
[16 May 2017] – [Parcel Tracking from DHL Malware] – SUBJECT : [Track Your Parcel ..]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Track Your Parcel ..”.
ASSOCIATED FILES:
ZIP archive of the malware: [07 Apr 2017] – [ DHL-MALWARE] – 3.91 MB (4,100,096 bytes)
7366bef0-ca81-449d-9945-c20005094060 1557 KB (1,597,440 bytes)
name.exe 1.31 MB (1,380,352 bytes)
tmp.exe 1.05 MB (1,114,112 bytes)
THE EMAIL:
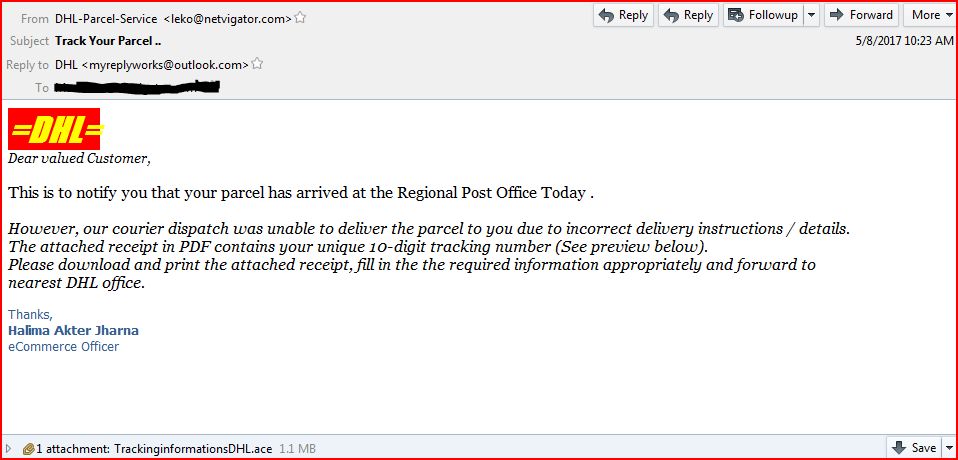
EMAIL DATA:
Received: from localhost (mailsrv01.local [127.0.0.1] by mailsrv01.local (Postfix) with ESMTP id 1F4B93833D23;
Received: from IP-129-104.dataclub.biz (unknown [84.38.129.104]) by mailsrv01.local (Postfix) with ESMTPA id 6D6D83219F35;
Subject: Track Your Parcel
From: “DHL-Parcel-Service ” <leko@netvigator.com>
Reply-To: DHL <myreplyworks@outlook.com>
Message-Id: <20170508050316.6D6D83219F35@mailsrv01.local>
THE ATTACHMENT:
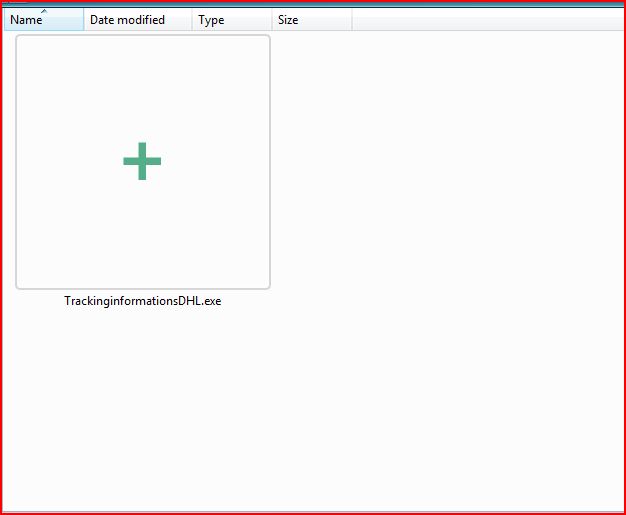
DROPPED FILE:
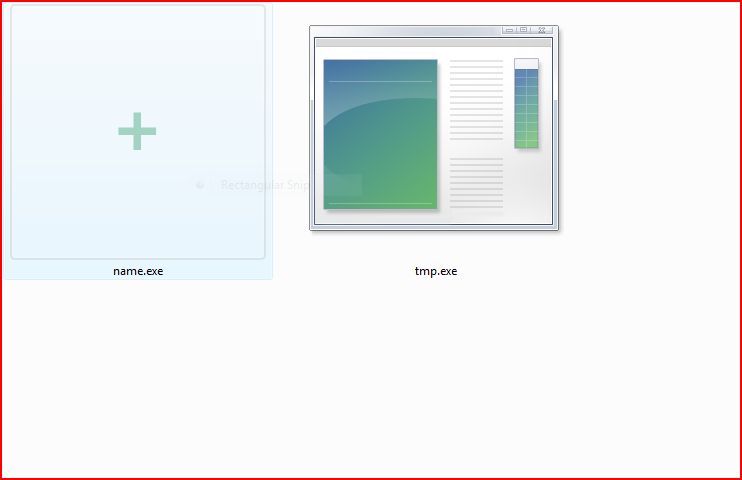
EXTRACTED FILE DETAILS FOR NAME.EXE:
EXTRACTED FILE DETAILS FOR TMP.EXE:
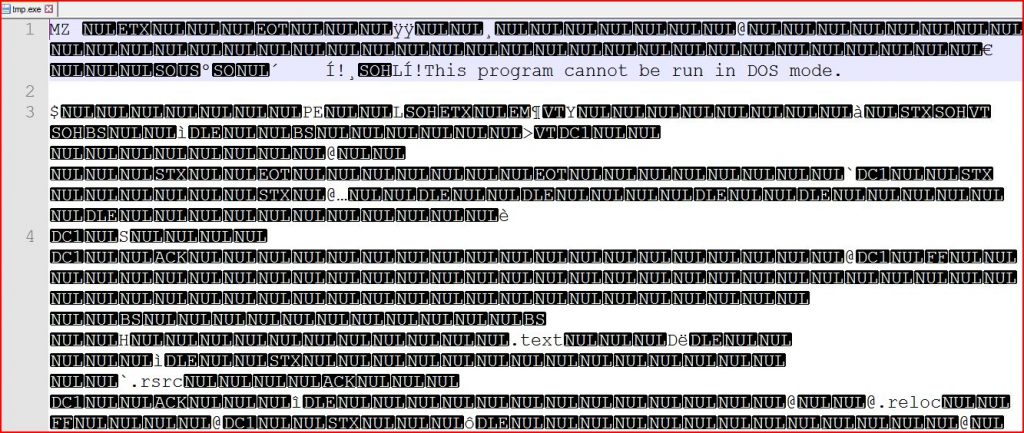
File Name : name.exe 1.31 MB (2,506,752 bytes)
MD5 hash : 399cd851f7e0da668ed215f9a684d561
SHA1 hash : 13257368e4a1201a46d15160b2d8a896c623b60a
SHA256 hash : 399cb409c80a931a87fd501f9ebb48bc33ff0edeacd57bcb1a67880d131f331f
File Name : tmp.exe 491 KB (503,512 bytes)
MD5 hash : ec48eacad852118221648ee14a9f2f2b
SHA1 hash : 559ffbe2161e4a410c2ddc4ac784dffea8ac367b
SHA256 hash : aa127947b0397e21af2706bfb1210fd782629a6420d3b38f02602a4f594d1260
TRAFFIC:
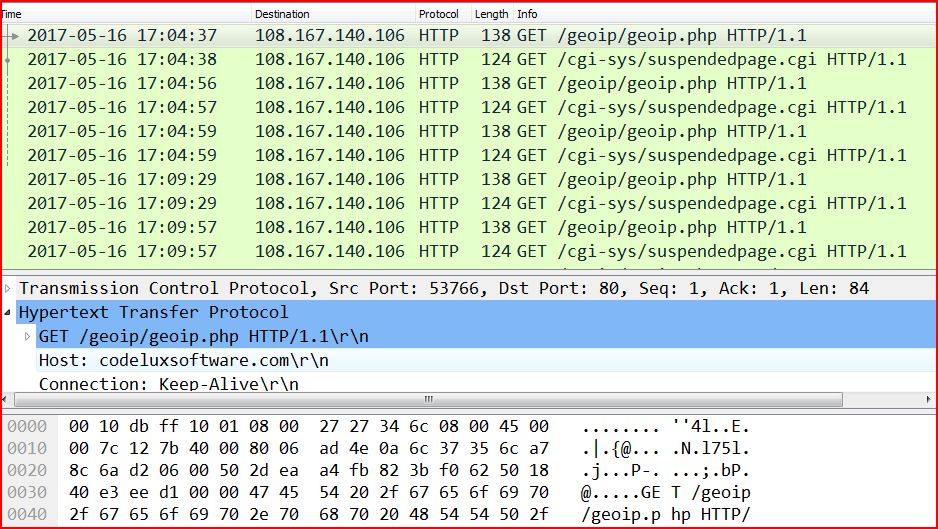
ASSOCIATED URLS:
- 2017-05-16 17:04:37 108.167.140.106 HTTP 138 GET /geoip/geoip.php HTTP/1.1
- 2017-05-16 17:04:38 108.167.140.106 HTTP 124 GET /cgi-sys/suspendedpage.cgi HTTP/1.1
- 2017-05-16 17:04:56 108.167.140.106 HTTP 138 GET /geoip/geoip.php HTTP/1.1
- 2017-05-16 17:04:57 108.167.140.106 HTTP 124 GET /cgi-sys/suspendedpage.cgi HTTP/1.1
- 2017-05-16 17:04:59 108.167.140.106 HTTP 138 GET /geoip/geoip.php HTTP/1.1
- 2017-05-16 17:04:59 108.167.140.106 HTTP 124 GET /cgi-sys/suspendedpage.cgi HTTP/1.1
- 2017-05-16 17:09:29 108.167.140.106 HTTP 138 GET /geoip/geoip.php HTTP/1.1
- 2017-05-16 17:09:29 108.167.140.106 HTTP 124 GET /cgi-sys/suspendedpage.cgi HTTP/1.1
- 2017-05-16 17:09:57 108.167.140.106 HTTP 138 GET /geoip/geoip.php HTTP/1.1
- 2017-05-16 17:09:57 108.167.140.106 HTTP 124 GET /cgi-sys/suspendedpage.cgi HTTP/1.1
VALKYRIE FOR REFERENCE:
File name:name.exe
https://valkyrie.comodo.com/get_info?sha1=13257368e4a1201a46d15160b2d8a896c623b60a
File name:tmp.exe
https://valkyrie.comodo.com/get_info?sha1=559ffbe2161e4a410c2ddc4ac784dffea8ac367b
FINAL NOTES:
Once again, here are the associated files:
ASSOCIATED FILES:
ZIP archive of the malware: [07 Apr 2017] – [ DHL-MALWARE] – 3.91 MB (4,100,096 bytes)
7366bef0-ca81-449d-9945-c20005094060 1557 KB (1,597,440 bytes)
name.exe 1.31 MB (1,380,352 bytes)
tmp.exe 1.05 MB (1,114,112 bytes)
