
Technical Malware Resource:
Malware authors from the netherworlds have crafted a new version of malware called the Lillian Photo Malware.
ASSOCIATED FILES:
ZIP archive of the malware: [22 Dec 2016] – [ Lillian Photo Malware ] 579.596 kb ( 579,596 bytes)
22271-1482329021-323897.eml (10,413 bytes)
PFE4ACDF.wsf (20,319 bytes)
osEhvowXIB1.dll (274,432 bytes)
osEhvowXIB1 (274,432 bytes)
Below is the sample email. The intended victim user receives a mail with a mail subject as “Photo from Lillian” and a message saying “Hi”. However there is an encrypted script running behind which stays invisible, when the infected user opens the mail and hence the attachment.
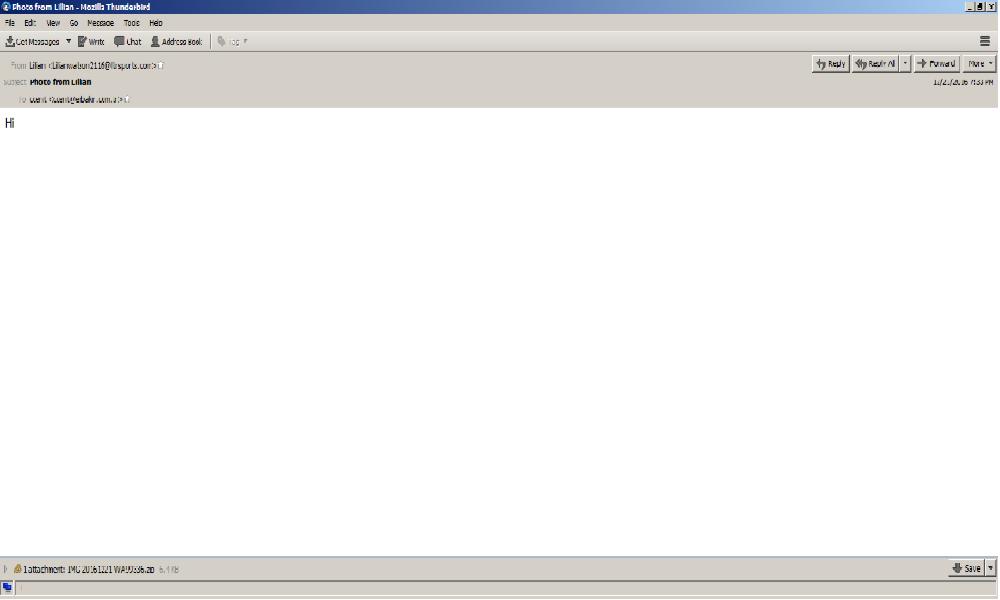
The malware is designed to download a malicious icon on the infected user’s device which remains unremovable. This might help the cyber criminal to track and access the data relating to identity theft and data loss.
EMAIL DATA:
Received: from unknown (HELO static.vdc.vn) (113.165.166.120) by 0
with SMTP; 21 Dec 2016 14:03:42 -0000
Received-SPF: unknown (0: domain at spf-trusted-fwd1.surgate.net does not
designate permitted sender hosts)
MIME-Version: 1.0
From: Lillian <Lillianwatson2116@ftrsports.com>
Date: Wed, 21 Dec 2016 21:03:31 +0700
Message-ID: <5066929189.9702153593098422@ftrsports.com>
Subject: Photo from Lillian
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.5
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: attachment IMG-20161221-WA99336.zip blocked because of
filter rule: .zip$ action: REJECT
Content-Type: multipart/mixed; boundary=4f64daf49d7acc37c80543898344
–4f64daf49d7acc37c80543898344
Content-Type: multipart/alternative; boundary=4f64daf49d7acc37c50543898342
–4f64daf49d7acc37c50543898342
Email Attached “Windows Script” file:
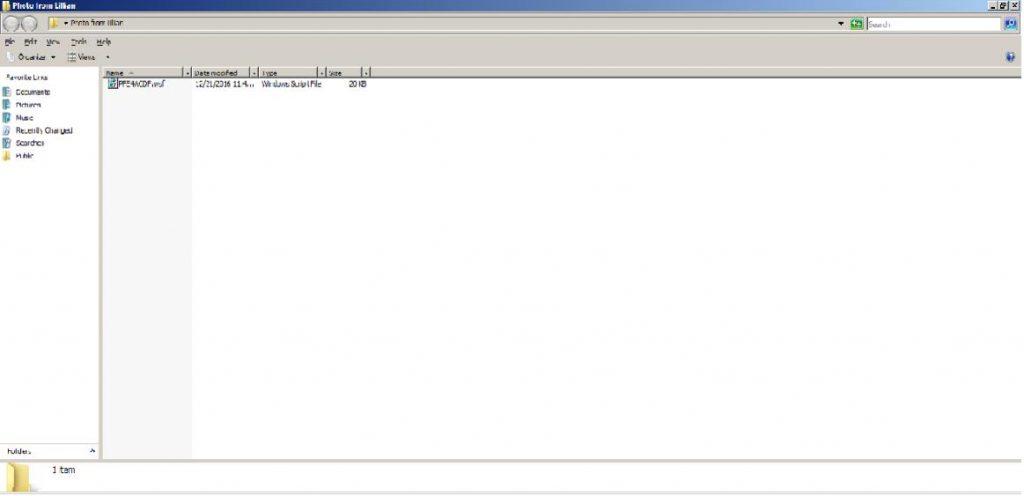
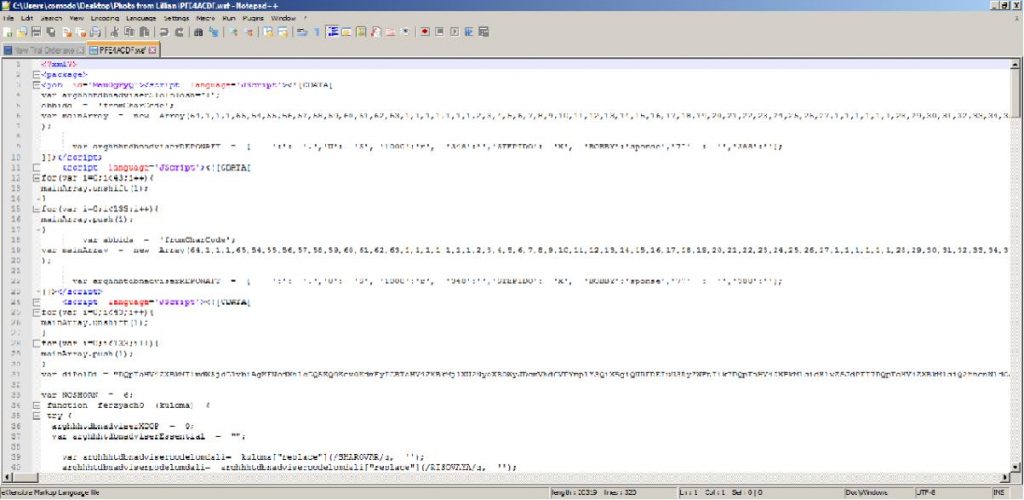
ATTACHMENT AND EXTRACTED .JS FILE:
SHA1 hash : c9c79a9613bf4e1fabf2841ee07f488f6a704fb7
SHA256 hash : f000fb6db46ba9291e80c4beefd51641c0a03a489b59d6260ba9e58bab2c82ed
File Name : IMG-20161221-WA99336.zip ( 6550 Bytes)
SHA1 hash : 5e18c0847a2a47f28bfca81df05a9fe76d004d3f
SHA256 hash : a3468b2d55e2ea804d9a70072fe88835cb11131e081f8fd78cc56dd595bead8f
File Name : PFE4ACDF.wsf ( 20,319 bytes)
Traffic
When the email attachment opened and executed, the file performs to capture the HTTP Request traffic and finds the host of the malicious file.
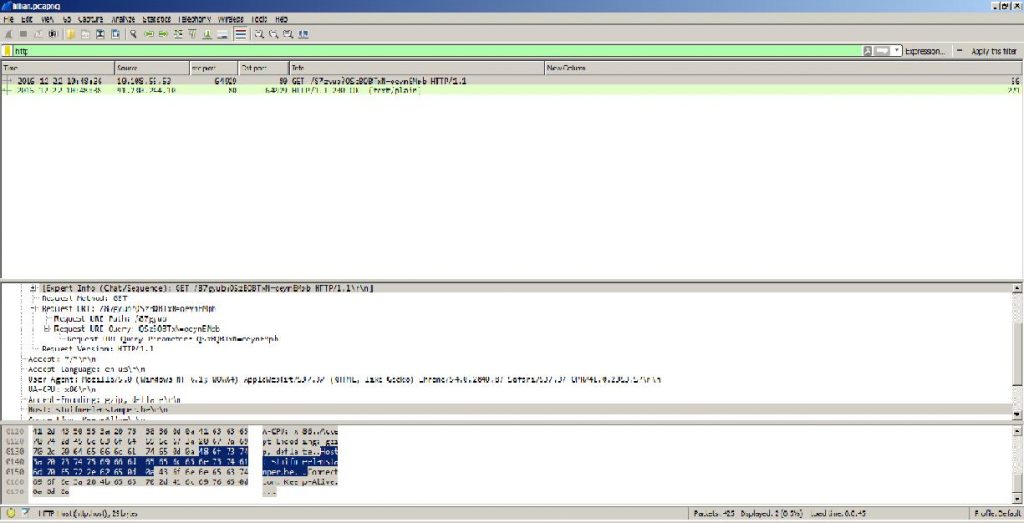
ASSOCIATED URLS:
2016-12-22 10:48:36 10.108.55.53 64929 80 GET /87gyub?QSzBQBTxN=oeynEMpb HTTP/1.1 56
2016-12-22 10:48:38 91.230.244.10 80 64929 HTTP/1.1 200 OK (text/plain) 271
FILES DOWNLOADED BY THE INFECTED HOST:
SHA1 hash : bbb7c4f4fabdbbc870d1d30ef1b29fe12a0901c2
SHA256 hash : 8e451a03d9abf4767b65bc06f2659db11ddeea2049f556191a3f5cd2ba6534e4
File name : osEhvowXIB1.dll (274,432 bytes)
Valkyrie Link : https://valkyrie.comodo.com/get_info?sha1=bbb7c4f4fabdbbc870d1d30ef1b29fe12a0901c2
SHA1 hash : 5dc2d937fe8f090618ae335711fe55b32dc7195e
SHA256 hash : 2974569356b5f22d79af8d0ed9efbdc20a9a4e8dd8831a84f9f6568bc5df3a5a
File name : osEhvowXIB1 (274,432 bytes)
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [22 Dec 2016] – [ Lillian Photo Malware] 579.596 kb (579,596 bytes)
22271-1482329021-323897.eml (10,413 bytes)
PFE4ACDF.wsf (20,319 bytes)
osEhvowXIB1.dll (274,432 bytes)
osEhvowXIB1 (274,432 bytes)
ZIP files are password-protected with the standard password.
Tips from Comodo to prevent malware attacks via Email:
Tip 1: Never get convinced by the display name
Phishing mails often spoofs the display name of an email, so as users do not trust and get convinced by the display name. Cross check with the email address, if you find it suspicious do not open the mail.
Tip 2: Don’t click on the links
If you find a link that is not familiar, do not click to open the link. If you are curious to know about the link, type in the address manually on the address bar and check on it. This will avoid you from getting directed to malicious websites.
Tip 3: Beware of Spelling Mistakes
You should take caution in checking the mail for spelling and grammar mistakes. Authenticated messages are free from such issues.
Tip 4: Avoid Sharing Personal Information
Banks and legitimate companies do not ask personal information through emails. Hence avoid such mails requesting for personal information and do not share any details.
Tip 5: Analyze the signature
Authenticated businesses do provide contact details. Hence it is always better to stay away from such mails.
Tip 6: Do not click on attachments
Phishing emails are known to have malicious attachments. So avoid clicking suspicious attachments that might direct you to a malicious website.
