
[07 Mar 2017] – [Fedex Shipment Malware] – SUBJECT : [Fedex Shipment]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Fedex Shipment”.
ASSOCIATED FILES:
ZIP archive of the malware: [07 Mar 2017] – [Fedex.rar] 1.18 MB (1,245,516 bytes)
- mail for blog3294-1488764094-552077.eml 439 KB (449,830 bytes)
- mailing label.zip 322 KB (330,186 bytes)
- fedex.pcapng 798 KB (817,724 bytes)
THE EMAIL:
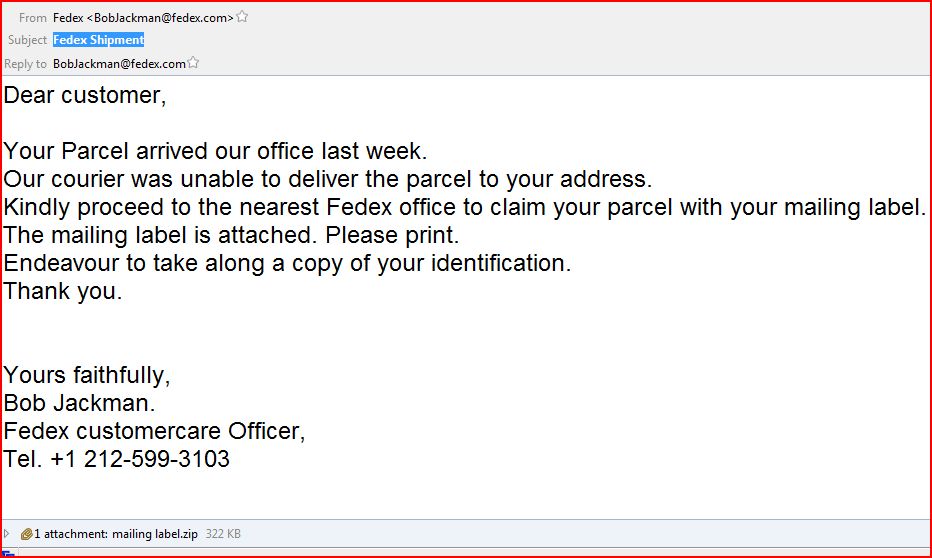
EMAIL DATA:
Reply-To: <BobJackman@fedex.com>
From: Fedex <BobJackman@fedex.com>
Subject: Fedex Shipment
Date: Wed, 1 Mar 2017 21:15:02 -0800
MIME-Version: 1.0
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2600.0000
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2600.0000
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.6
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: attachment mailing label.zip blocked because of filter
rule: ZIP$ action: REJECT
X-KORUMAIL-QueueId: 3294-1488764094-552077
Content-Type: multipart/mixed;
THE ATTACHMENT:
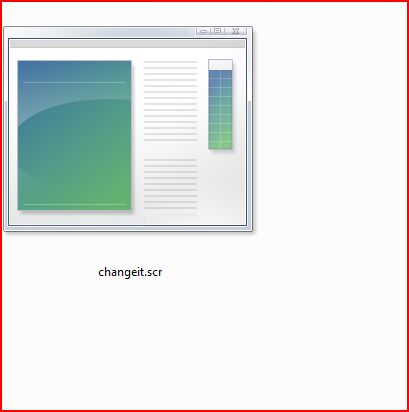
EXTRACTED FILE DETAILS:

File Name : mailing label.zip 322 KB (330,186 bytes)
MD5 hash : CEC6A1C01807A61D177A591482F3B728
SHA1 hash : 4C701C8FF243B01CD90B22D77337D8FBF76BA9BB
SHA256 hash : 204A19BF280F0ADC8A2D2FB3E4F6F1CCB5EF0CBC671C06F574DD065C7F9D1772
File Name : changeit.scr
MD5 hash : BB168565FF6B6C09265FC18BD86BA27E
SHA1 hash : D0D25E65829B356BCF0995DF48948F0D3330B9D1
SHA256 hash : 0244618C5C547315F22712C71E30CC910404E277D683293C062E88E7694B3160
TRAFFIC:
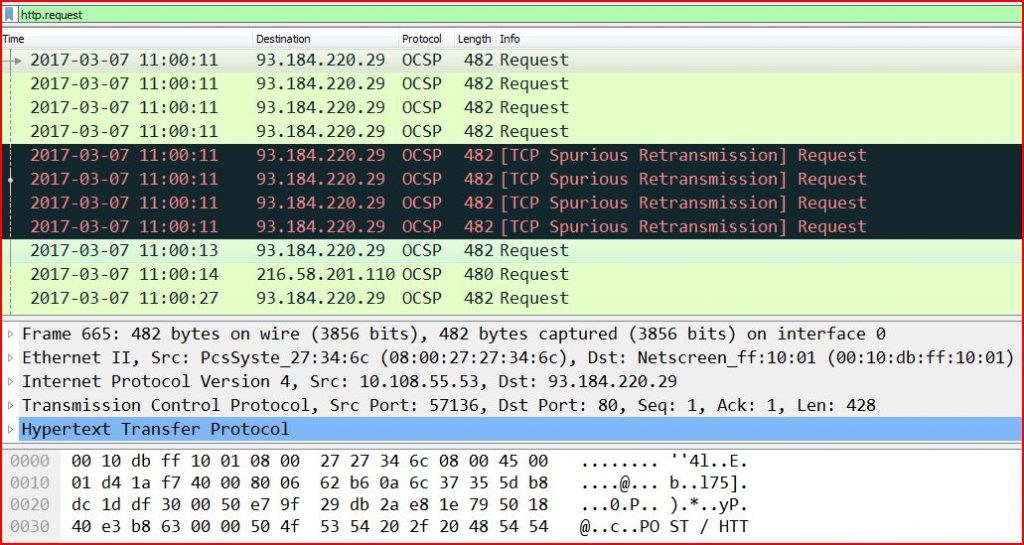
ASSOCIATED URLS:
2017-03-07 11:00:11 93.184.220.29 OCSP 482 Request
2017-03-07 11:00:11 93.184.220.29 OCSP 482 Request
2017-03-07 11:00:11 93.184.220.29 OCSP 482 Request
2017-03-07 11:00:11 93.184.220.29 OCSP 482 Request
2017-03-07 11:00:11 93.184.220.29 OCSP 482 [TCP Spurious Retransmission] Request
2017-03-07 11:00:11 93.184.220.29 OCSP 482 [TCP Spurious Retransmission] Request
2017-03-07 11:00:11 93.184.220.29 OCSP 482 [TCP Spurious Retransmission] Request
2017-03-07 11:00:11 93.184.220.29 OCSP 482 [TCP Spurious Retransmission] Request
2017-03-07 11:00:13 93.184.220.29 OCSP 482 Request
2017-03-07 11:00:14 216.58.201.110 OCSP 480 Request
VALKYRIE FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=d0d25e65829b356bcf0995df48948f0d3330b9d1
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [07 Mar 2017] – [Fedex.rar] 1.18 MB (1,245,516 bytes)
- mail for blog3294-1488764094-552077.eml 439 KB (449,830 bytes)
- mailing label.zip 322 KB (330,186 bytes)
- fedex.pcapng 798 KB (817,724 bytes)
