
[09 Feb 2017] – [Exxon Mobil Malware] – SUBJECT : [ExxonMobile Introduction Letter]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “ExxonMobile Introduction Letter”.
ASSOCIATED FILES:
ZIP archive of the malware: [09 Feb 2017] – [Exxon Mobil.rar] 3.28 MB (3,444,308 bytes)
15134-1486626736-950754.eml 249 KB (255,594 bytes)
Exxon malware.pcapng 3.18 MB (3,345,344 bytes)
HC CEMEA MEA KSA BA SCM.exe 275 KB (282,296 bytes)
THE EMAIL:
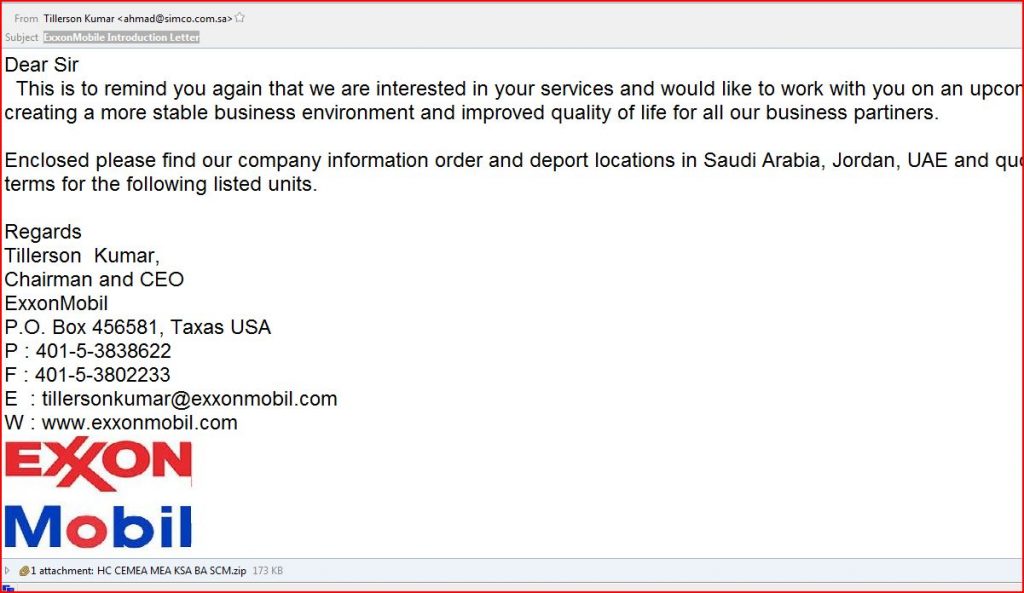
EMAIL DATA:
From: Tillerson Kumar <ahmad@simco.com.sa>
Subject: ExxonMobile Introduction Letter
Date: Wed, 8 Feb 2017 23:51:20 -0800
MIME-Version: 1.0
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2600.0000
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2600.0000
X-AntiAbuse: This header was added to track abuse, please include it with any abuse report
X-AntiAbuse: Primary Hostname – host.afi.com.sa
X-AntiAbuse: Original Domain – dentaskagit.com.tr
X-AntiAbuse: Originator/Caller UID/GID – [47 12] / [47 12]
X-AntiAbuse: Sender Address Domain – simco.com.sa
X-Get-Message-Sender-Via: host.afi.com.sa: authenticated_id:emmanuel.calinisan@afi.com.sa
X-Authenticated-Sender: host.afi.com.sa: emmanuel.calinisan@afi.com.sa
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.5
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: attachment HC CEMEA MEA KSA BA SCM.zip blocked because of
filter rule: .zip$ action: REJECT
THE ATTACHMENT:
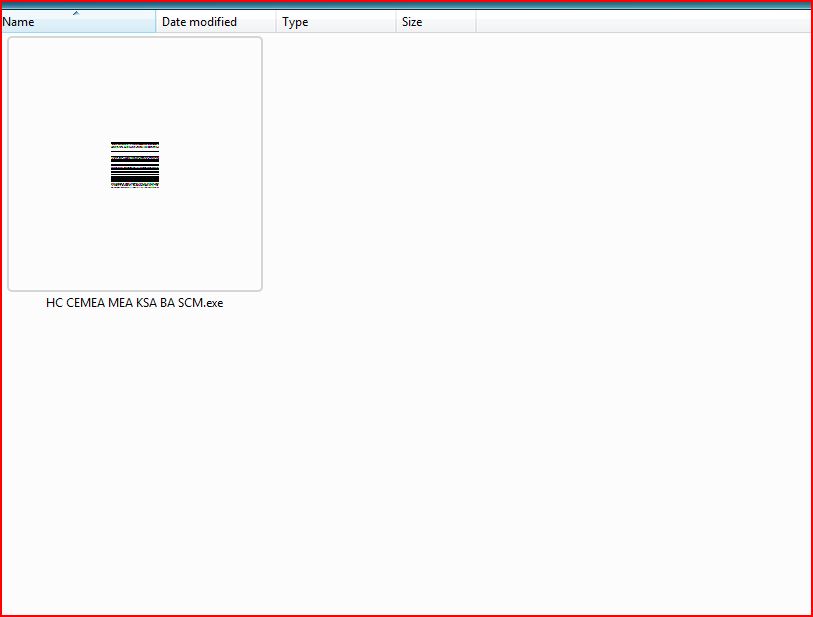

EXTRACTED FILE DETAILS:
File Name : HC CEMEA MEA KSA BA SCM.zip 173 KB (177,399 bytes)
MD5 hash : 56D7A9AD3815602351EC9DA0A7731E2B
SHA1 hash : FEEEE05E8399DDD262A9CC9F1EE4BA44A94F428F
SHA256 hash : 2AF0DEFCD5F628E0731C0515F3900AF9F088BD416FC5B2BC8A7B2A2B56312BD1
File Name : HC CEMEA MEA KSA BA SCM.exe 282,296 Bytes
MD5 hash : 914AF4A9D25499012C343B0B9FF214D6
SHA1 hash : F90AE26E206A2234B0777E02629949A450A09271
SHA256 hash : 6D128FC9602E245D1635AC61CDF9D41BF786BCD3BC2BEF7FDBDAA93D3489BDC7
TRAFFIC:
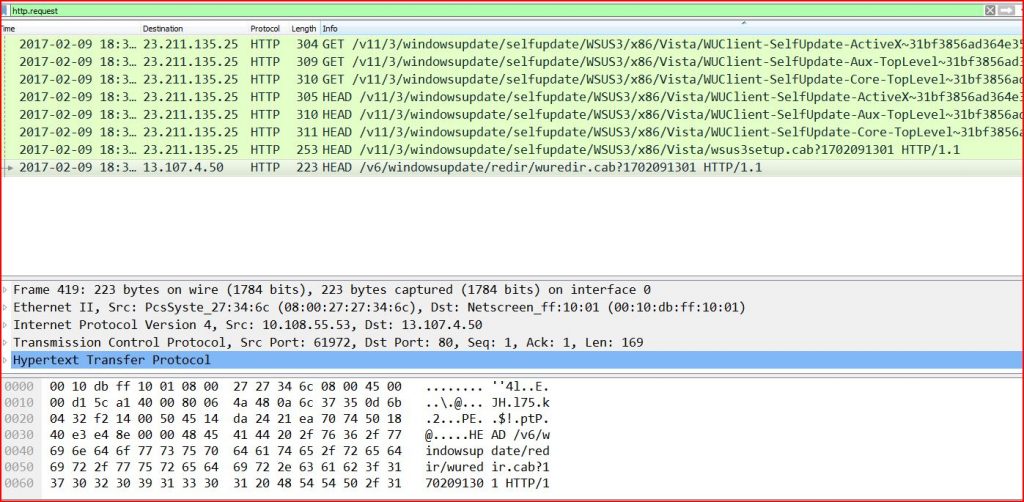
ASSOCIATED URLS:
2017-02-09 18:31:24 23.211.135.25 HTTP 304 GET /v11/3/windowsupdate/selfupdate/WSUS3/x86/Vista/WUClient-SelfUpdate-ActiveX~31bf3856ad364e35~x86~~7.6.7600.256.cab?1702091301 HTTP/1.1
2017-02-09 18:31:24 23.211.135.25 HTTP 309 GET /v11/3/windowsupdate/selfupdate/WSUS3/x86/Vista/WUClient-SelfUpdate-Aux-TopLevel~31bf3856ad364e35~x86~~7.6.7600.256.cab?1702091301 HTTP/1.1
2017-02-09 18:31:24 23.211.135.25 HTTP 310 GET /v11/3/windowsupdate/selfupdate/WSUS3/x86/Vista/WUClient-SelfUpdate-Core-TopLevel~31bf3856ad364e35~x86~~7.6.7600.256.cab?1702091301 HTTP/1.1
2017-02-09 18:31:24 23.211.135.25 HTTP 305 HEAD /v11/3/windowsupdate/selfupdate/WSUS3/x86/Vista/WUClient-SelfUpdate-ActiveX~31bf3856ad364e35~x86~~7.6.7600.256.cab?1702091301 HTTP/1.1
2017-02-09 18:31:24 23.211.135.25 HTTP 310 HEAD /v11/3/windowsupdate/selfupdate/WSUS3/x86/Vista/WUClient-SelfUpdate-Aux-TopLevel~31bf3856ad364e35~x86~~7.6.7600.256.cab?1702091301 HTTP/1.1
2017-02-09 18:31:24 23.211.135.25 HTTP 311 HEAD /v11/3/windowsupdate/selfupdate/WSUS3/x86/Vista/WUClient-SelfUpdate-Core-TopLevel~31bf3856ad364e35~x86~~7.6.7600.256.cab?1702091301 HTTP/1.1
2017-02-09 18:31:20 23.211.135.25 HTTP 253 HEAD /v11/3/windowsupdate/selfupdate/WSUS3/x86/Vista/wsus3setup.cab?1702091301 HTTP/1.1
2017-02-09 18:31:13 13.107.4.50 HTTP 223 HEAD /v6/windowsupdate/redir/wuredir.cab?1702091301 HTTP/1.1
VALKYRIE LINK FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=f90ae26e206a2234b0777e02629949a450a09271
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [09 Feb 2017] – [Exxon Mobil.rar] 3.28 MB (3,444,308 bytes)
- 15134-1486626736-950754.eml 249 KB (255,594 bytes)
- Exxon malware.pcapng 3.18 MB (3,345,344 bytes)
- HC CEMEA MEA KSA BA SCM.exe 275 KB (282,296 bytes)
