
[16 Dec 2016] – [Airtel Broadband Malware] – SUBJECT: [Subscription Details]
Comodo Threat Research Labs (CTRL) identified a new phishing email attack with a malware file attachment. It is an “Airtel Broadband Malware” with subject titled: “Subscription Details” targeted at Airtel Broadband customers.
A new type of JavaScript file malware – “Airtel Broadband Malware” has been created by malware authors.
ASSOCIATED FILES:
ZIP archive of the malware: [16 Dec 2016] – [Airtel Broadband Malware] 301 KB (308,318 bytes)
- 26535-1481889541-140181.eml (7,000bytes)
- ~_BA6I5B_~.js (70,000 bytes)
- ogZWC9ed.zk (169,000 bytes)
- rogZWC9ed (169,000 bytes)
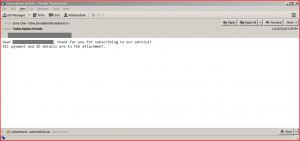
Below is an image of the Subscription Details email. The targeted victim receives an email with the following message:
“Dear xxxxxxxxxxxxx, thank you for subscribing to our service!
All payment and ID details are in the attachment.”
However, there is an encrypted script running behind the scenes which stays invisible when the infected user opens the mail and the attachment. The malware is designed to download a malicious file on to the infected user’s device which remains unremovable. This could help the cyber criminal track and access data relating to the victim’s identity and credentials.
THE EMAIL:
EMAIL DATA:
Received: from unknown (HELO abts-tn-dynamic-084.122.164.122.airtelbroadband.in) (122.164.122.84) by 0 with SMTP; 16 Dec 2016 11:59:02 -0000
Received-SPF: unknown (0: domain at spf-trusted-fwd1.surgate.net does not
designate permitted sender hosts)
From: Erma Cline <Cline.Erma@airtelbroadband.in>
Subject: Subscription Details
Date: Fri, 16 Dec 2016 17:29:09 +0530
MIME-Version: 1.0
Message-Id: <6908884993.439965.05540.server@dentaskagit.com.tr>
Content-Type: multipart/related; boundary=6248592184f8b6e4eb4f6ac181b19b9e
THE ATTACHMENT:
The attachment is a “.zip file”, which is actually a “.js” JavaScript file.
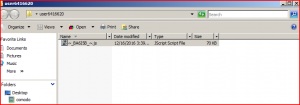
ATTACHMENT AND EXTRACTED .JS FILE:
File Name : [user6416620.zip] (795 Bytes)
SHA256 hash : a36c017341bdd7f8dc64c1cdaf3e81c496a096553f588d8c025a13848dc8c102
SHA1 hash : 12f85e46c4eb2cbc60cf55aff5d3813c2f6464f5
MD5 hash : 74681c4d9584b494c9e67421919e2d60
File Name : ~_BA6I5B_~.js (7000bytes)
SHA256 hash : 7588b5b833d4454e0fb0a79b65323cd880492de70fc78e3b890a43716a04725d
SHA1 hash : 7007b563adceef172b5bb5b59730756b5b1ba332
MD5 hash : a7dd33fdb52216bd963a5ca16085a547
TRAFFIC:
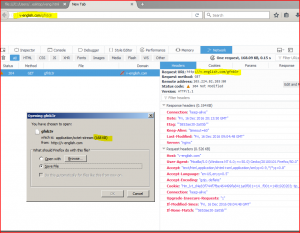
When the email attachment is opened and executed, the file captures the HTTP Request traffic and finds the host of the malicious file URL.
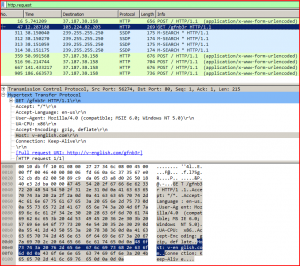
ASSOCIATED URLS:
274 46.486602 10.108.55.53 103.224.82.203 HTTP 352 GET /gfnb3r HTTP/1.1
276 46.601755 103.224.82.203 10.108.55.53 HTTP 253 HTTP/1.1 304 Not Modified
281 46.854649 103.224.82.203 10.108.55.53 HTTP 60 [TCP Spurious Retransmission] Continuation
IMAGES:
FILES DOWNLOADED BY THE INFECTED HOST:
File name : rogZWC9ed.zk (169,000 bytes)
SHA256 hash : 1e2db9b036dc85109e0bfadac229bfdd7a94d9cc75c91d7cf084b3e06c01ae1c
MD5 hash : 3d2673c65c832a9eec1686ef8780c138
SHA 1 hash : 08da52a59efa983c08df72d05b24e6e11f81297
File name : ogZWC9ed (169,000 bytes)
SHA256 hash : ec603e5b385baf25bcf9f766a7c294c19602c06d2d5cf63b064c0e53cefc3460
MD5 hash : d502e809d47db05ae06f9854f04a0079
SHA 1 hash : 05d666dbd4a83cb2ab6da2bef761de31f067b70f
VALKYRIE LINK FOR REFERENCE:
https://valkyrie.comodo.com/get_info?sha1=08da52a59efa983c08df72d05b24e6e11f812979
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [16 Dec 2016] – [Airtel Broadband Malware] 301 KB (308,318 bytes)
- 26535-1481889541-140181.eml (7,000bytes)
- ~_BA6I5B_~.js (70,000 bytes)
- ogZWC9ed.zk (169,000 bytes)
- rogZWC9ed (169,000 bytes
