
[27 June 2017] – [Message Ready with Link Malware] – SUBJECT : [Emailing: 495909959.tiff]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Emailing: 495909959.tiff”.
ASSOCIATED FILES:
ZIP archive of the malware: [27 June 2017] – [ MESSAGE READY WITH LINK MALWARE] – 420 KB (430,080 bytes)
- 94edf201-1d11-43a5-929b-fbf2d13b43de.eml 12.0 KB (12,288 bytes)
- LORLMGFdK2.exe 296 KB (303,104 bytes)
THE EMAIL:
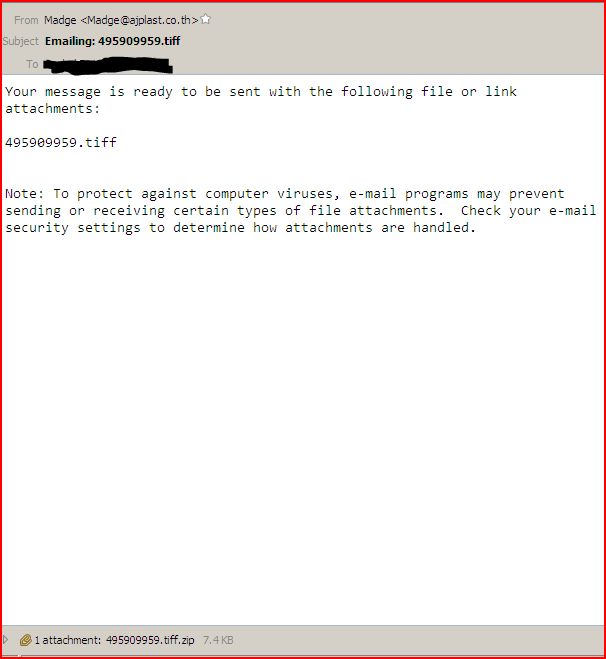
EMAIL DATA:
- From: “Madge” <Madge@ajplast.co.th>
- Subject: Emailing: 495909959.tiff
- Date: Fri, 23 Jun 2017 12:51:21 +0300
- Message-ID: <000c01d1666f$957c2840$c07478c0$@smokintime.com>
- MIME-Version: 1.0
- Content-Type: multipart/mixed;
THE ATTACHMENT:
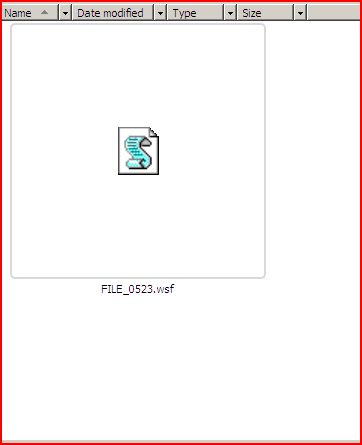
DROPPED FILE:
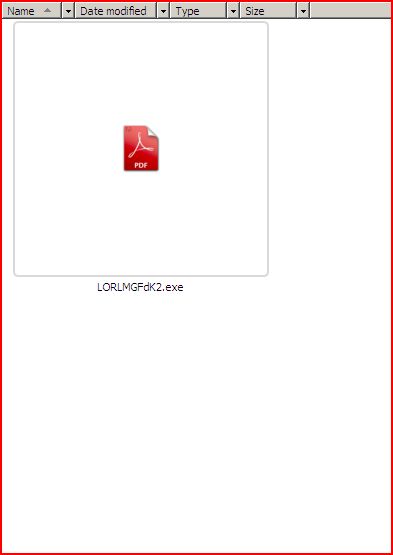
EXTRACTED FILE DETAILS FOR LORLMGFdK2.EXE:
File Name : FILE_0523.wsf 20.0 KB (20,480 bytes)
MD5 hash : ac7d0dc2a92ea3295a9a2ee3eb6ca4d5
SHA1 hash : 81136a38636f25cd9460e1b357da75d4ed975a86
SHA256 hash : 9f9f8eb498a781a9e522f9b2f82e92fc78e5d120646efaaaba03a752629f32df
File Name : LORLMGFdK2.exe 296 KB (303,104 bytes)
MD5 hash : d6ece3d643777677e874e5cbd935f4d0
SHA1 hash : e62d00c1a346d83d50edf982e1b84c01104e1584
SHA256 hash : 8c0fcbbcffd712b6e8147eeab1a11bf1a28b1f85a350e438112abbcbf8664ed2
TRAFFIC:
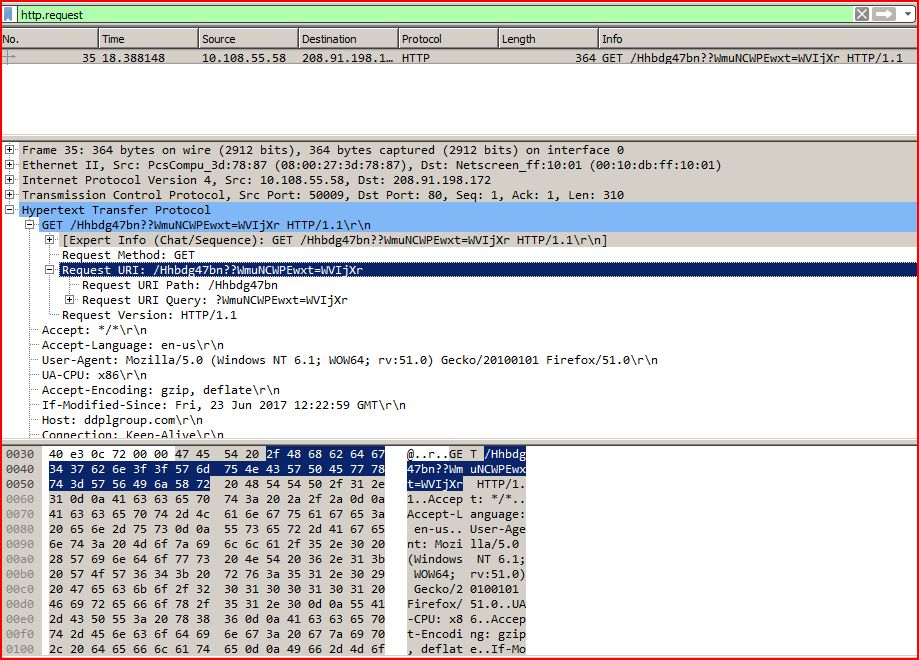
ASSOCIATED URLS:
18.388148 10.108.55.58 208.91.198.172 HTTP 364 GET /Hhbdg47bn??WmuNCWPEwxt=WVIjXr HTTP/1.1
VALKYRIE FOR REFERENCE:
File name:name.exe
https://valkyrie.comodo.com/get_info?sha1=e62d00c1a346d83d50edf982e1b84c01104e1584
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [27 June 2017] – [ MESSAGE READY WITH LINK MALWARE] – 420 KB (430,080 bytes)
- 94edf201-1d11-43a5-929b-fbf2d13b43de.eml 12.0 KB (12,288 bytes)
- LORLMGFdK2.exe 296 KB (303,104 bytes)
