
[21 Dec 2016] –[Dec Month Malware]-SUBJECT:[Dec Month Bill Details]
Comodo Threat Research Labs (CTRL) identified a new phishing email attack that contains a malware file attachment. The malware with subject titled: “Dec Month Bill Details” is targeted at email users.
Malware authors have created a new type of JavaScript file malware named as “Dec Month” malware.
ASSOCIATED FILES:
ZIP archive of the malware: [21 Dec 2016] – [Dec Month Malware] 577.156 kb (577,156 bytes)
- 9212-1482290913-596139.eml (12,479 bytes)
- DEC731230.js (24,005 bytes)
- brvrRr1.dll (270,336 bytes)
- brvrRr1 (270,336 bytes)
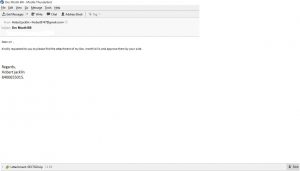
Below is an image of the “Dec Month Bill Details” email. The targeted victim receives an email with the following message:
Dear sir ,
Kindly requested to you to please find the attachment of my Dec. month bills and approve them by your side .
Regards,
Hobert jacklin
8400655015.
However, there is an encrypted script running behind the scenes which stays invisible when the infected user opens the mail and the attachment. The malware is designed to download a malicious file on to the infected user’s device which remains unremovable. This could help the cyber criminal track and access data relating to the victim’s identity and credentials.
THE EMAIL:
EMAIL DATA:
Received: from unknown (HELO ?103.233.119.210?) (103.233.119.210)by 0 with SMTP; 21 Dec 2016 03:28:33 -0000
Received-SPF: unknown (0: domain at spf-trusted-fwd1.surgate.net does not designate permitted sender hosts)
MIME-Version: 1.0
From: Hobert jacklin <Hobert6147@gmail.com>
Date: Wed, 21 Dec 2016 08:59:04 +0530
Message-ID: <B1e1a2a8bD56A301cD3BCCcB429349dA18215362c930545286C@mail.gmail.com>
Subject: Dec Month Bill
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.5
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: attachment DEC7620.zip blocked because of filter rule:
.zip$ action: REJECT
Content-Type: multipart/mixed; boundary=a3c61770bd01c559ed0542ab2f64
–a3c61770bd01c559ed0542ab2f64
Content-Type: multipart/alternative; boundary=a3c61770bd01c559e80542ab2f62
–a3c61770bd01c559e80542ab2f62
THE ATTACHMENT:
The attachment is a “.zip file”, which is actually a “.js” JavaScript file.
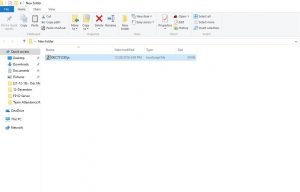
ATTACHMENT AND EXTRACTED .JS FILE:
File Name : [DEC7620.zip] (7,543 Bytes)
SHA1 hash : 6bd3dd2b534a9ab0133d1c27fc310fc49b57cef4
SHA256 hash : 4de9b9fddc00317ad9b4e2969aebc0ab10a0eeffae1f4a919cfb371f3fa3677d
MD5 hash : 11ee65fbe5e59dc815e370536dd7433c
File Name : DEC731230.js (24,005 bytes)
SHA1 hash : 616996daa6f48852846c872d2dc093075022f0d7
SHA256 hash : dc3002a85195f4ea239bb42b09a44203b3c47f824c4f73b90dd94a07618b2b73
MD5 hash : b95caa53d12d92b6c3620233e55b829b
TRAFFIC:
When the email attachment is opened and executed, the file captures the HTTP Request traffic and finds the host of the malicious file URL.
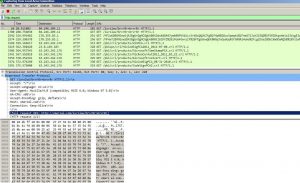
ASSOCIATED URLS:
2016-12-21 11:13:54 10.108.55.53 55002 80 GET /iurslwu?brvrRr=brvrRr HTTP/1.1 96
2016-12-21 11:13:57 84.246.209.11 80 55002 HTTP/1.1 200 OK (text/plain) 380
2016-12-21 11:14:14 10.108.55.53 55027 80 GET /COMODORSACertificationAuthority.crl HTTP/1.1453
2016-12-21 11:14:14 104.16.91.188 80 55027 HTTP/1.1 200 OK (application/x-pkcs7-crl) 456
IMAGES:
FILES DOWNLOADED BY THE INFECTED HOST:
File name : brvrRr1.dll (270,336 bytes)
SHA1 hash : 443df4f1df24893933bf3ce02d82c05caefd8d92
SHA256 hash : 9cea939b5049be272bc2fb494803693d9861f5308c6dfa30be26cffcfa3af8ad
MD5 hash : D3986EDCC13121A8989FE23B49DFEF19
File name : brvrRr1 (270,336 bytes)
SHA1 hash : 0dc92514dc2d547d3eb3aaf38909b6c5296d73bf
SHA256 hash : 7e23755faf5f168c2d12d7fb825683bf42c298ebaa100411aa1573a934330b6a
MD5 hash : 80707AE4B53E4E8F700BED252824463E
VALKYRIE LINK FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=443df4f1df24893933bf3ce02d82c05caefd8d92
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [18 Dec 2016] – [Subscription Malware] 577.156 kb (577,156 bytes)
- 9212-1482290913-596139.eml (12,479 bytes)
- DEC731230.js (24,005 bytes)
- brvrRr1.dll (270,336 bytes)
- brvrRr1 (270,336 bytes)
