
[07 June 2017] – [ MPC CUSTOMER SUPPORT MALWARE] – SUBJECT : [Order #67506]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware link, and spread to email user with subject “Order #67506”.
ASSOCIATED FILES:
RAR archive of the malware: [07 June 2017] – [MPC Customer Support Malware] – 608 KB (622,592 bytes)
Email : 14089-1496805136-616072 116KB(118,784 bytes)
Malware Link Dropped File : ok.exe 404 KB (413,696 bytes)
Dropped file : DOC8556841068-PDF.vbs 88.0 KB (90,112 bytes)
THE EMAIL:
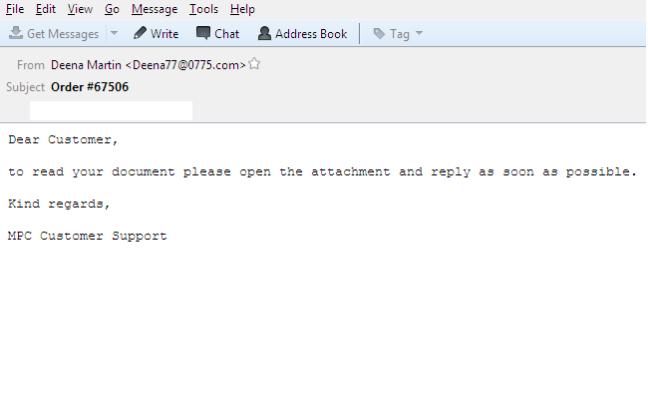
EMAIL DATA:
Received: from unknown (HELO ?0.0.0.0?) (123.21.159.17)
by 0 with SMTP; 7 Jun 2017 03:12:17 -0000
Received: from ftzpj ([226.149.20.129]) by 0775.com with MailEnable ESMTP; Wed, 7 Jun 2017 10:12:17 +0700
Received: (qmail 67506 invoked by uid 675); 7 Jun 2017 10:12:13 +0700
From: Deena Martin <Deena77@0775.com>
Subject: Order #67506
Date: Wed, 7 Jun 2017 10:12:17 +0700
Message-ID: <67506791814934.9711.qmail@wgwkjm>
Mime-Version: 1.0
Content-Type: multipart/mixed; boundary= “wmiyvb_sahnlros_yzvj”
–wmiyvb_sahnlros_yzvj
Content-Type: text/plain; charset=US-ASCII
PHISHING LINK – DROPPED FILE:

DROPPED FILE:
EXTRACTED FILE DETAILS FOR DOC8556841068-PDF.vbs:
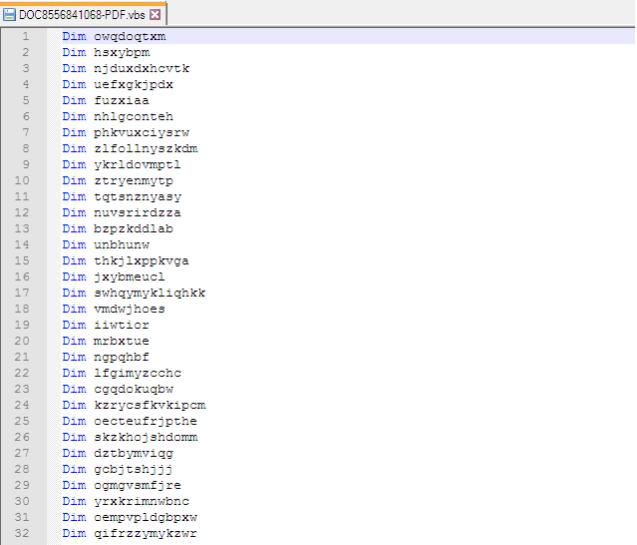
EXTRACTED FILE DETAILS FOR Ok.exe:

File Name : DOC8556841068-PDF.vbs
MD5 hash : fb83d46c96706dc3ebf55baee5d4c09f
SHA1 hash : 441db65c06e92b771aafc6c872ebb7ca84bf1498
SHA256 hash : 503502f37b498d5764f7e46e273c3e6a4be4dc35b445432fa6266bd21a8a0b2d
File Name : ok.exe 404 KB (413,696 bytes)
MD5 hash : a06153df50c6fa82869e2a2545930b67
SHA1 hash : 149a0d36bae896d6bda8ebdb35efa2d80ca4f7a2
SHA256 hash : b5619182dec4091715b4f6c6b6413803c8661ee62cffd81b946675d3ab997c6d
TRAFFIC:
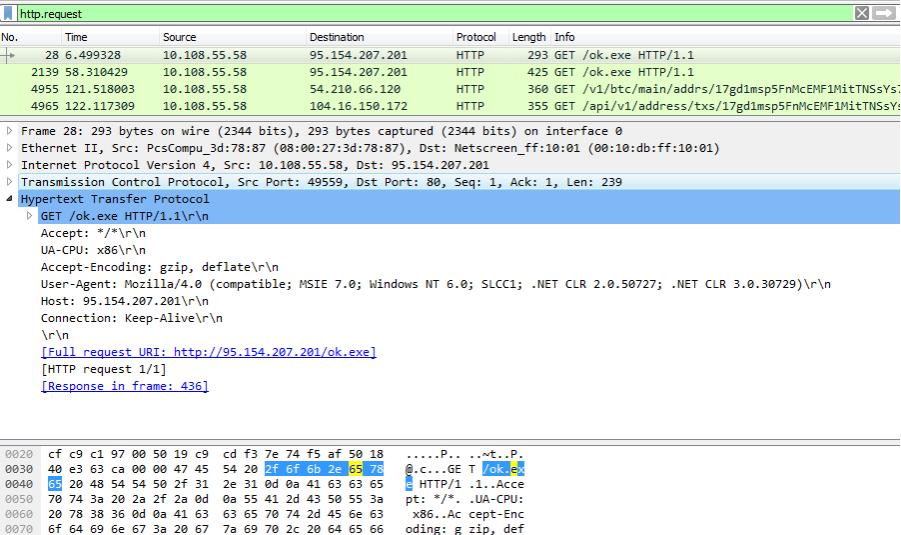
ASSOCIATED URLS:
- 28 6.499328 10.108.55.58 95.154.207.201 HTTP 293 GET /ok.exe HTTP/1.1
- 2139 58.310429 10.108.55.58 95.154.207.201 HTTP 425 GET /ok.exe HTTP/1.1
- 4955 121.518003 10.108.55.58 54.210.66.120 HTTP 360 GET /v1/btc/main/addrs/17gd1msp5FnMcEMF1MitTNSsYs7w7AQyCt?_=1496800547801 HTTP/1.1
- 4965 122.117309 10.108.55.58 104.16.150.172 HTTP 355 GET /api/v1/address/txs/17gd1msp5FnMcEMF1MitTNSsYs7w7AQyCt?_=1496800548919 HTTP/1.1
VALKYRIE FOR REFERENCE:
File name : ok
https://valkyrie.comodo.com/get_info?sha1=149a0d36bae896d6bda8ebdb35efa2d80ca4f7a2
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
RAR archive of the malware: [07 June 2017] – [Microsoft Account Spoofing Malware] – 608 KB (622,592 bytes)
- Email : 14089-1496805136-616072 116KB(118,784 bytes)
- Malware Link Dropped File : ok.exe 404 KB (413,696 bytes)
- Dropped file : DOC8556841068-PDF.vbs 88.0 KB (90,112 bytes)
