
[06 Feb 2017] – [HSBC Payment Malware] – SUBJECT : [Payment Advice – Advice Ref :[G51958526665] / Priority payment / Customer Ref:[150000495]]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Payment Advice – Advice Ref :[G51958526665] / Priority payment / Customer Ref:[150000495]”.
ASSOCIATED FILES:
ZIP archive of the malware: [06 Feb 2017] – [HSBC Payment.rar] 638 KB (653,721 bytes)
- 7433-1486351279-378833.eml 52.0 KB (53,248 bytes)
- HSBC_256474775883748848384939_PDF.jar 251 KB (257,995 bytes)
- Hsbc.pcapng 243 KB (249,084 bytes)
THE EMAIL:
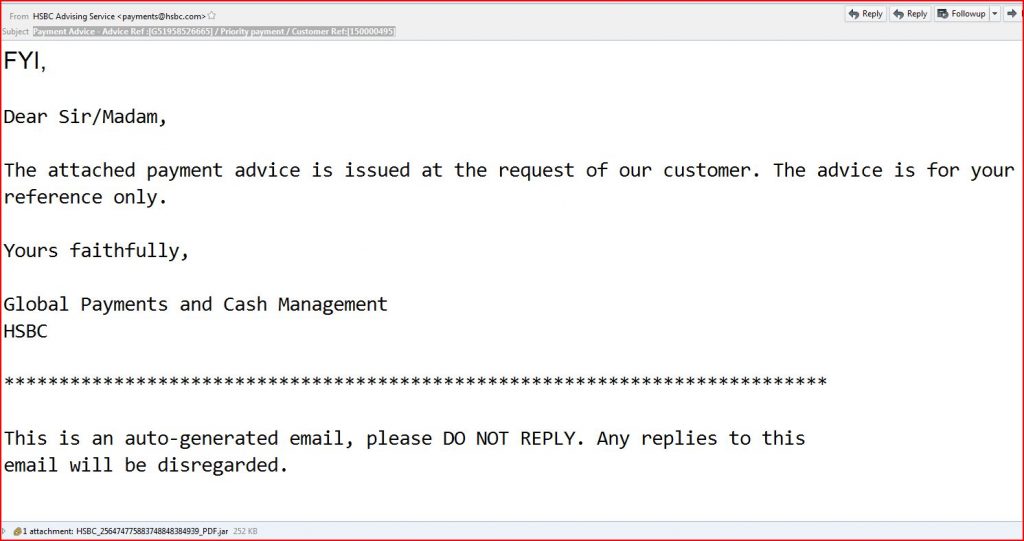
EMAIL DATA:
From: HSBC Advising Service <payments@hsbc.com> User-Agent: Horde Application Framework 5MIME-Version: 1.0
X-PPP-Message-ID: <20170206032117.3320.53018@plesk4.hipernet.es>
X-PPP-Vhost: arrobaes.com
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.5
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: attachment HSBC_256474775883748848384939_PDF.jar blocked
because of filter rule: .jar$ action: DISCARD
Content-Type: multipart/mixed; boundary=”=_hGMGpIFaJ5Ct0XZSs7TelnI”
Content-Transfer-Encoding: 8bit
THE ATTACHMENT:
EXTRACTED FILE DETAILS:
File Name : HSBC_256474775883748848384939_PDF.jar
MD5 hash : FE49C487C934103373C1B072E2FCE39C
SHA1 hash : A6E68FE1576EA96D1781FDA59787568D38A83620
SHA256 hash : D9DC889CA9637679A0E5A34A865BCB96E7F0CBA33AB6ECCBD015659386C25BC2
File Name : MANIFEST.MF 299 bytes (299 bytes)
MD5 hash : 5E435937F44E9D9040E766FEE6EBCD27
SHA1 hash : 0CABD3BE088BB45F9543DBC69795ADF4E10A22C3
SHA256 hash : FFB2E40FF99A1711310FB799B70EA2A38A094AFCC0AB0ABC6C8156A0421AC62C
TRAFFIC:
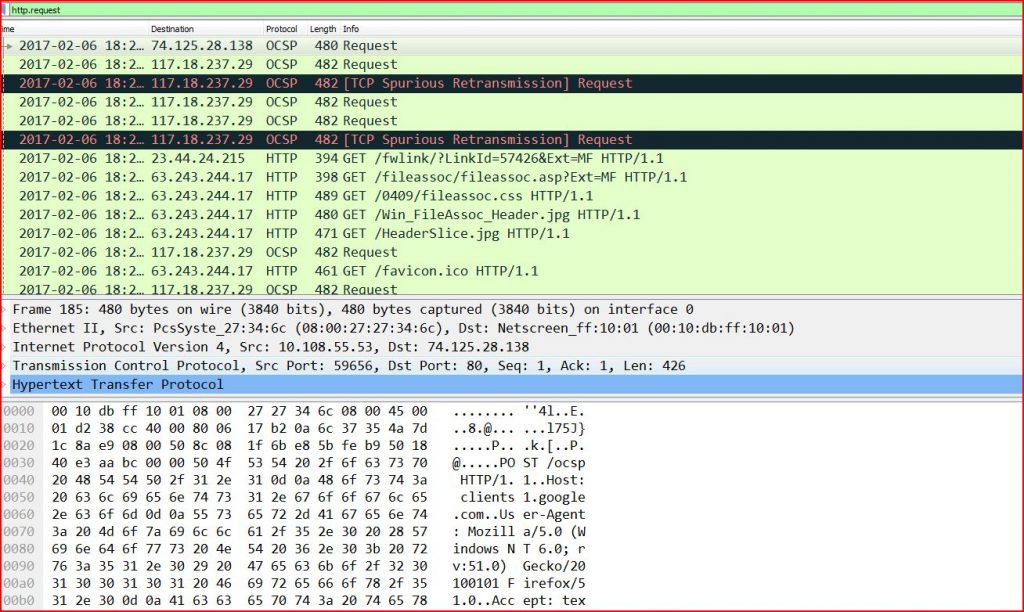
ASSOCIATED URLS:
2017-02-06 18:24:34 74.125.28.138 OCSP 480 Request
2017-02-06 18:24:34 117.18.237.29 OCSP 482 Request
2017-02-06 18:24:35 117.18.237.29 OCSP 482 Request
2017-02-06 18:24:35 117.18.237.29 OCSP 482 [TCP Spurious Retransmission] Request
2017-02-06 18:24:37 23.44.24.215 HTTP 394 GET /fwlink/?LinkId=57426&Ext=MF HTTP/1.1
2017-02-06 18:24:41 63.243.244.17 HTTP 398 GET /fileassoc/fileassoc.asp?Ext=MF HTTP/1.1
2017-02-06 18:24:42 63.243.244.17 HTTP 489 GET /0409/fileassoc.css HTTP/1.1
2017-02-06 18:24:42 63.243.244.17 HTTP 480 GET /Win_FileAssoc_Header.jpg HTTP/1.1
2017-02-06 18:24:49 63.243.244.17 HTTP 471 GET /HeaderSlice.jpg HTTP/1.1
2017-02-06 18:24:49 117.18.237.29 OCSP 482 Request
2017-02-06 18:24:50 63.243.244.17 HTTP 461 GET /favicon.ico HTTP/1.1
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [06 Feb 2017] – [HSBC Payment.rar] 638 KB (653,721 bytes)
- 7433-1486351279-378833.eml 52.0 KB (53,248 bytes)
- HSBC_256474775883748848384939_PDF.jar 251 KB (257,995 bytes)
- Hsbc.pcapng 243 KB (249,084 bytes)
