
[22 May 2017] – [Microsoft Account Spoofing Malware] – SUBJECT : [14806 irbpqk]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware link, and spread to email user with subject “14806 irbpqk”.
ASSOCIATED FILES:
RAR archive of the malware: [22 May 2017] – [Microsoft Account Spoofing Malware] – 232 KB (237,829 bytes)
Email : 14007-1494939375-945685.eml 5 KB (5000 bytes)
Malware Link Dropped File : 2 440 KB (442,000 bytes)
Dropped file : 1016.js 14 KB (14,000 bytes)
THE EMAIL:
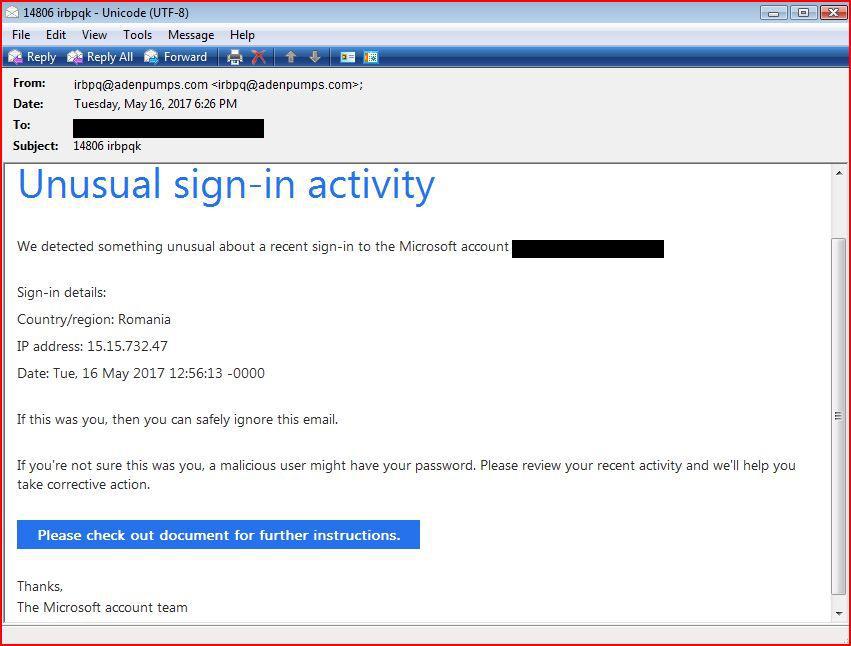
EMAIL DATA:
Received: from unknown (HELO jazztel.es) (95.22.39.221) by 0 with SMTP;
16 May 2017 12:56:17 -0000
Message-ID: <149493937300.836.8143336677651806863@jazztel.es>
Subject: 14806 irbpqk
MIME-Version: 1.0
Reply-To: <irbpq@adenpumps.com>
From: irbpq@adenpumps.com
Importance: High
X-Envelope-Sender: irbpq@jazztel.es
X-KORUMAIL-QueueId: 14007-1494939375-945685
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.6.3
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: E-mail is discarded and quarantined because of RBL
blacklisted.
Content-Transfer-Encoding: 8bit
Content-Type: text/html; charset=UTF-8
PHISHING LINK – DROPPED FILE:
DROPPED FILE:
EXTRACTED FILE DETAILS FOR 1016.js:
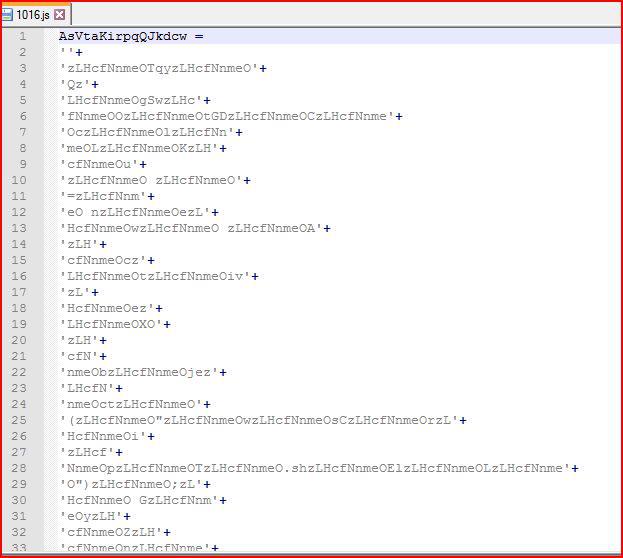
EXTRACTED FILE DETAILS FOR 2:

File Name : 1016.js 14 KB (14,000 bytes)
MD5 hash : fb72f98d469aff3ced617ced3c2e9864
SHA1 hash : 5d3f11845e3c715af4c1c88b99c0d8f90c49924b
SHA256 hash : 023c57c77863820bb0674606cc5c8a94e32318610bdb6ad378f047f13787c0c9
File Name : 2 440 KB (440,000 bytes)
MD5 hash : cc52ba8f6f250704f6ed9139a242382f
SHA1 hash : 0dddca0add163af6238f2b68bc25a88ada1f35d5
SHA256 hash : b076d68a304f781505c27fd7e6b2c7d1d247aa676f5fda360c86718ce0920712
TRAFFIC:
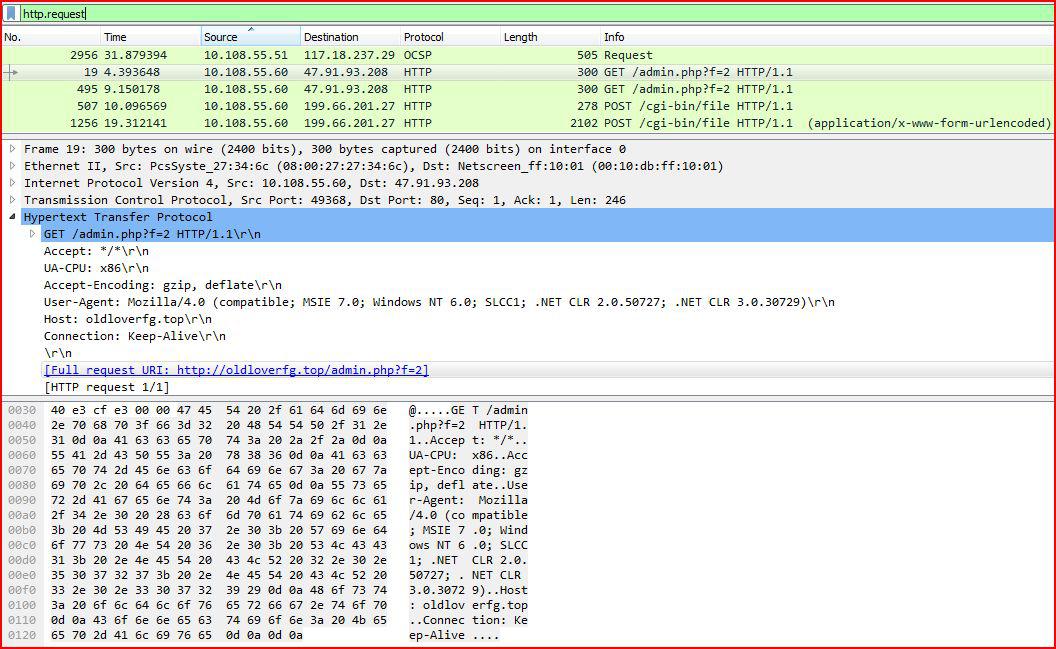
ASSOCIATED URLS:
- 19 4.393648 10.108.55.60 47.91.93.208 HTTP 300 GET /admin.php?f=2 HTTP/1.1
- 495 9.150178 10.108.55.60 47.91.93.208 HTTP 300 GET /admin.php?f=2 HTTP/1.1
- 507 10.096569 10.108.55.60 199.66.201.27 HTTP 278 POST /cgi-bin/file HTTP/1.1
- 1256 19.312141 10.108.55.60 199.66.201.27 HTTP 2102 POST /cgi-bin/file HTTP/1.1 (application/x-www-form-urlencoded)
- 2956 31.879394 10.108.55.51 117.18.237.29 OCSP 505 Request
VALKYRIE FOR REFERENCE:
File name : 2
https://valkyrie.comodo.com/get_info?sha1=0dddca0add163af6238f2b68bc25a88ada1f35d5
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
RAR archive of the malware: [22 May 2017] – [Microsoft Account Spoofing Malware] – 232 KB (237,829 bytes)
- Email : 14007-1494939375-945685.eml 5 KB (5000 bytes)
- Malware Link Dropped File : 2 440 KB (442,000 bytes)
- Dropped file : 1016.js 14 KB (14,000 bytes)
