
[14 Jan 2017] – [Scan Image Malware] – SUBJECT: [New Order]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “New order”.
ASSOCIATED FILES
ZIP archive of the malware: [14 Jan 2017] – [Scan Image Malware] 406 KB (416,315 bytes)
- 12558-1483664655-888841.eml 270 KB (276,506 bytes)
- scan029302image_9303.exe 297 KB (304,640 bytes)
- Scanimage.pcapng 385 KB (394,648 bytes)
THE EMAIL
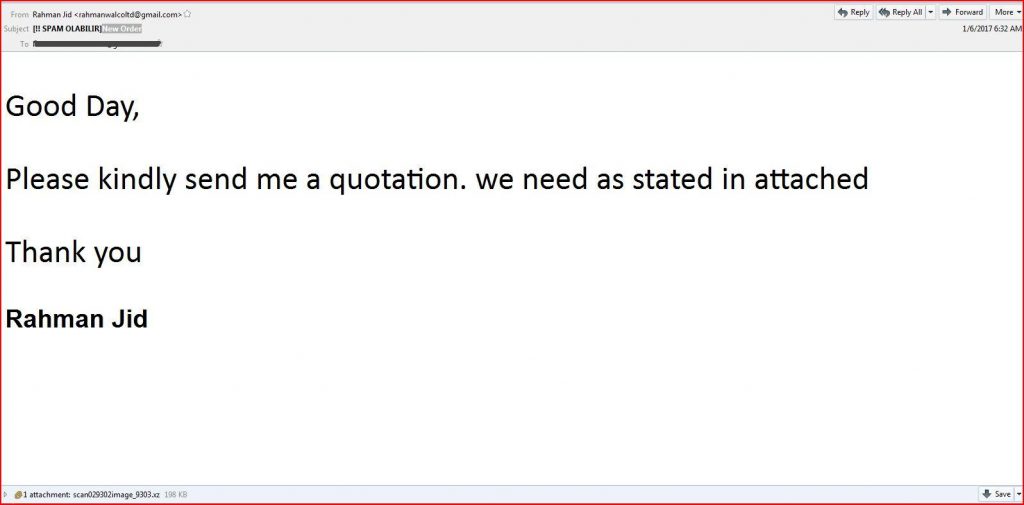
EMAIL DATA
From: Rahman Jid <rahmanwalcoltd@gmail.com>
Date: Fri, 06 Jan 2017 02:02:34 +0100
Return-Path: rahmanwalcoltd@gmail.com
Message-ID: <IP-8-117liRtUvh18cb00000931@IP-8-117.dataclub.biz>
X-OriginalArrivalTime: 06 Jan 2017 01:02:34.0807 (UTC)
FILETIME=[90CB9470:01D267B8]
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.5
X-KORUMAIL-Result: 50.000000 points (Spam)
X-KORUMAIL-Reason: Classified as spam
Content-Type: multipart/mixed;
Content-Transfer-Encoding: quoted-printable
Content-Description: Mail message body
THE ATTACHMENT
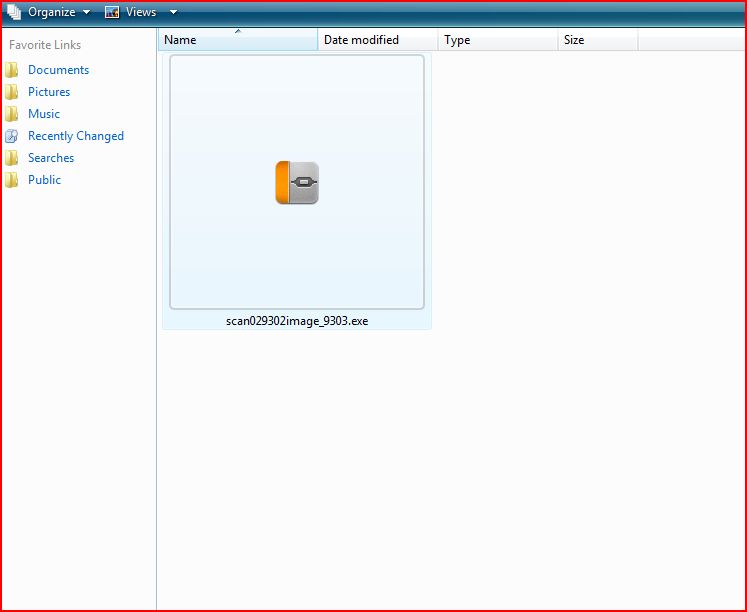
ATTACHMENT AND EXTRACTED FILE
MD5 hash : ADB3DABC577669BFD2E17C79AD849F12
SHA1 hash : 14C8FE7724FA74C61F348502089B3C414A7FBDEC
SHA256 hash : 52EE453AA1FBF0AB8B64793D9C18D7002AD455ABCDF372A70396B5A8A7B3B5E5
File Name : scan029302image_9303 297 KB (304,640 bytes)
TRAFFIC
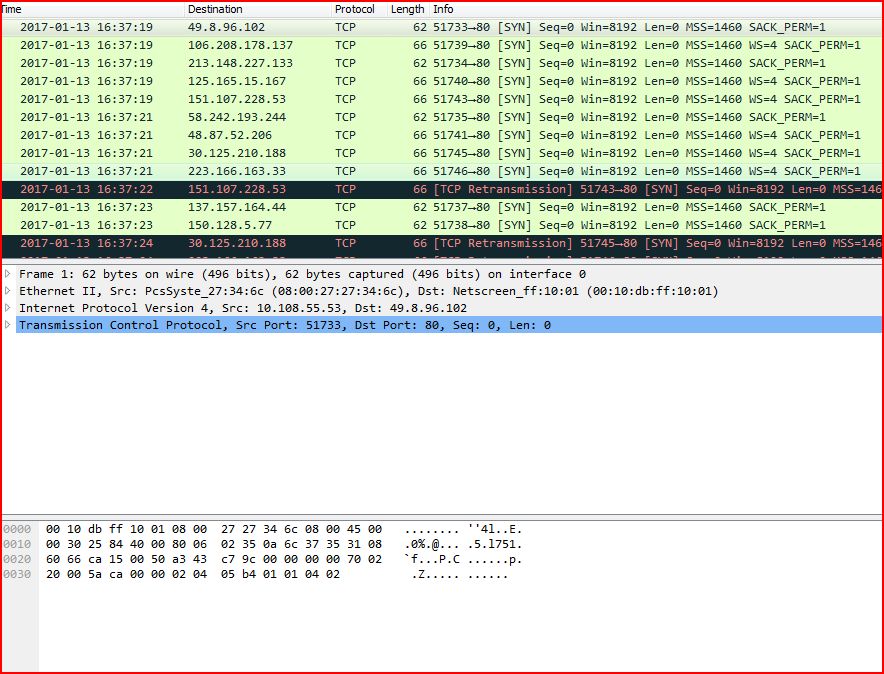
ASSOCIATED URLS
2017-01-13 16:37:19 49.8.96.102 TCP 62 51733→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 SACK_PERM=1
2017-01-13 16:37:19 106.208.178.137 TCP 66 51739→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-13 16:37:19 213.148.227.133 TCP 62 51734→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 SACK_PERM=1
2017-01-13 16:37:19 213.148.227.133 TCP 62 51734→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 SACK_PERM=1
2017-01-13 16:37:19 125.165.15.167 TCP 66 51740→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-13 16:37:19 151.107.228.53 TCP 66 51743→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-13 16:37:21 58.242.193.244 TCP 62 51735→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 SACK_PERM=1
2017-01-13 16:37:21 48.87.52.206 TCP 66 51741→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-13 16:37:21 30.125.210.188 TCP 66 51745→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-13 16:37:21 223.166.163.33 TCP 66 51746→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
2017-01-13 16:37:22 151.107.228.53 TCP 66 [TCP Retransmission] 51743→80 [SYN] Seq=0 Win=8192 Len=0 MSS=1460 WS=4 SACK_PERM=1
VALKYRIE LINK FOR REFERENCE
https://valkyrie.comodo.com/get_info?sha1=14c8fe7724fa74c61f348502089b3c414a7fbdec
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES
ZIP archive of the malware: [14 Jan 2017] – [Scan Image Malware] 406 KB (416,315 bytes)
- 12558-1483664655-888841.eml 270 KB (276,506 bytes)
- scan029302image_9303.exe 297 KB (304,640 bytes)
- Scanimage.pcapng 385 KB (394,648 bytes)
