
[24 Dec 2016] – [Income Tax Malware] – SUBJECT : [Attention required]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Attention required”.
ASSOCIATED FILES
ZIP archive of the malware: [24 Dec 2016] – [Income Tax Malware] 145 KB (149,458 bytes)
- 373-1481151568-739244.eml (6,599 bytes)
- ~B3475MMI213Z9XUJ96A0V0D.js (33,430 bytes)
- KHYnZx4nz.zk (274,432 bytes)
THE EMAIL
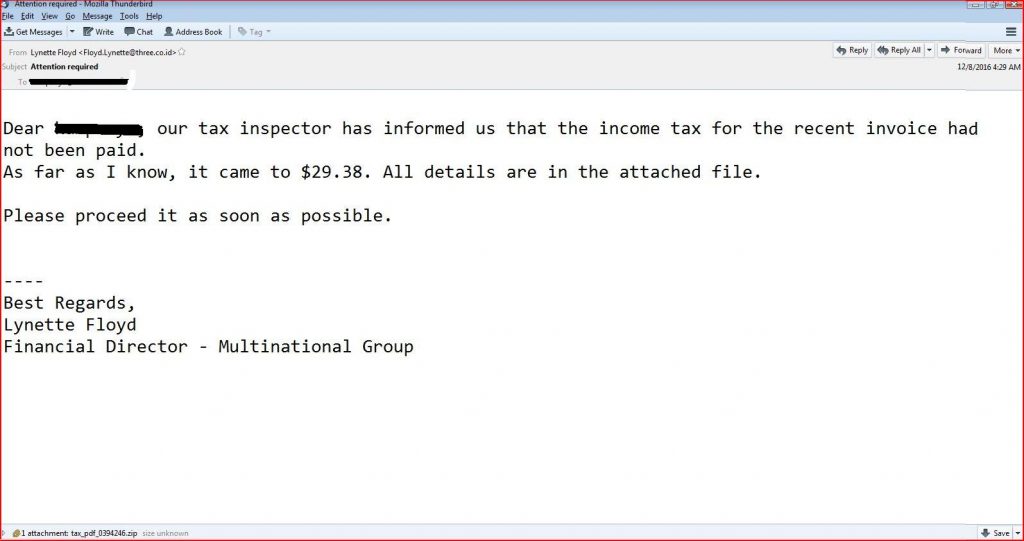
EMAIL DATA
From: Lynette Floyd <Floyd.Lynette@three.co.id>
Subject: Attention required
Date: Thu, 08 Dec 2016 05:59:21 +0700
MIME-Version: 1.0
Message-Id: <3259946730.089512.14507.server@isimtescil.net>
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.4
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason:
Content-Type: multipart/related; boundary=1d9e12660212874dfa1c3a4f4ff07a8a
–1d9e12660212874dfa1c3a4f4ff07a8a
Content-Type: text/plain;
charset=utf-8
Content-Transfer-Encoding: base64
Content-Type: application/zip; name=”tax_pdf_0394246.zip”
Content-Transfer-Encoding: base64
Content-Disposition: attachment; filename=”tax_pdf_0394246.zip”
THE ATTACHMENT
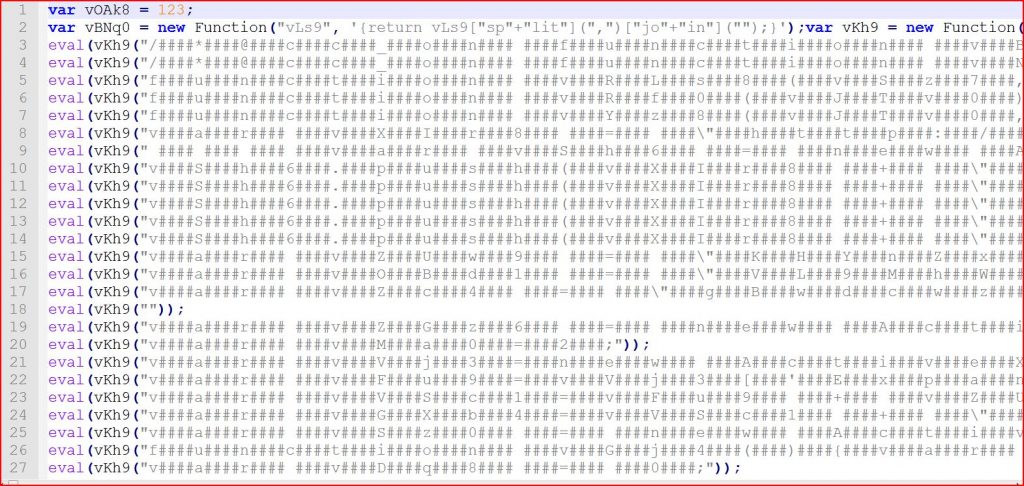
ATTACHMENT AND EXTRACTED .JS FILE
File Name : tax_pdf_0394246.zip ((3,837 bytes))
SHA1 hash : FB247047A7A6F0A4C742AAE2BEBBDF2DEC01F82A
SHA256 hash : 93F9587D5A4D289A72D3694A85B6FE5B0F1509F160F1F54A92124CE023C124C7
MD5 Value : 257dfe3f3133f08c3aa3f5b89ade8880
File Name : ~B3475MMI213Z9XUJ96A0V0D.js (33,430 bytes)
SHA1 hash : c72fdcb4718373f1218dd42259ba41edc36d5d58
SHA256 hash : a173de0772c21697aea83dda21006898b9292c64dab1588a9f05bb838b6080c2
MD5 Value : 5f1f7feba3ab07f47075d76418889c08
TRAFFIC
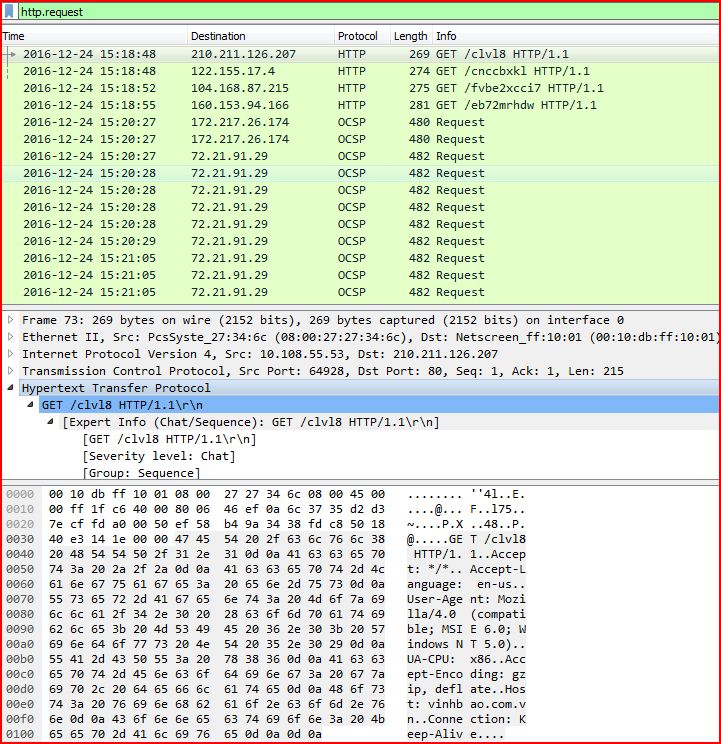
ASSOCIATED URLS
2016-12-24 15:18:48 10.108.55.53 64928 80 GET /clvl8 HTTP/1.1 73
2016-12-24 15:18:48 10.108.55.53 64929 80 GET /cnccbxkl HTTP/1.1 86
2016-12-24 15:18:52 10.108.55.53 64934 80 GET /fvbe2xcci7 HTTP/1.1 265
2016-12-24 15:18:55 10.108.55.53 64938 80 GET /eb72mrhdw HTTP/1.1 290
2016-12-24 15:20:27 10.108.55.53 65039 80 Request 1005
2016-12-24 15:20:27 10.108.55.53 65041 80 Request 1006
2016-12-24 15:20:27 10.108.55.53 65040 80 Request 1025
2016-12-24 15:20:28 10.108.55.53 65042 80 Request 1071
2016-12-24 15:20:28 10.108.55.53 65040 80 Request 1072
2016-12-24 15:20:28 10.108.55.53 65042 80 Request 1136
2016-12-24 15:20:28 10.108.55.53 65040 80 Request 1137
2016-12-24 15:20:29 10.108.55.53 65042 80 Request 1161
2016-12-24 15:21:05 10.108.55.53 64972 80 Request 5995
2016-12-24 15:21:05 10.108.55.53 64972 80 Request 6019
2016-12-24 15:21:05 10.108.55.53 64974 80 Request 6025
2016-12-24 15:21:05 10.108.55.53 64975 80 Request 6041
2016-12-24 15:21:19 10.108.55.53 64972 80 Request 6228
IMAGES
FILES DOWNLOADED BY THE INFECTED HOST
File name : KHYnZx4nz.zk (187,110 bytes)
SHA1 hash : f8b5c98e21b2a05fd83ba772091a2ed8bbf1bc12
SHA256 hash : e407a9b7adba2587150d66ec638a4a9b64d57ac23b320c0f7df02668479c61da
MD5 Value : a88491a1e76fd8e433adad53bd330d31
VALKYRIE LINK FOR REFERENCE
https://valkyrie.comodo.com/get_info?sha1=f8b5c98e21b2a05fd83ba772091a2ed8bbf1bc12
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES
ZIP archive of the malware: [24 Dec 2016] – [Income Tax Malware] 145 KB (149,458 bytes)
- 373-1481151568-739244.eml (6,599 bytes)
- ~B3475MMI213Z9XUJ96A0V0D.js (33,430 bytes)
- KHYnZx4nz.zk (274,432 bytes)
