
[15 Jan 2017] – [Inquity sales Malware] – SUBJECT: [Re: Inquity sales]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Inquity sales”.
ASSOCIATED FILES
ZIP archive of the malware: [15 Jan 2017] – [Inquitysales.rar] 2.22 MB (2,333,285 bytes)
- 22833-1484219783-410528.eml 340 KB (348,294 bytes)
- New Order.exe 505 KB (517,632 bytes)
- Inquitysales.pcapng 4.94 MB (5,183,120 bytes)
THE EMAIL
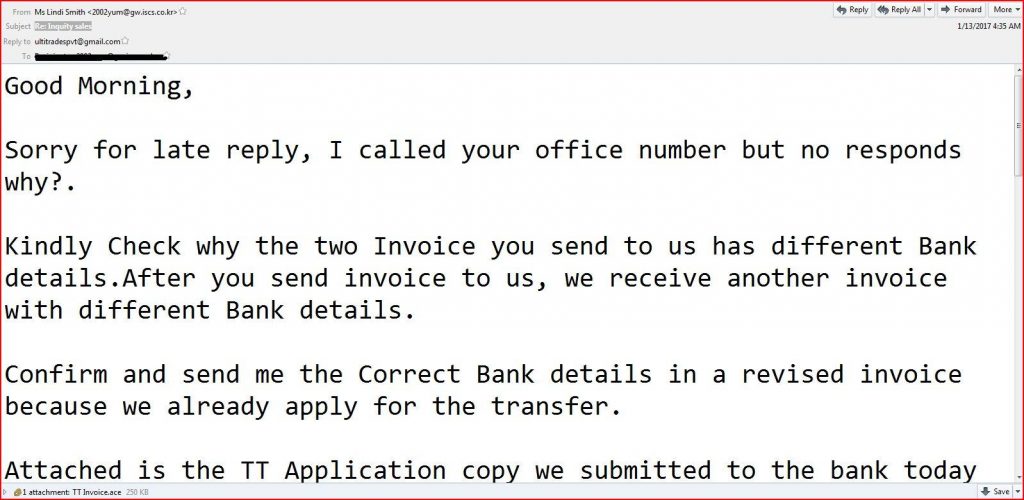
EMAIL DATA
From: Ms Lindi Smith <2002yum@gw.iscs.co.kr>
Date: Thu, 12 Jan 2017 11:05:42 -1200
Reply-To: ultitradespvt@gmail.com
X-TERRACE-SPAMMARK: NO (SR:17.20) (by Terrace)
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.5
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: attachment TT Invoice.ace blocked because of filter rule:
.ace$ action: REJECT
Content-Type: multipart/mixed;
Content-Transfer-Encoding: quoted-printable
Content-Description: Mail message body
THE ATTACHMENT
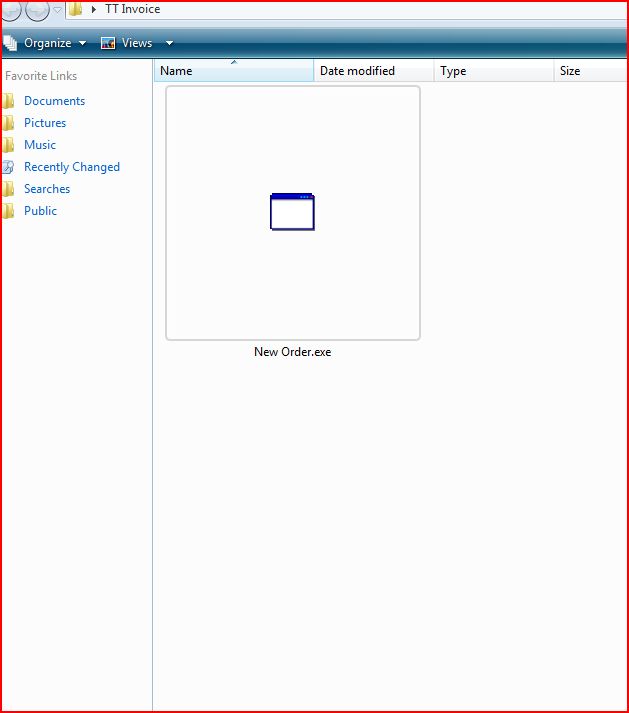
ATTACHMENT AND EXTRACTED FILE
MD5 hash : 0E25F2FF58D6DB331E7533C54D649792
SHA1 hash : 4AAD51DDAC437FD8CEB9B7A1047BC3B504A337AB
SHA256 hash : 9325504DF5C328E0F131C34BD99E52DBDC273ABDC244F249DD6BE9FBF7B5AEE5
File Name : TT Invoice 505 KB (517,632 bytes)
TRAFFIC
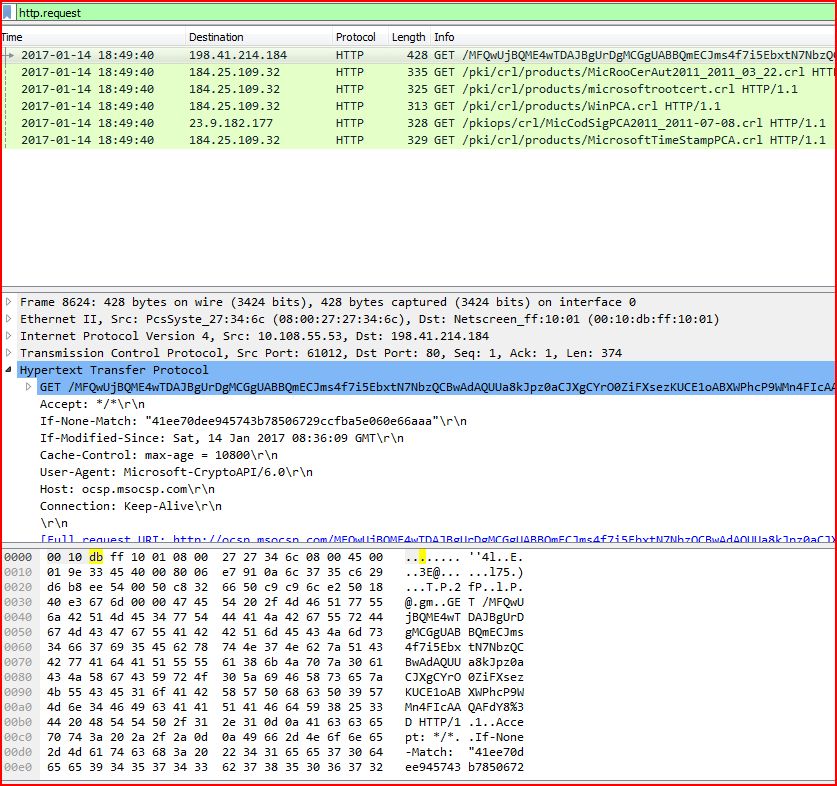
ASSOCIATED URLS
2017-01-14 18:49:40 198.41.214.184 HTTP 428 GET /MFQwUjBQME4wTDAJBgUrDgMCGgUABBQmECJms4f7i5EbxtN7NbzQCBwAdAQUUa8kJpz0aCJX gCYrO0ZiFXsezKUCE1oABXWPhcP9WMn4FIcAAQAFdY8% 3D HTTP/1.1
2017-01-14 18:49:40 184.25.109.32 HTTP 335 GET /pki/crl/products/MicRooCerAut2011_2011_03_22.crl HTTP/1.1
2017-01-14 18:49:40 184.25.109.32 HTTP 325 GET /pki/crl/products/microsoftrootcert.crl HTTP/1.1
2017-01-14 18:49:40 184.25.109.32 HTTP 313 GET /pki/crl/products/WinPCA.crl HTTP/1.1
2017-01-14 18:49:40 23.9.182.177 HTTP 328 GET /pkiops/crl/MicCodSigPCA2011_2011-07-08.crl HTTP/1.1
2017-01-14 18:49:40 184.25.109.32 HTTP 329 GET /pki/crl/products/MicrosoftTimeStampPCA.crl HTTP/1.1
VALKYRIE LINK FOR REFERENCE
https://valkyrie.comodo.com/get_info?sha1=262d6f442db049f92034dcb95133f050473ed16d
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES
ZIP archive of the malware: [15 Jan 2017] – [Inquitysales.rar] 2.22 MB (2,333,285 bytes)
- 22833-1484219783-410528.eml 340 KB (348,294 bytes)
- New Order.exe 505 KB (517,632 bytes)
- Inquitysales.pcapng 4.94 MB (5,183,120 bytes)
