
[03 Jan 2017] – [Software License Malware] – SUBJECT : [Software License]
Comodo Threat Research Labs (CTRL) identified a new phishing email, that contains a malware file, and spread to email user with subject “Software License”.
ASSOCIATED FILES
ZIP archive of the malware: [03 Jan 2017] – [Software License Malware] 128 KB (131,583 bytes)
- 14622-1481572596-769050.eml 6.00 KB (6,152 bytes)
- ~X8L90WS61UC4709Z2VVT02M.wsf 21.1 KB (21,683 bytes)
- Y7X0upJ8Iq25GNJE.zk 149 KB (152,977 bytes)
THE EMAIL
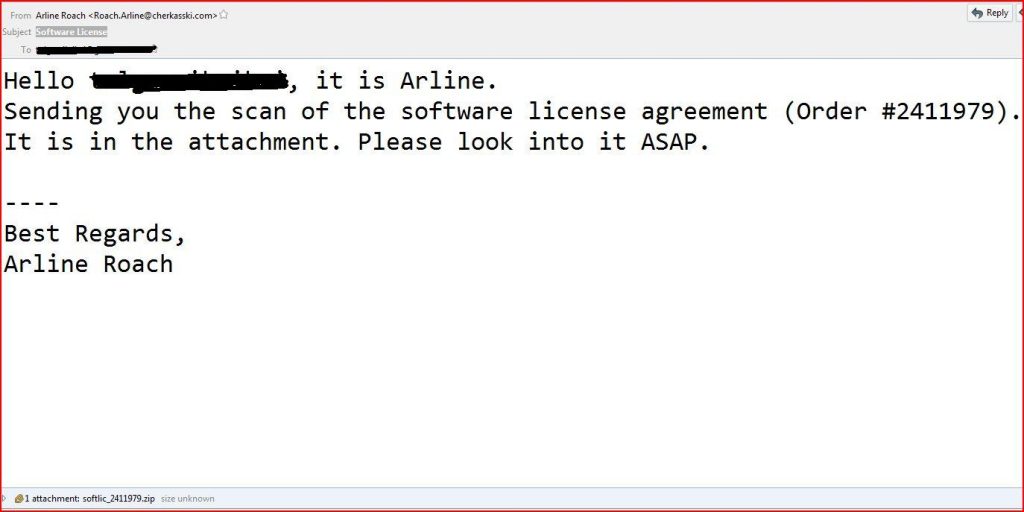
EMAIL DATA
From: Arline Roach <Roach.Arline@cherkasski.com>
Subject: Software License
Date: Tue, 13 Dec 2016 02:56:40 +0700
MIME-Version: 1.0
Message-Id: <9479847701.800340.37611.server@giresun.edu.tr>
X-SMTP-Filter: Korumail SMTP Filter Engine Korumail 6.5
X-KORUMAIL-Result: Miscellaneous filter match
X-KORUMAIL-Reason: Foxhole.Wsf_Zip_1.UNOFFICIAL
Content-Type: multipart/related; boundary=245cf1b3efca3ab38c4e3a7b83f28f12
–245cf1b3efca3ab38c4e3a7b83f28f12
Content-Type: text/plain;
charset=utf-8
Content-Transfer-Encoding: base6
Content-Type: application/zip; name=”softlic_2411979.zip”
Content-Transfer-Encoding: base64
Content-Disposition: attachment; filename=”softlic_2411979.zip”
THE ATTACHMENT
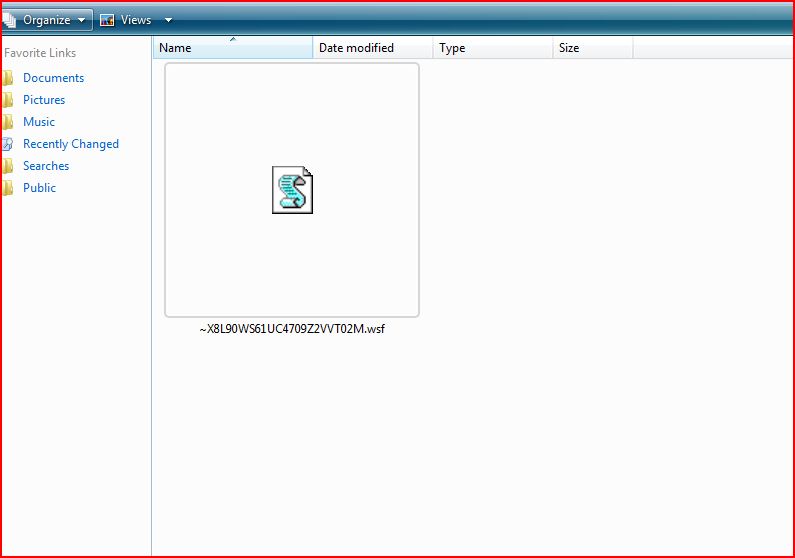
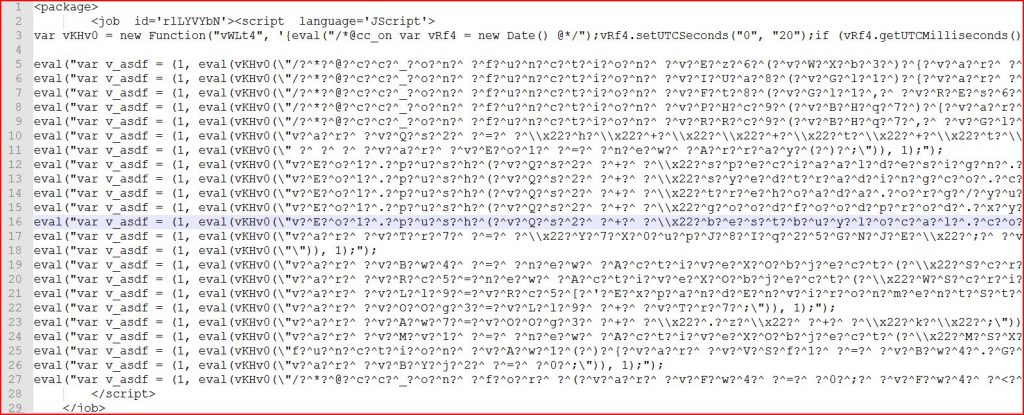
ATTACHMENT AND EXTRACTED .WSF FILE
MD5 hash : 7dd27b45c925c5a7a932a19e4570a73b
SHA1 hash : 4c80f1da2d8d1cac4cee48f2edbb235008cbfbb6
SHA256 hash : c839346e1e6c7cd5f26dd8190ce8d24d210adea2118af37ef4397bf57898bb00
File Name : softlic_2411979.zip 3.51 KB (3,599 bytes)
MD5 hash : 336185795bc2a0b9ca337356a676e7d5
SHA1 hash : 7bcc013205d9fc6bbac05d03af35ab61f637f381
SHA256 hash : 5144270cdcb2ee792af900de1f673e36fed6694145d1e2cbc7441fca29a4d638
File Name : ~X8L90WS61UC4709Z2VVT02M.wsf 21.1 KB (21,683 bytes)
TRAFFIC
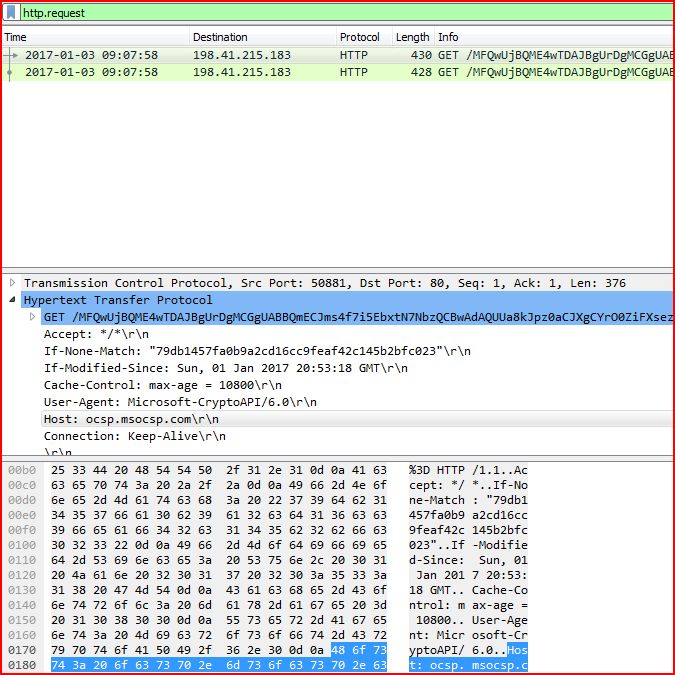
ASSOCIATED URLS
2017-01-03 09:07:58 198.41.215.183 HTTP 430 GET /MFQwUjBQME4wTDAJBgUrDgMCGgUABBQmECJms4f7i5EbxtN7NbzQCBwAdAQUUa8kJpz0aCJXgCYrO0ZiFXsezKUCE1oABasbVc1%2F30qkcksAAQAFqxs%3D HTTP/1.1
2017-01-03 09:07:58 198.41.215.183 HTTP 428 GET /MFQwUjBQME4wTDAJBgUrDgMCGgUABBQmECJms4f7i5EbxtN7NbzQCBwAdAQUUa8kJpz0aCJXgCYrO0ZiFXsezKUCE1oABXWPhcP9WMn4FIcAAQAFdY8%3D HTTP/1.1
IMAGES
FILES DOWNLOADED BY THE INFECTED HOST
MD5 hash : db48e7ba4364f0755b86a90cf6868abe
SHA1 hash : 3f1dfaa8d39ce3323e2617485c7de447a4ad1b06
SHA256 hash : 960221953d73c8389290308eb2121e05349ccf272b62bff36626afbcc900de4f
File name : Y7X0upJ8Iq25GNJE.zk 149 KB (152,977 bytes)
VALKYRIE LINK FOR REFERENCE
https://valkyrie.comodo.com/get_info?sha1=3f1dfaa8d39ce3323e2617485c7de447a4ad1b06
FINAL NOTES
Once again, here are the associated files:
ASSOCIATED FILES
ZIP archive of the malware: [03 Jan 2017] – [Software License Malware] 128 KB (131,583 bytes)
- 14622-1481572596-769050.eml 6.00 KB (6,152 bytes)
- ~X8L90WS61UC4709Z2VVT02M.wsf 21.1 KB (21,683 bytes)
- Y7X0upJ8Iq25GNJE.zk 149 KB (152,977 bytes)
