
[23 Feb 2017] – [DHL Receipt Malware] – SUBJECT : [Re:#AWB details for delivery of shipping documents]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Re:#AWB details for delivery of shipping documents”.
ASSOCIATED FILES:
ZIP archive of the malware: [23 Feb 2017] – [DHL receipt malware.rar] 331 KB (339,090 bytes)
- 30038-1486475362-108002.eml 210 KB (215,293 bytes)
- balance payment.jar 134 KB (138,228 bytes)
- receipt.pcapng 151 KB (154,928 bytes)
THE EMAIL:

EMAIL DATA:
Subject: [PHISHING]Re:#AWB details for delivery of shipping documents
From: Dhl Delivery <joyce@portoworld.pt>
Date: Thu, 14 Jul 2016 03:02:35 +0300
Message-Id: <E1bNU6t-000Ezz-Ge@fosamax.yoafrica.com>
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.5
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: Phishing attack
X-Envelope-Sender: test@pala.com
X-KORUMAIL-QueueId: 30038-1486475362-108002
Content-Type: multipart/mixed;
THE ATTACHMENT:
EXTRACTED FILE DETAILS:
File Name : balance payment.jar
MD5 hash :12DC2EB22608E7B3C057AB9BEEA8C9FE
SHA1 hash : 043944CD824547B29BDA42B26372283DF31641A1
SHA256 hash : 303FB9FD7425F59CB83B1325206D1C58AF8CCEA15ADC99558B0B0BE27862F245
File Name : IkjL.ayn
MD5 hash : 40F6D66E84FA7E073B3BAB8BD5621D6D
SHA1 hash : CEBD191FE96AB545BC28DB2AE1BA85D6076DAC4B
SHA256 hash : 9E40CC29CD227051E97068BC0EBF561F9FCDA8BF1E72407EF4E6E17F7F773C07
TRAFFIC:
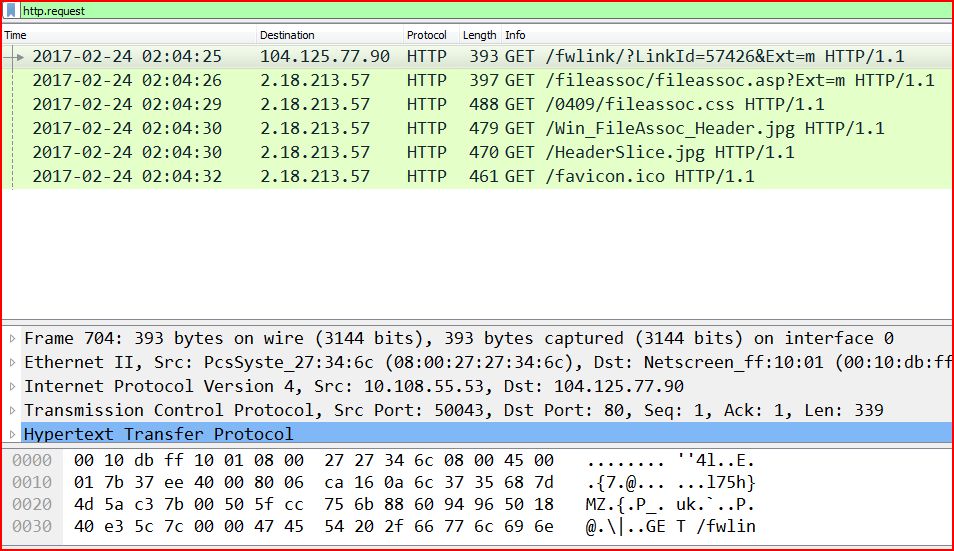
ASSOCIATED URLS:
2017-02-24 02:04:25 104.125.77.90 HTTP 393 GET /fwlink/?LinkId=57426&Ext=m HTTP/1.1
2017-02-24 02:04:26 2.18.213.57 HTTP 397 GET /fileassoc/fileassoc.asp?Ext=m HTTP/1.1
2017-02-24 02:04:29 2.18.213.57 HTTP 488 GET /0409/fileassoc.css HTTP/1.1
2017-02-24 02:04:30 2.18.213.57 HTTP 479 GET /Win_FileAssoc_Header.jpg HTTP/1.1
2017-02-24 02:04:30 2.18.213.57 HTTP 470 GET /HeaderSlice.jpg HTTP/1.1
2017-02-24 02:04:32 2.18.213.57 HTTP 461 GET /favicon.ico HTTP/1.1
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [23 Feb 2017] – [DHL receipt malware.rar] 331 KB (339,090 bytes)
- 30038-1486475362-108002.eml 210 KB (215,293 bytes)
- balance payment.jar 134 KB (138,228 bytes)
- receipt.pcapng 151 KB (154,928 bytes)
