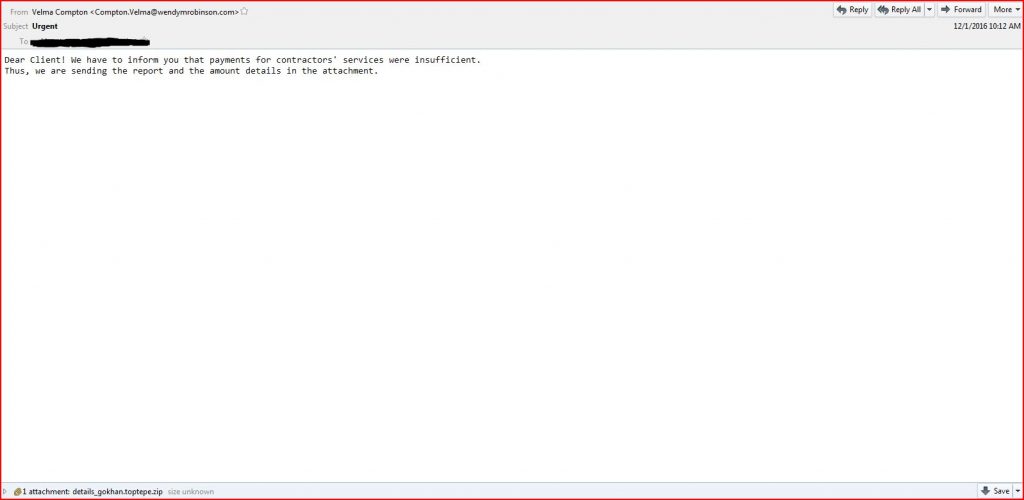
Below is an image of the “Urgent” email. The targeted victim receives an email with the following message:
Dear Client! We have to inform you that payments for contractors’ services were insufficient.
Thus, we are sending the report and the amount details in the attachment.
However, there is an encrypted script running behind the scenes which stays invisible when the infected user opens the mail and the attachment. The malware is designed to download a malicious file on to the infected user’s device which remains unremovable. This could help the cyber criminal track and access data relating to the victim’s identity and credentials.
THE EMAIL:
EMAIL DATA:
- Subject: Urgent
- X-PHP-Originating-Script: 9028914:Smail.class.php
- From: Velma Compton <Compton.Velma@wendymrobinson.com>
- Date: Thu, 01 Dec 2016 11:42:04 +0700
- MIME-Version: 1.0
- Message-Id: <3060614686.417985.09356.SMail@giresun.edu.tr>
- X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.4
- X-KORUMAIL-Result: Miscellaneous filter match
- X-KORUMAIL-Reason: Foxhole.JS_Zip_1.UNOFFICIAL
- Content-Type: multipart/related; boundary=4556e12049c0355030f210a75b77ba8c
THE ATTACHMENT
The attachment is a “.zip file”, which is actually a “.js” JavaScript file.
[SCREENSHOT of the java script file]
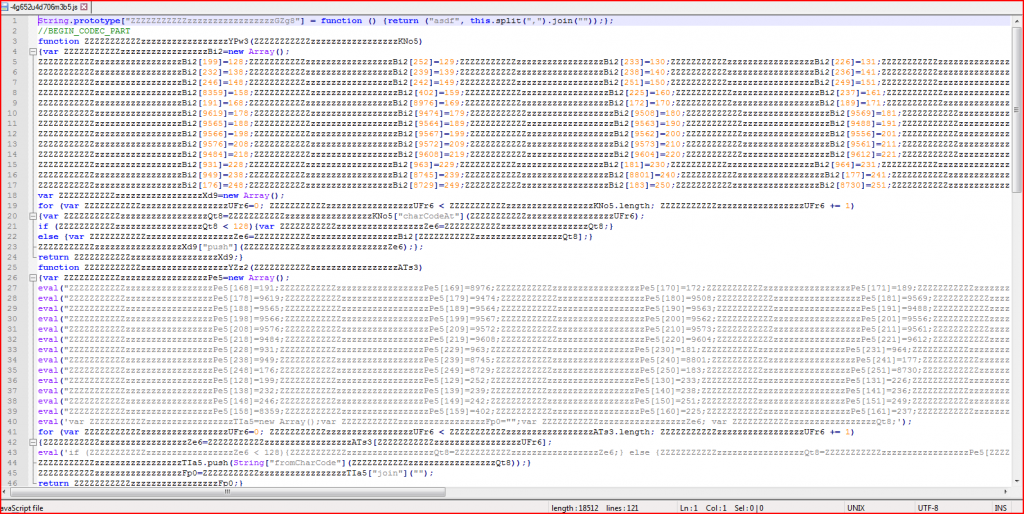
ATTACHMENT AND EXTRACTED .JS FILE:
- File Name : details_gokhan.toptepe.zip 4.0 KB (4,096 bytes)
- SHA-1 Value : 7909AE2D9625C02C493D661F40ED5F4BC50C80DB
- SHA-256 Value:3a496e67b33420c86515f42faffc84fe75f5594b9325c9d3a6f61106c2d82996
- MD5 Value : c7d0ecdf115bd56d6b0e619a3542e2d1
- File Name : -4g652u4d706m3b5.js 19.0 KB (18,512 bytes)
- SHA-1 Value : ADBD9AD9248D36B3A259D0AF82366B171E48F9AB
- SHA-256 Value: aae5a19aa8882fc74cf51ffd241be1913222fe37291e7c55a67f3978d40a27c8
- MD5 Value : 01f9c5c2b7d3142f6c9b1be9526410cf
TRAFFIC:
When the email attachment is opened and executed, the file captures the HTTP Request traffic and finds the host of the malicious file URL.
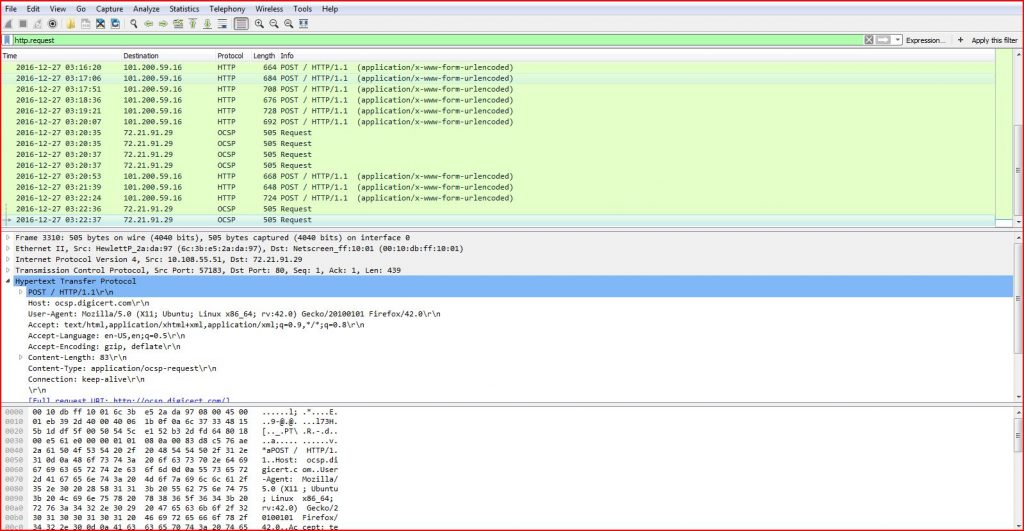
ASSOCIATED URLS:
- 2016-12-27 03:11:03 101.200.59.16 HTTP 704 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:11:48 101.200.59.16 HTTP 676 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:12:34 101.200.59.16 HTTP 696 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:13:19 101.200.59.16 HTTP 716 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:14:04 101.200.59.16 HTTP 700 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:14:50 101.200.59.16 HTTP 724 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:15:35 101.200.59.16 HTTP 680 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:16:20 101.200.59.16 HTTP 664 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:17:06 101.200.59.16 HTTP 684 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:17:51 101.200.59.16 HTTP 708 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:18:36 101.200.59.16 HTTP 676 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:19:21 101.200.59.16 HTTP 728 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:20:07 101.200.59.16 HTTP 692 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:20:35 72.21.91.29 OCSP 505 Request
- 2016-12-27 03:20:35 72.21.91.29 OCSP 505 Request
- 2016-12-27 03:20:37 72.21.91.29 OCSP 505 Request
- 2016-12-27 03:20:37 72.21.91.29 OCSP 505 Request
- 2016-12-27 03:20:53 101.200.59.16 HTTP 668 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:21:39 101.200.59.16 HTTP 648 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:22:24 101.200.59.16 HTTP 724 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2016-12-27 03:22:36 72.21.91.29 OCSP 505 Request
- 2016-12-27 03:22:37 72.21.91.29 OCSP 505 Request
IMAGES:
FILES DOWNLOADED BY THE INFECTED HOST:
- File Name : d3d9caps.dat 1.0Kb (680 bytes)
- SHA1 Value : DE5E01A0801CB95CA0FA7398CDB20796F208F3DF
- SHA256Value : 09e200abf0dbcad13c2c4c7c9627e8567d25d29406fc6a66c6226637020f9548
- MD5 Value : 266cc233b801df1899e288852743982b
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
- ZIP archive of the pcap: payment.rar 628 KB (642,680 bytes)
- ZIP archive of the malware: urjent.rar 10.0 KB (10,320 bytes)
