
[08 Jan 2017] – [Sample Order Malware] – SUBJECT: [Sample Order]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Sample Order”.
ASSOCIATED FILES
ZIP archive of the malware: [08 Jan 2017] – [Sample Order Malware] 944 KB (966,656 bytes)
- 7874-1483824685-83778.eml 420 KB (430,080 bytes)
- Sample Order.exe 443 KB (454,656 bytes)
THE EMAIL
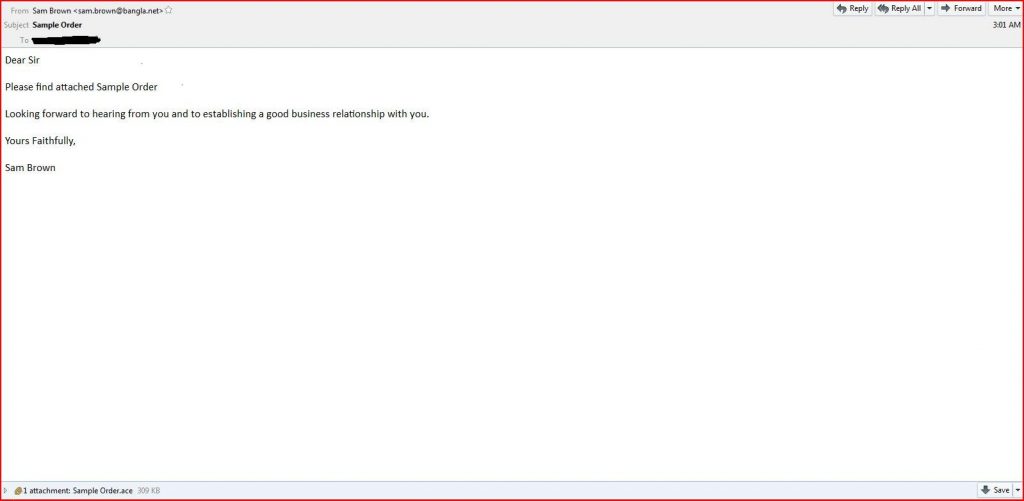
EMAIL DATA
- Received: from unknown (HELO vps2014.synema.nl) (31.3.97.104) by 0
with SMTP; 7 Jan 2017 21:31:26 -0000 - Received-SPF: unknown (0: domain at spf-trusted-fwd1.surgate.net does not
designate permitted sender hosts) - Received: from daniella by vps2014.synema.nl
with local (Exim 4.88) (envelope-from <daniella@vps2014.synema.nl>)
id 1cPyaB-0006UG-TU for esas@esas.com.tr; Sat, 07 Jan 2017 22:31:23 +0100 - Subject: Sample Order
- X-PHP-Script: daniella.nl/img/rfxzetta/www/phpmailer.php for 74.95.99.73
- From: Sam Brown <sam.brown@bangla.net>
- Reply-To:
- MIME-Version: 1.0
- Message-Id: <E1cPyaB-0006UG-TU@vps2014.synema.nl>
- Date: Sat, 07 Jan 2017 22:31:23 +0100
THE ATTACHMENT
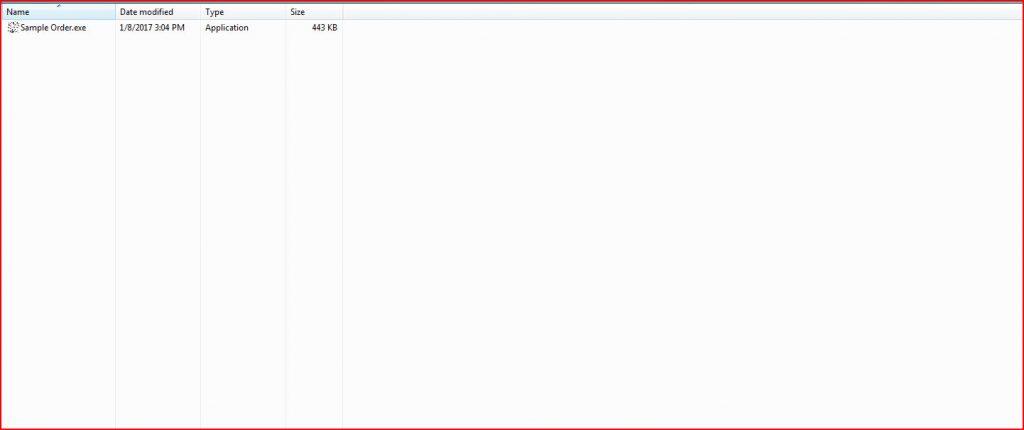

ATTACHMENT AND EXTRACTED .Exe FILE
File Name : sample order.zip 311 KB (319,488 bytes)
MD5 hash : 2C7F3C23876FBD7EC7CC0094E73D6190
SHA1 hash : 30349D20689D737508E78BC7027D9E02114B7108
SHA256 hash : FE63DE5DF3B07B5115F7D2C37B0D6FAB57751CC64B590A33A34417813CF2896A
File Name : sample order exe 443 KB (454,656 bytes)
MD5 hash : 145659494A62324F59D46385F05D3171
SHA1 hash : 213E0AE9A518A9003BF77AB90817A67D6A8B07E6
SHA256 hash :2B68977A6262D40B25DFB0536C265BD82ABF5832F21EB6B8F9BF96171F047E37
TRAFFIC
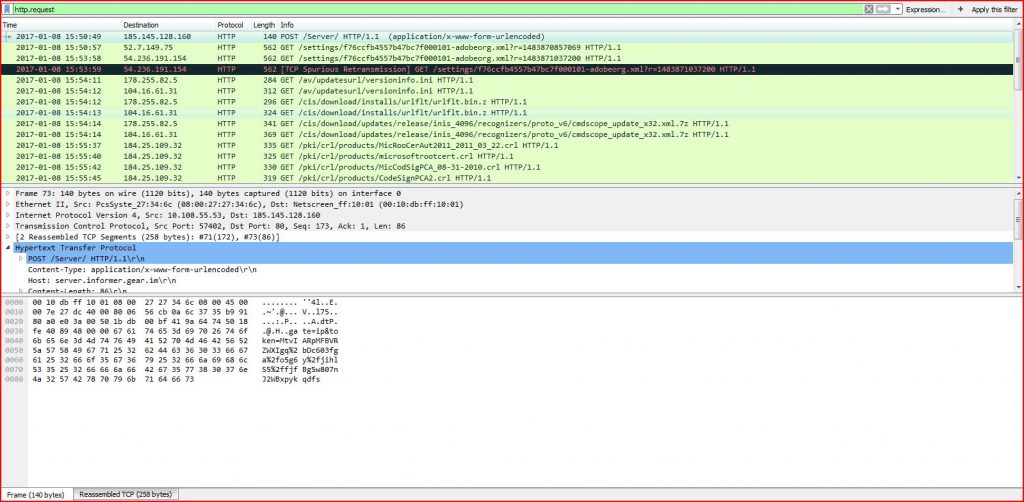
ASSOCIATED URLS:
- 2017-01-08 15:50:49 185.145.128.160 HTTP 140 POST /Server/ HTTP/1.1 (application/x-www-form-urlencoded)
- 2017-01-08 15:50:57 52.7.149.75 HTTP 562 GET /settings/f76ccfb4557b47bc7f000101-adobeorg.xml?r=1483870857069 HTTP/1.1
- 2017-01-08 15:53:58 54.236.191.154 HTTP 562 GET /settings/f76ccfb4557b47bc7f000101-adobeorg.xml?r=1483871037200 HTTP/1.1
- 2017-01-08 15:53:59 54.236.191.154 HTTP 562 [TCP Spurious Retransmission] GET /settings/f76ccfb4557b47bc7f000101-adobeorg.xml?r=1483871037200 HTTP/1.1
- 2017-01-08 15:54:11 178.255.82.5 HTTP 284 GET /av/updatesurl/versioninfo.ini HTTP/1.1
- 2017-01-08 15:54:12 104.16.61.31 HTTP 312 GET /av/updatesurl/versioninfo.ini HTTP/1.1
- 2017-01-08 15:54:12 178.255.82.5 HTTP 296 GET /cis/download/installs/urlflt/urlflt.bin.z HTTP/1.1
- 2017-01-08 15:54:13 104.16.61.31 HTTP 324 GET /cis/download/installs/urlflt/urlflt.bin.z HTTP/1.1
- 2017-01-08 15:54:14 178.255.82.5 HTTP 341 GET /cis/download/updates/release/inis_4096/recognizers/proto_v6/cmdscope_update_x32.xml.7z HTTP/1.1
- 2017-01-08 15:54:14 104.16.61.31 HTTP 369 GET /cis/download/updates/release/inis_4096/recognizers/proto_v6/cmdscope_update_x32.xml.7z HTTP/1.1
- 2017-01-08 15:55:37 184.25.109.32 HTTP 335 GET /pki/crl/products/MicRooCerAut2011_2011_03_22.crl HTTP/1.1
- 2017-01-08 15:55:40 184.25.109.32 HTTP 325 GET /pki/crl/products/microsoftrootcert.crl HTTP/1.1
- 2017-01-08 15:55:42 184.25.109.32 HTTP 330 GET /pki/crl/products/MicCodSigPCA_08-31-2010.crl HTTP/1.1
IMAGES:

FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES
ZIP archive of the malware: [08 Jan 2017] – [Sample Order Malware] 944 KB (966,656 bytes)
- 7874-1483824685-83778.eml 420 KB (430,080 bytes)
- Sample Order.exe 443 KB (454,656 bytes)
